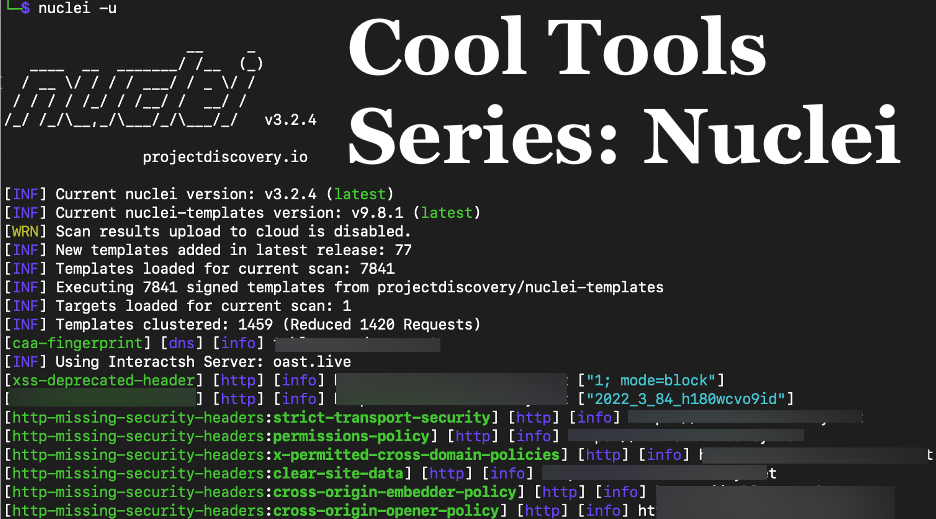
Hopefully you enjoyed Adam Fernandez’s recent Cool Tools post, Nmap For Penetration Tests. In this next post in the series, I’d like to introduce another great penetration testing tool: Nuclei.
Nuclei is an outstanding enumeration tool that performs a myriad of checks against the systems and services it discovers. It does particularly well against web applications. It also tests for known vulnerabilities, can pull versioning information from systems, and can try default credentials.
Installing Nuclei
You can use apt to easily install it on Kali Linux:
apt install nuclei
Templates
Nuclei uses saved templates to perform tests against systems. This lets users create new templates as new discoveries are made. You can also generate custom templates for tasks you often use or things you discover yourself.
More information about these templates can be found here: https://docs.projectdiscovery.io/templates/introduction
You can explore the templates Nuclei uses by default here.
https://github.com/projectdiscovery/nuclei-templates/tree/main
Options
There are a lot of different options when using the tool, but generally, when I’m using it for external network and web application tests, I just pass a target or a list of targets to the program.
To get a full list of options, all you need to do is this command:
nuclei –helpTo scan a single device, simply use:
nuclei -u {Target}Here is an example from a recent penetration test. There was only one target, so I simply passed that target to Nuclei:
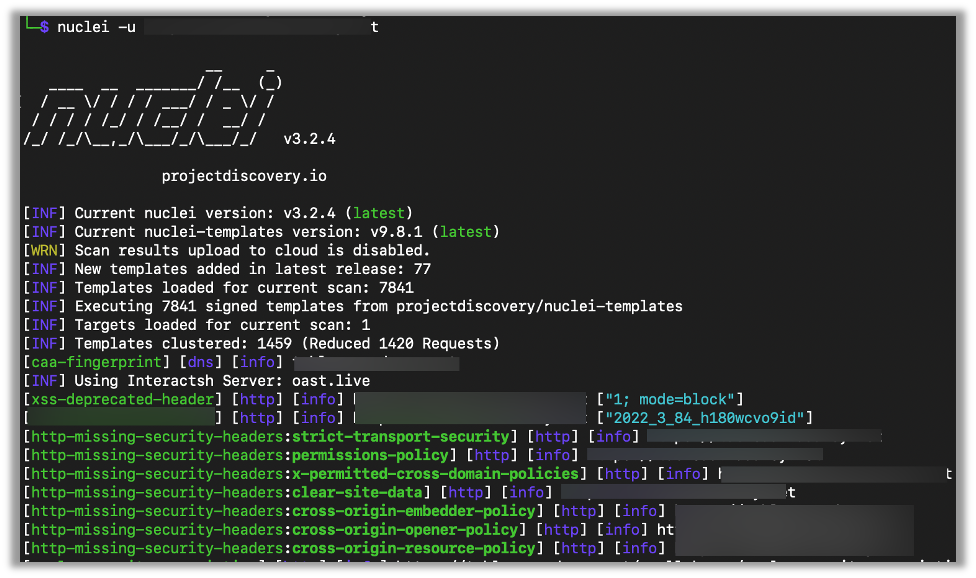
You can see that Nuclei examined the responses from the web server and found that security-related headers were missing.
