The Benchmark for Penetration Testing Excellence
Why risk a breach? The 2025 Verizon Data Breach Investigations Report reveals critical gaps in fully AI-driven penetration testing
Real Attacks. Real Results. Real Penetration Testing.
Penetration Testing Services
Trusted by startups and enterprises as their penetration test company of choice, we go deeper than scans—blending elite penetration testing expertise with AI powered tools to identify exploitable flaws, prioritize fixes, and deliver audit-ready reports that strengthen your defenses.
Penetration Testing Services
Our security experts simulate realistic attack scenarios across your entire environment to uncover vulnerabilities before attackers do. Every assessment is led by certified ethical hackers using offensive security techniques refined over thousands of engagements.
External Network Penetration Testing
We target your internet-facing infrastructure the way a real attacker would — probing firewalls, services, and public-facing systems for exploitable weaknesses that could give an adversary a foothold into your network.
Penetration Testing as a Service
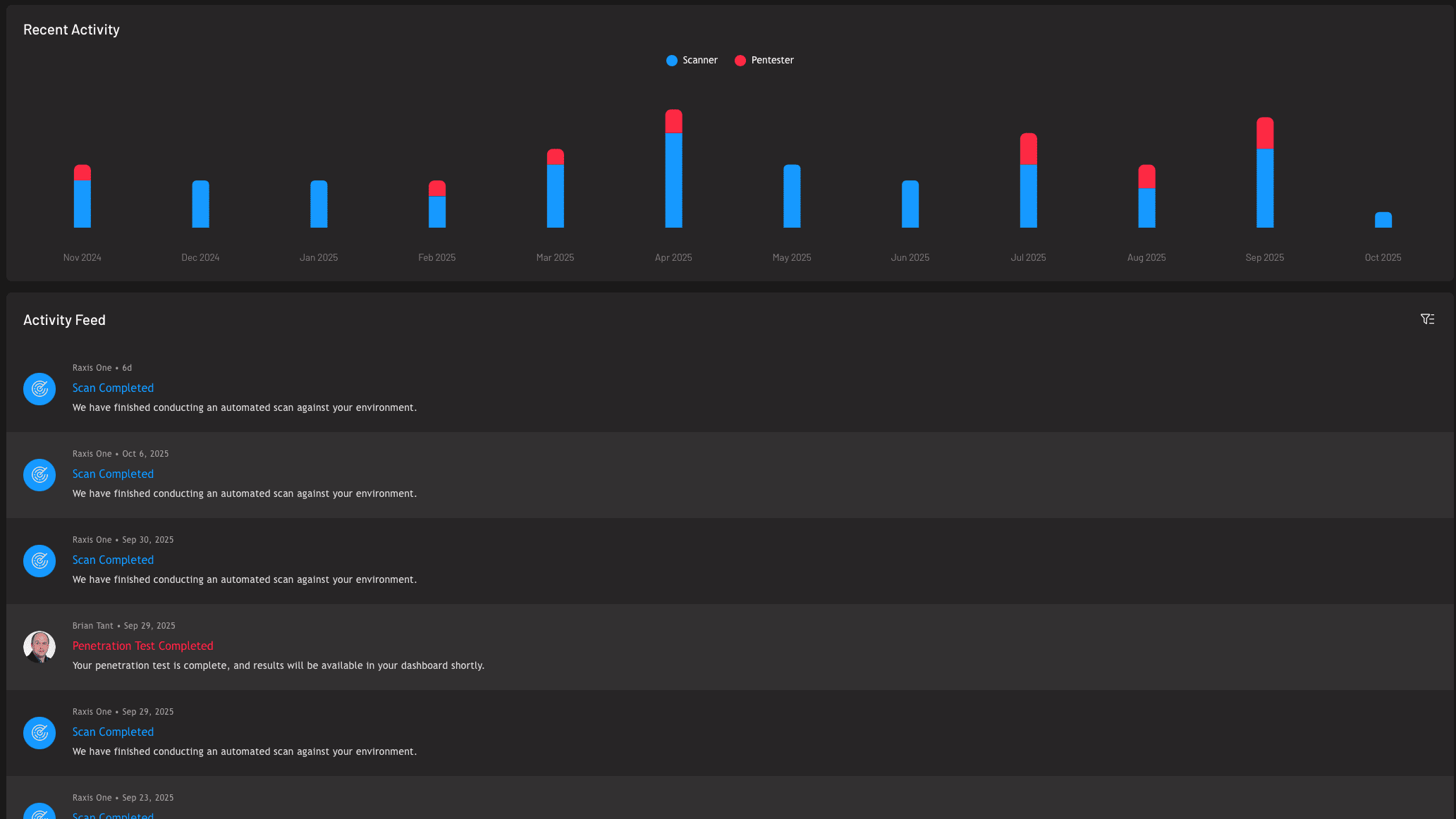
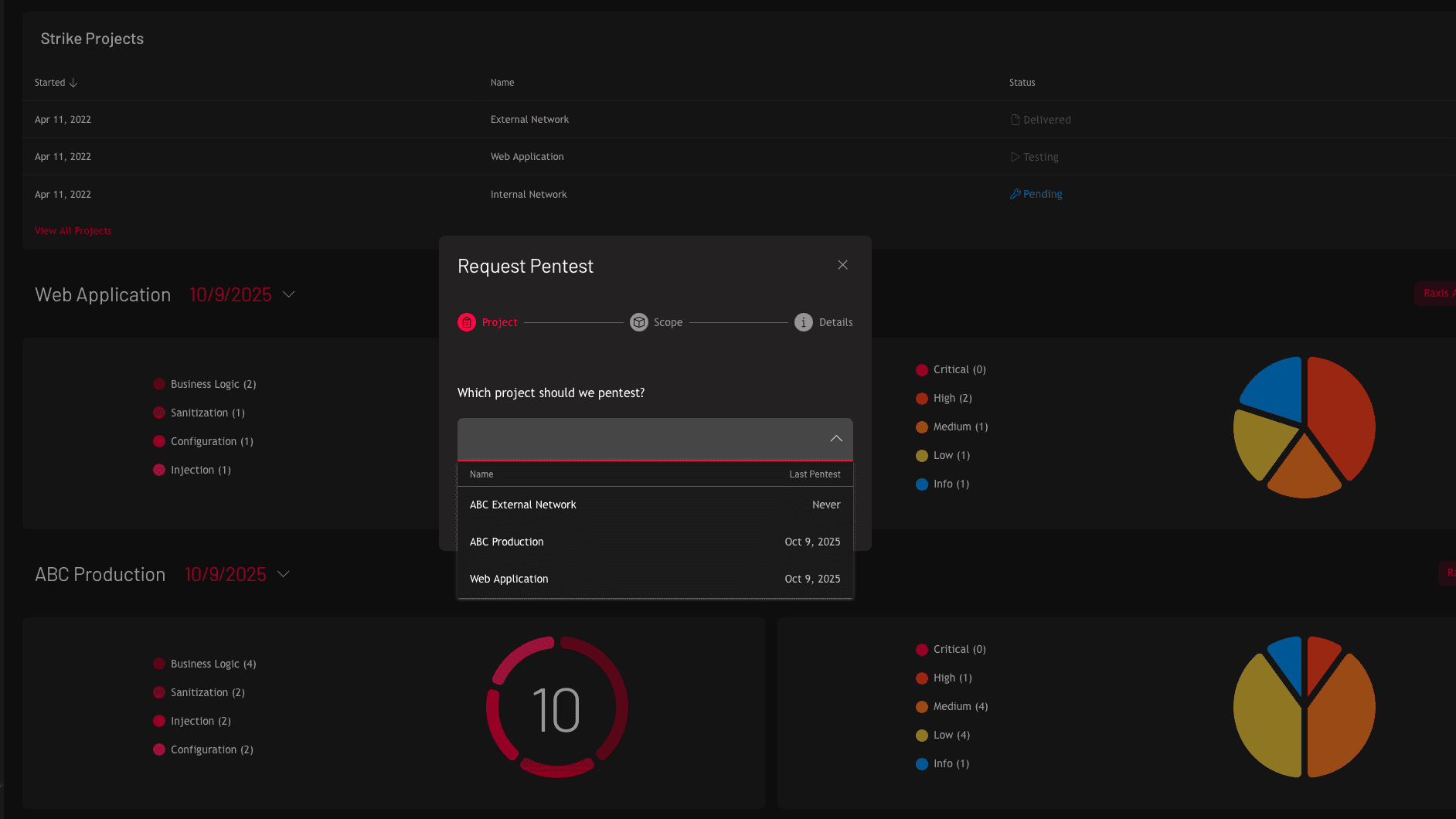
Raxis Attack delivers continuous penetration testing through an always-on platform, giving you unlimited assessments throughout the year instead of a single point-in-time snapshot. Monitor your security posture in real time, request tests on demand, and track remediation progress — all through the Raxis One portal.
