Raxis Red Team Services
“Everybody Has a Plan Until They Get Punched in the Face.” -Mike Tyson
Red Teaming
Are You truly prepared for a cyber attack?
Red Teaming is where we excel. Since 2011, we’ve empowered Fortune 500 companies and mission-critical businesses with battle-tested expertise. The Raxis Red Team doesn’t just probe your defenses—we redefine them. Unlike standard vulnerability scans or penetration tests, a Red Team assessment is a full-scope attack simulation designed to test your people, processes, and technology under realistic conditions. This holistic approach identifies security gaps that automated tools and conventional tests often miss.
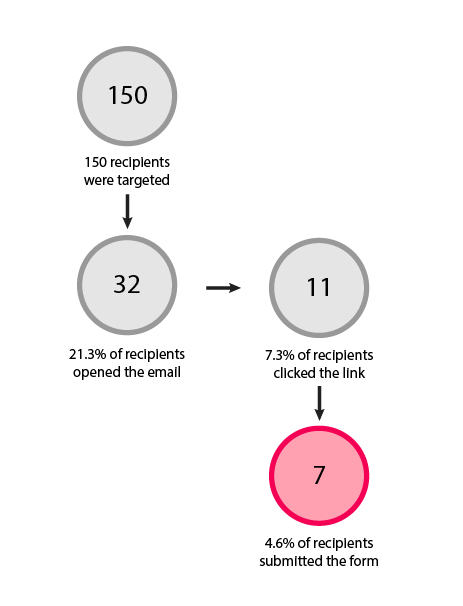
Email Phishing
We craft custom phishing campaigns tailored to your organization’s unique profile, ensuring maximum effectiveness and relevance. Our targeted approach allows us to focus on specific high-risk roles or conduct company-wide assessments, providing comprehensive insights into your cybersecurity awareness.
Physical Social Engineering
We’re experts at talking our way in, tailgating, and even circumventing digital locks to gain access to your network.
Telephone Social Engineering
Phones are increasingly being used to breach companies, and we will utilize similar tactics to assess the effectiveness of your security training.
Vulnerability Exploitation
Our red team uses advanced techniques to find and exploit system vulnerabilities with tools like Nmap and Metasploit. Leveraging our collective expertise, the Raxis Red Team consistently outperforms industry rivals, delivering superior results. Our reputation for excellence has led clients to engage us when other security firms fall short, solidifying our position as the go-to experts for challenging cybersecurity assessments.
Pivoting and Lateral Movement
Once we gain a foothold, we pivot laterally through your network using tools like Mimikatz and PAExec to expand reach and access sensitive materials.
Privilege Escalation
We will elevate privileges by leveraging methods such as misconfigured permissions, exploiting vulnerabilities in the kernel, and taking advantage of weaknesses in local accounts.
Harvesting Credentials
Upon gaining access, we’ll securely extract and analyze critical authentication data, including password hashes and digital certificates. This comprehensive approach allows us to identify potential vulnerabilities in your authentication mechanisms and provide targeted recommendations to enhance your overall security posture.
Password Hash Cracking
Leveraging our GPU-accelerated password recovery system running Hashcat, we’ll employ substantial dictionaries and advanced rules to crack as many hashed credentials as we can.
Password Analysis
The Raxis Red Team conducts a comprehensive analysis of your cracked passwords, delivering detailed insights into password strength and complexity. We provide actionable recommendations to enhance your overall password security posture, helping you implement better defenses against potential threats.
Search For The Goods
The Raxis Red team will comprehensively scan file shares, databases, and even local workstations to pinpoint the most critical information. This highlights the potential risk of a cyber attack, helping you justify budget allocation for security measures.
Exfiltrate Data
Once we identify the most vital components, we will demonstrate that we can extract data without physically removing anything from your network. This enhances the evidence of cybersecurity risk.
Test Detection and Response
Our simulated data exfiltration exercise tests your existing security controls, providing valuable insights to enhance your incident response capabilities. This process allows us to identify potential gaps in your defenses and offer targeted recommendations for strengthening your overall security posture against real-world threats.
Experience the Thrill of A Red Team
Red Team Operations Designed For You
Let’s Work Together
Many customers use our Red Team to test the effectiveness of their Blue Team. We’ll work closely with you to orchestrate a real world cyber attack to ensure everyone is ready when the real attack happens.
Real Vulnerability Exploitation
We’ll combine open source intelligence, dark web data, social engineering, our rock star pentesting team, and evasion techniques to safely test every aspect of your defense.
Safe, Blended Attacks
While our Red Team’s real-world cyber-attack is highly effective at finding gaps in your armor, we take precautions to ensure your systems and data remain safe during this controlled simulation.
