Password Cracking
Raxis Blog Posts by Category
-
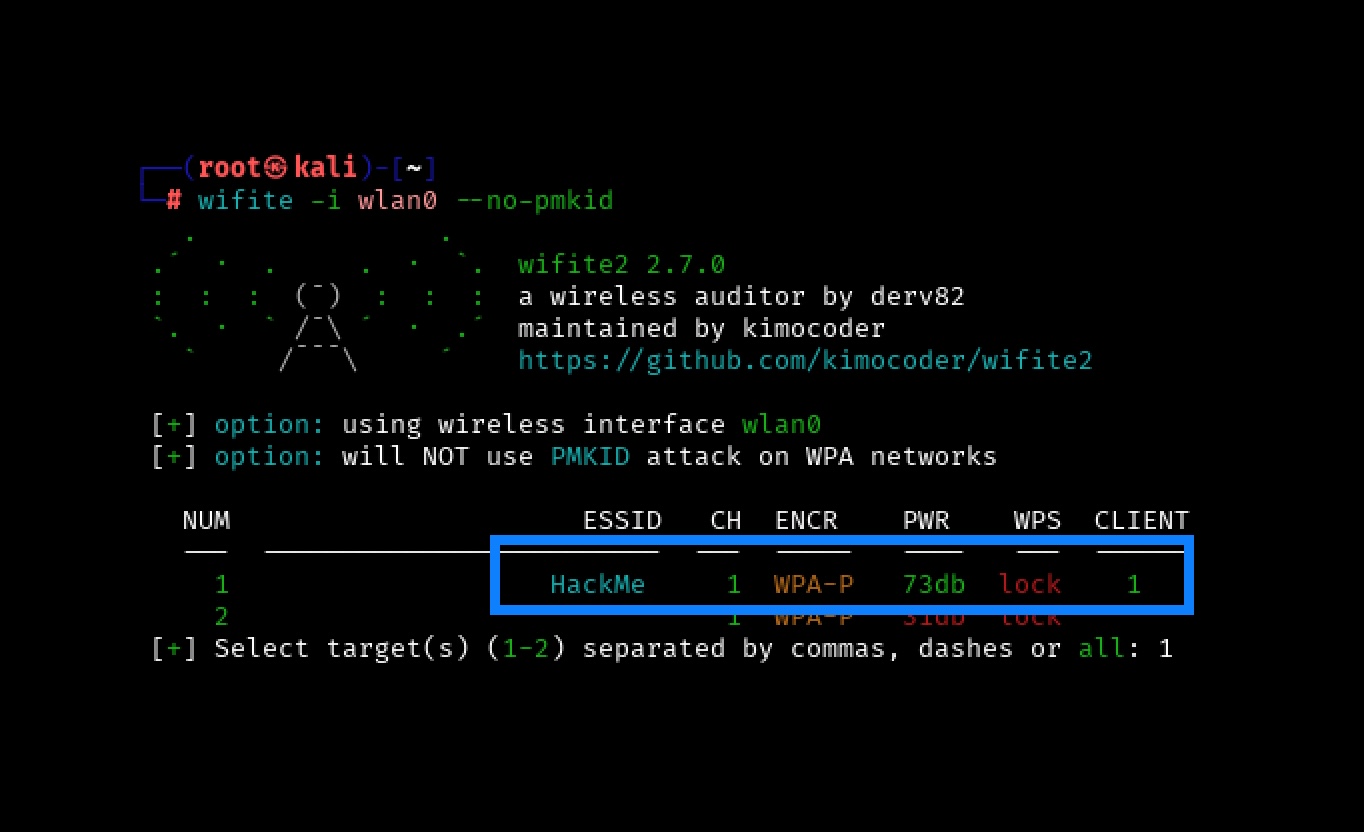 Wireless Series: Using Wifite to Capture and Crack a WPA2 Pre-Shared Key for Penetration TestingPrincipal Penetration Tester Scottie Cole begins our wireless penetration testing series with capturing and cracking a WPA2 Pre-Shared Key using Wifite.