Internal Network Penetration Testing
Our testers assess your internal networks, cloud environments, and VPCs — including AWS, Azure, and GCP — to identify lateral movement paths, privilege escalation opportunities, and misconfigurations.
Web Application Penetration Testing
We go beyond OWASP Top 10 scanning to manually test your web applications for complex logic flaws, authentication bypasses, and injection vulnerabilities that only skilled human testers can find.
API Penetration Testing
APIs are among the most targeted and least tested attack surfaces. Our team evaluates your APIs for broken authentication, data exposure, and authorization flaws that could compromise your most sensitive data.
Wireless Penetration Testing
Using our Transporter hardware deployed on-site, we test your wireless networks for rogue access points, weak encryption, and misconfigurations that could allow an attacker to bypass your perimeter entirely.
Mobile Application Penetration Testing
We test your iOS and Android applications for insecure data storage, weak encryption, and server-side vulnerabilities — giving you a clear picture of your mobile security posture.
IoT Penetration Testing
Raxis IoT penetration testing uncovers hidden vulnerabilities across your entire device ecosystem — from hardware and firmware to cloud APIs and wireless protocols.
OT Penetration Testing
Raxis tests your SCADA, ICS, and industrial control systems for exploitable vulnerabilities — without disrupting the operations that keep your business running. From field devices to IT/OT boundaries, we find the gaps attackers cross.
Phishing Penetration Testing
We test your people alongside your technology. Our social engineering assessments use targeted phishing, spear phishing, and pretexting to measure how your organization responds to real-world manipulation tactics.
Physical Penetration Testing
Our Red Team engineers breach your facilities using the same tactics real adversaries deploy — tailgating, badge cloning, lock picking, and pretexting. We prove how physical entry cascades into full network compromise.

Salesforce Penetration Testing
Salesforce environments hold your most sensitive customer data — and misconfigured sharing rules, exposed APIs, and weak access controls put it all at risk. Raxis tests your Salesforce org for the vulnerabilities that standard security reviews miss.
Proudly Built in Atlanta
Our platform is proudly designed and coded in Atlanta, and our incredible engineering team is distributed across the United States.
What Makes Raxis Penetration Testing More Effective
Trusted by startups and enterprises alike, Raxis is a penetration test company built on one principle: real security comes from real attacks, not automated reports.
Ethical Hackers, Not Just Scanners
Our certified testers go far beyond vulnerability scanning. They chain together exploits, test complex logic flaws, and simulate realistic attack scenarios using the same tactics and techniques that real-world adversaries use. Every engagement is led by experienced security experts with OSCP, GPEN, GWAPT, and other industry-recognized certifications — giving you results that automated tools simply cannot deliver.
Compliance-Ready Reporting
Penetration testing shouldn’t create more work at audit time. Our reports are built to satisfy the requirements of PCI DSS, SOC 2, HIPAA, GLBA, CMMC, ISO 27001, and other regulatory frameworks out of the box. Each report includes executive summaries for leadership, detailed technical findings for your engineering team, and clear remediation guidance to help you close gaps fast.
Continuous Protection, Not Just Point-in-Time Snapshots
Threats evolve constantly, and annual testing leaves you exposed between assessments. Through PTaaS and attack surface management, Raxis provides continuous security testing that adapts as your environment changes. Request assessments on demand, monitor emerging vulnerabilities in real time, and track your security posture through the Raxis One portal.