Interface With Raxis One
Your interface to your Red Team engagement is through our online customer management portal, Raxis One. Securely communicate with your Red Team or download your comprehensive report.
Physical Security
In most of our Red Team assessments, physical security is deemed in scope to gain a full-inset view of every potential avenue of attack. We test physical security to ensure that intruders can’t gain access to your technology.
Experienced Professionals
Raxis’ Red Team brings decades of clandestine experience to bear against your defenses. Certifications include the OSCP, OSWE, C|EH, GPEN, and many others.
The Digital Shoplifter
Raxis Hack Stories
Our stories are based on real events encountered by Raxis engineers; however, some details have been altered or omitted to protect our customers’ identities.
In a daring demonstration of cybersecurity vulnerabilities, the Raxis Red Team orchestrated a multi-stage attack that exposed critical weaknesses in a major retailer’s digital infrastructure. The operation began with our team targeting the company’s wireless network using the powerful Aircrack-ng suite. This versatile toolkit allowed us to capture the network’s encryption key during a routine handshake process and swiftly crack it using Hashcat’s advanced capabilities.
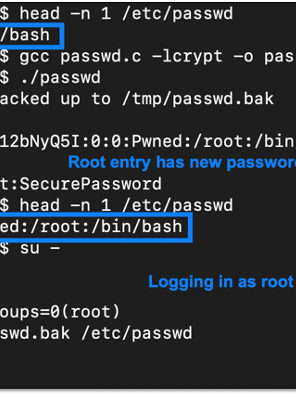
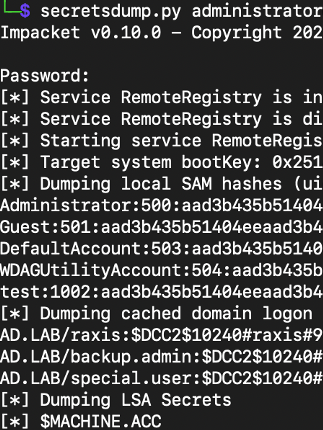
With network access secured, we obtained local system access and then pivoted to internal systems using CrackMapExec, a potent post-exploitation tool. We discovered a system protected by nothing more than a default password—a digital equivalent of leaving the keys in the ignition. This oversight became our gateway, allowing us to gain local administrator privileges. Using CrackMapExec’s –sam option, we dumped the local SAM hashes, further expanding our access.
Like master locksmiths, we moved from system to system, leveraging our newly acquired local admin rights. Eventually, we obtained a prized domain administrator hash. Overnight, our dedicated team worked tirelessly, using Raxis’ Hashcat multi-GPU system to break this high-value credential. Returning the next day, we validated our newfound domain administrative access, cementing our control over the retailer’s entire digital domain.
The crown jewel of our operation was the discovery of the application and database containing store-branded gift cards and PINs, along with the ability to generate new ones at will. This find not only highlighted the potential for financial exploitation but also underscored the critical importance of robust, multi-layered cybersecurity measures in today’s retail landscape.
Our Unique Edge
Uncovering What Others Miss
Many organizations rely on leading cybersecurity providers for their initial assessments—only to discover that complex threats and subtle vulnerabilities still remain undetected. Raxis Red Team is frequently called in after large, well-known competitors have completed their work, and time and again, we uncover critical security gaps that were completely overlooked.
Our approach is different: we don’t just scan for surface-level weaknesses. Instead, we simulate real-world adversaries, leveraging advanced techniques, persistence, and creativity to find hidden paths that could lead to a full compromise of your systems. Often, these vulnerabilities are not only missed by other teams but are the exact entry points that sophisticated attackers would exploit to move laterally, escalate privileges, and access sensitive data.
By focusing on stealth and persistence—much like actual cybercriminals—Raxis Red Team exposes flaws in your defenses that traditional testing simply doesn’t catch. Our findings frequently reveal just how close your organization might be to a serious breach, even after previous assessments by industry leaders. This makes Raxis Red Team the ultimate second opinion—and your best defense against threats that others fail to see.


Red Teams, Blue Teams, And Purple Teams
The cybersecurity field has adopted the terms Red Teams, Blue Teams, and Purple Teams to categorize various methods of evaluating and enhancing an organization’s security.
- Red Teams simulate real-world attackers, constantly probing your defenses to find vulnerabilities before cybercriminals do.
- Blue Teams are your defenders, monitoring networks, detecting intrusions, and responding to incidents to keep your organization safe.
- Purple Teams bridge the gap between Red and Blue, fostering collaboration and continuous improvement. By sharing insights and working together, Purple Teams help both sides learn from each other, ensuring your security posture is always advancing.
F.A.Q.
Frequently Asked Questions