Wireless Series: Using Wifite to Capture and Crack a WPA2 Pre-Shared Key for Penetration TestingPrincipal Penetration Tester Scottie Cole begins our wireless penetration testing series with capturing and cracking a WPA2 Pre-Shared Key using Wifite. -
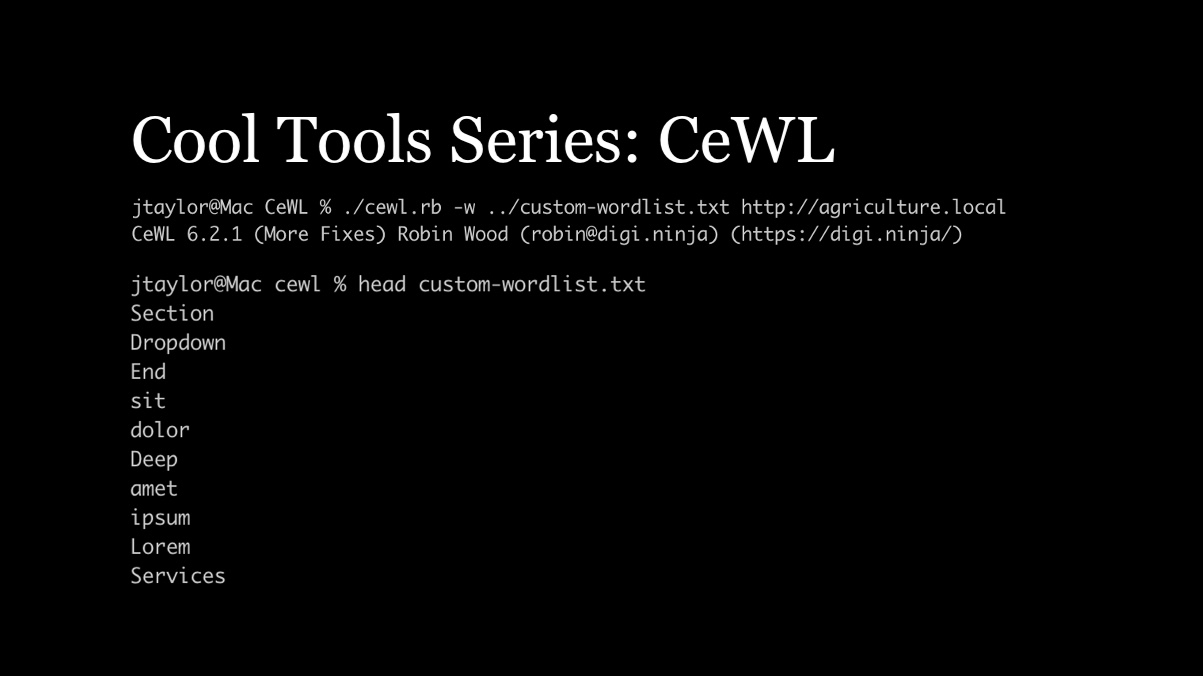 Cool Tools Series: CeWL for Penetration TestingLead Penetration Tester Jason Taylor discusses how the CeWL Custom Word List generator can improve hashcat results for penetration testing.