Actionable Remediation That Strengthens Your Defenses
We don’t just find vulnerabilities — we help you fix them. Every finding comes with prioritized, actionable steps to remediate security weaknesses and strengthen your security controls. Our testers are available for retesting after remediation, so you can validate fixes and demonstrate measurable improvement to stakeholders and auditors.
Our Customers Agree
“The team from Raxis are true professionals”
“The team from Raxis are true professionals. They immediately added capabilities, tools and an experienced perspective to our team. You can count on them to deliver exactly what their proposal contains as scheduled.”
Raxis Is Live at RSA 2026
Join our elite penetration testing team at RSA Conference 2026, Booth S-2444, to see real-world attacks in action and learn how Raxis Attack keeps your security posture ahead of evolving threats.
Latest From Our Cybersecurity Blog, The Exploit
-
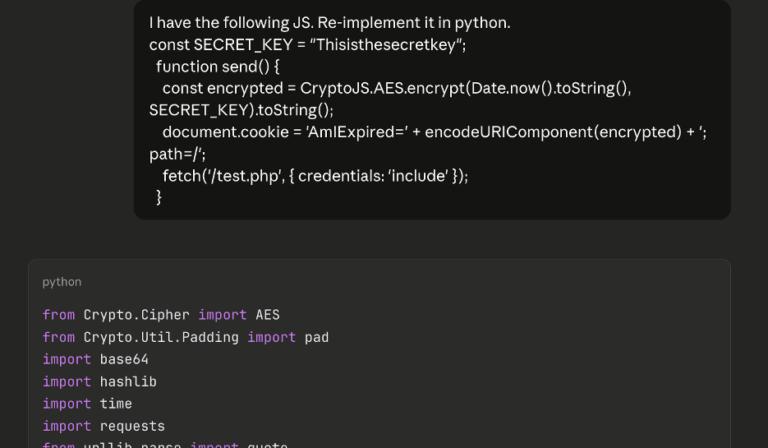
AI-Augmented Series: AI Scripting for Brute-Forcing on a Web App Pentest
By Andrew Trexler • March 4, 2026On a recent web app pentest, Andrew Trexler used AI to find client-side code that stopped his brute-force attack then used AI again to thwart that code. -
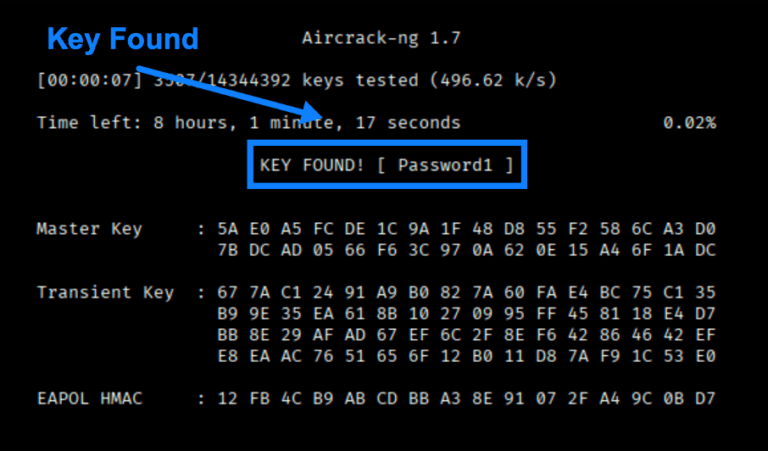
Wireless Series: The Aircrack-ng Suite for All Your Wireless Pentesting Needs
By Scottie Cole • February 24, 2026Principal Penetration Tester Scottie Cole continues our wireless series with the Aircrack-ng Suite, a set of tools for wireless pentest discovery and exploits. -

Reynolds Ransomware BYOVD Eludes EDR Tools
By Nathan Anderson • February 20, 2026Reynolds poses a new type of threat by including a Bring Your Own Vulnerable Driver (BYOVD) in the ransomware bundle, making it harder for EDR tools to catch.