Tired of Waiting Three Weeks for a PDF?
See findings as we find them. Ask questions as they come up.
Traditional pen tests are a black box — you hand over credentials, wait, and hope the report makes sense. Raxis works differently. With Raxis One, you see findings in real time, chat directly with your testers, and track remediation in one place. Schedule 30 minutes and we’ll show you what a transparent engagement actually looks like.
Years Experience
Average Days To Initial Access
Reaching Crown Jewels
Average data Breach Cost
Why Raxis
Not your typical Penetration Test.
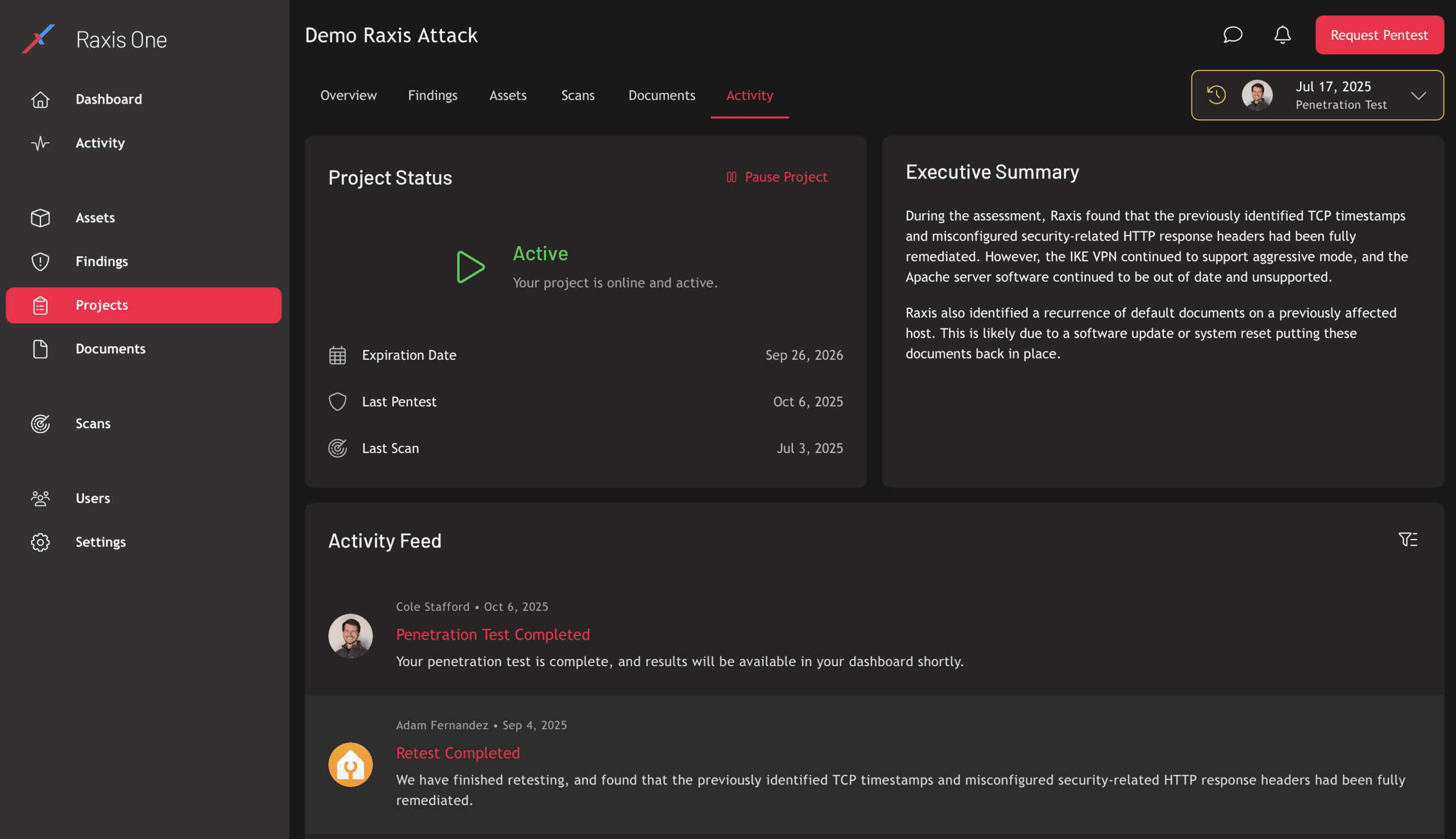
Turn Penetration Testing Into Continuous Defense
Request a live demo to see how Raxis One centralizes your security testing, integrates with your workflow, and delivers actionable intelligence in real time.
Command Your Security Posture with Precision
Raxis One delivers the clarity CISOs need and the depth engineers demand—unifying attack data, analytics, and progress tracking under one secure interface.
15+ Years of Real Breaches
Our human led team has compromised Fortune 500s, critical infrastructure, and everything in between. Our playbooks are forged from thousands of successful engagements—not theory.
See Your Security Through an Attacker’s Eyes
Experience how Raxis One visualizes live penetration test results, so your team can prioritize and remediate threats before they become incidents.
The Problem
Compliance ≠ Security
You’ve passed every audit. Your vulnerability scans are clean. Your security team is confident.
Yet sophisticated attackers breach “compliant” organizations every day. Because compliance tests what you know—adversaries exploit what you don’t.
2024 Breach Statistics
Sources: IBM Cost of a Data Breach Report 2024, Verizon DBIR 2024
Attack Surface Management
We attack from every angle.
External Network Penetration Testing
Breaking in from the internet
Phishing & Social Engineering
Exploiting the human layer
Physical Security Bypass
On-site infiltration
Cloud Infrastructure Attacks
AWS, Azure, GCP exploitation
Insider Threat Simulation
Compromised employee scenarios
Supply Chain Attacks
Third-party compromise paths
Methodology
How we operate.
Our human led penetration testing methodology mirrors real-world adversaries—with the discipline and ethics of professionals.
“Raxis found attack paths that another big name firms missed. Within a week, they had domain admin and demonstrated full compromise of our crown jewels. It was humbling—and exactly what we needed.”