Cool Tools Series: CeWL for Penetration TestingLead Penetration Tester Jason Taylor discusses how the CeWL Custom Word List generator can improve hashcat results for penetration testing. -
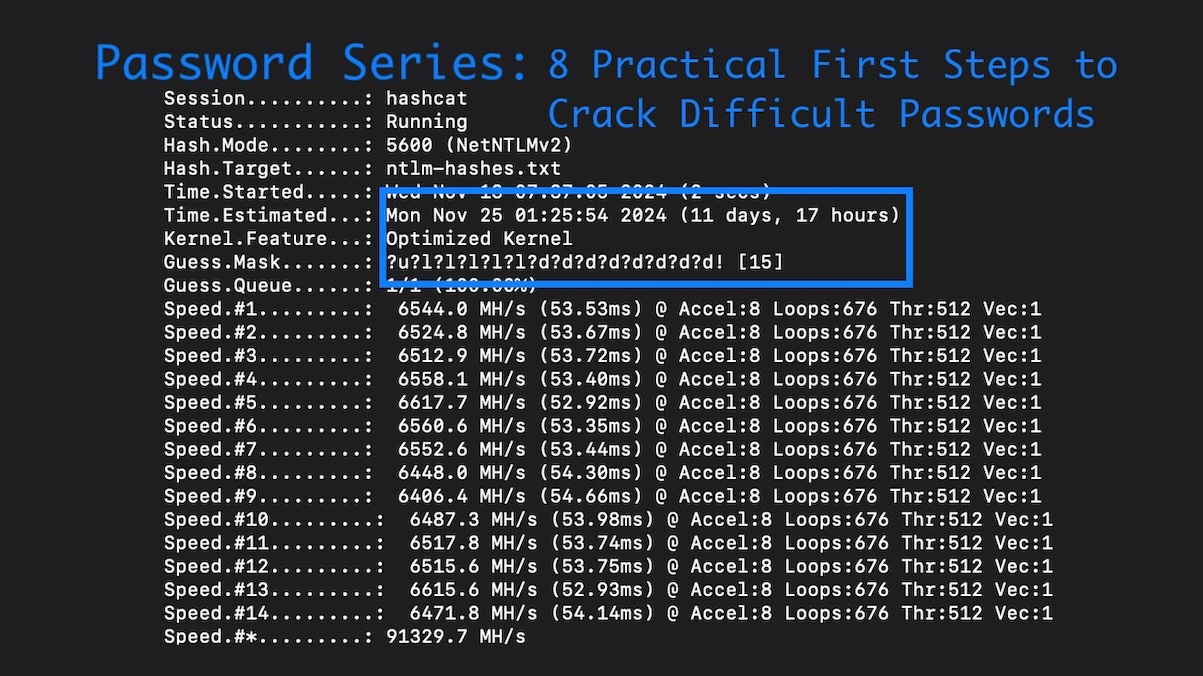 Password Series: 8 Practical First Steps to Crack Difficult Passwords in Penetration TestsFrom rulesets and hardware to wordlists and mask attacks, Lead Penetration Tester Ryan Chaplin shows how to crack difficult password hashes in penetration tests.
Password Series: 8 Practical First Steps to Crack Difficult Passwords in Penetration TestsFrom rulesets and hardware to wordlists and mask attacks, Lead Penetration Tester Ryan Chaplin shows how to crack difficult password hashes in penetration tests. -
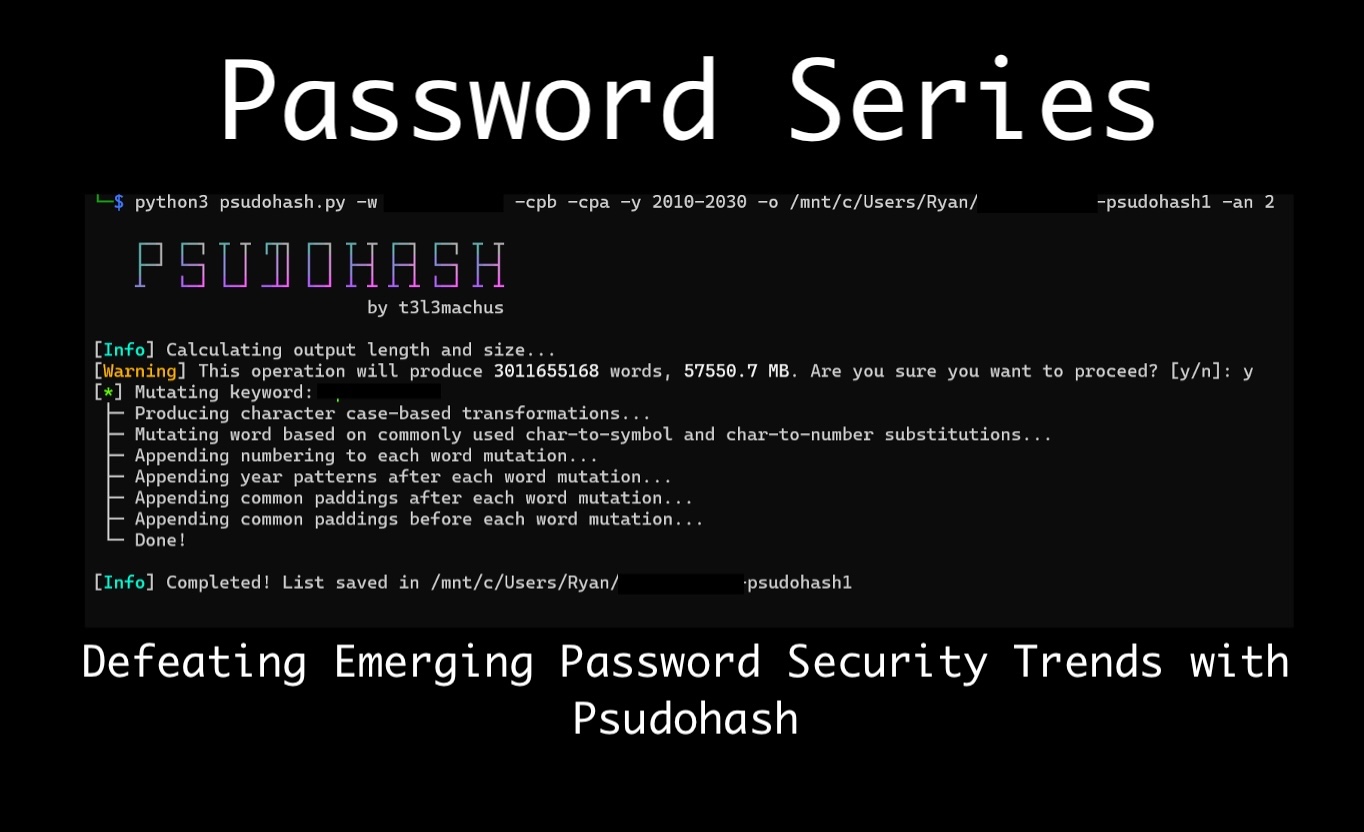 Password Series: Defeating Emerging Password Security Trends with Psudohash for Penetration TestingLead Pentester Ryan Chaplin discusses emerging improvements in password security and how Psudohash can help bypass them on penetration tests.
Password Series: Defeating Emerging Password Security Trends with Psudohash for Penetration TestingLead Pentester Ryan Chaplin discusses emerging improvements in password security and how Psudohash can help bypass them on penetration tests. -
 Password Length: More than Just a Question of CompliancePassword length requirements are a key part of password security, but, with PCI, NIST, OWASP, and CIS offering different recommendations, what length is best?
Password Length: More than Just a Question of CompliancePassword length requirements are a key part of password security, but, with PCI, NIST, OWASP, and CIS offering different recommendations, what length is best? -
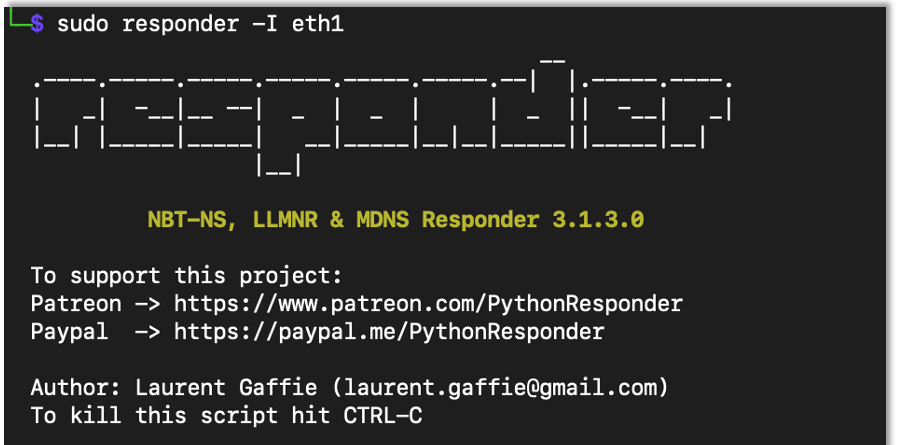 AD Series: How to Perform Broadcast Attacks Using NTLMRelayx, MiTM6 and Responder for Penetration TestsAndrew Trexler continues his AD Series with an in-depth tutorial on broadcast Attacks using NTLMRelayx, MiTM6 and Responder for penetration tests.
AD Series: How to Perform Broadcast Attacks Using NTLMRelayx, MiTM6 and Responder for Penetration TestsAndrew Trexler continues his AD Series with an in-depth tutorial on broadcast Attacks using NTLMRelayx, MiTM6 and Responder for penetration tests. -
 How to Create an AD Test Environment to Use for Penetration TestingAndrew Trexler walks us through creating a simple AD test environment to test new hacks before trying them on a penetration test.
How to Create an AD Test Environment to Use for Penetration TestingAndrew Trexler walks us through creating a simple AD test environment to test new hacks before trying them on a penetration test. -
 Understanding the Why Behind Password ManagementIn this video, Raxis CTO Brian Tant explains why password mismanagement is still one of the most reliable ways to breach a company network and what you can do to secure your network.
Understanding the Why Behind Password ManagementIn this video, Raxis CTO Brian Tant explains why password mismanagement is still one of the most reliable ways to breach a company network and what you can do to secure your network. -
 3 Steps You Should Take Right Now to Reduce Your Risk of a CyberattackIn this video, Raxis CTO Brian Tant talks about three steps you should take to secure your network against hackers.
3 Steps You Should Take Right Now to Reduce Your Risk of a CyberattackIn this video, Raxis CTO Brian Tant talks about three steps you should take to secure your network against hackers. -
 IKE VPNs Supporting Aggressive ModeIn this post we’ll look at why IKE VPNs with Aggressive Mode enabled continue to be a vulnerability, how it can be exploited, and how to mitigate this risk.
IKE VPNs Supporting Aggressive ModeIn this post we’ll look at why IKE VPNs with Aggressive Mode enabled continue to be a vulnerability, how it can be exploited, and how to mitigate this risk. -
 The Weakest Link in the Password HashRaxis VP of Business Development explains easy rules to use to make your passwords more secure and harder for hackers to crack.
The Weakest Link in the Password HashRaxis VP of Business Development explains easy rules to use to make your passwords more secure and harder for hackers to crack. -
 HP iLO Password CrackingRaxis CEO Mark Puckett shows how simple and fast it is for a hacker to crack a weak HP iLO password hash.
HP iLO Password CrackingRaxis CEO Mark Puckett shows how simple and fast it is for a hacker to crack a weak HP iLO password hash.
Categories
- Careers
- Exploits
- How To
- In The News
- Injection Attacks
- Just For Fun
- Meet The Team
- Mobile Apps
- Networks
- Password Cracking
- Penetration Testing
- Phishing
- PTaaS
- Raxis In The Community
- Red Team
- Security Recommendations
- Social Engineering
- Tips For Everyone
- Unsupported Software Unpatched Systems
- Web Apps
- What People Are Saying
- Wireless