Here is an example using Nuclei against a list of targets. I put the targets for the engagement into a file called targets & ran the following command:
nuclei -list {File}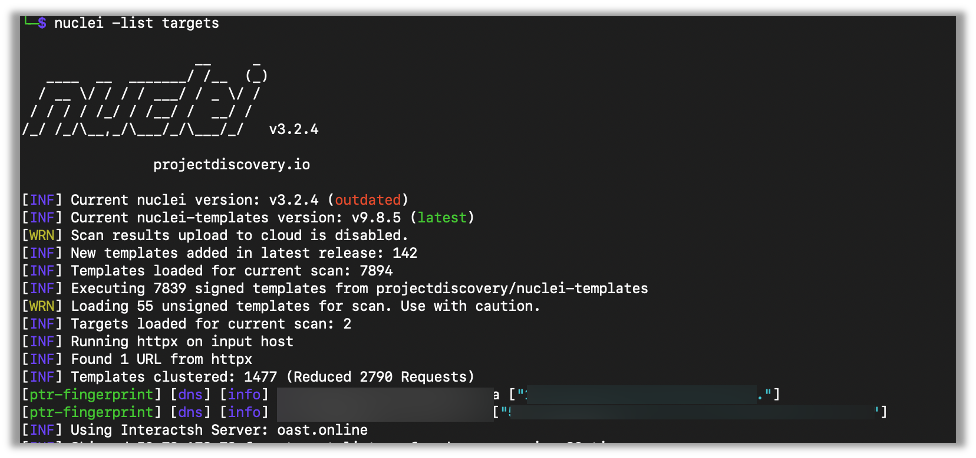
Real-World Nuclei Discoveries
Here are some examples of useful things Nuclei has found for me during various penetration tests.
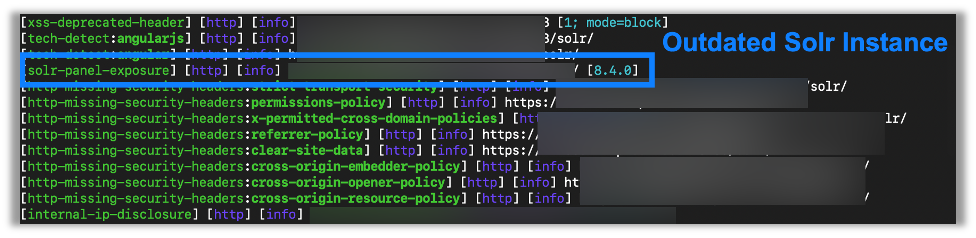
Here Nuclei found a Solr panel, revealed the version running, and shared it in a human-readable format easy for me to use as a pentester:
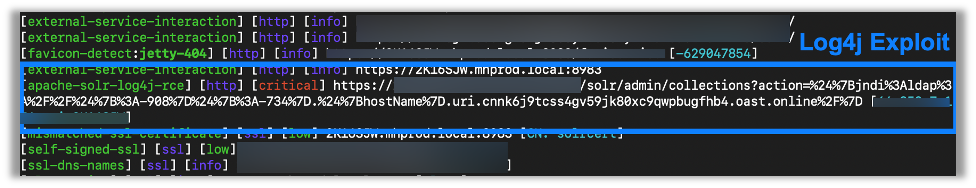
Here Nuclei did some testing against a host on an internal network and successfully performed a Log4j exploit. It then reported the success with a critical flag as this could lead to remote code execution (RCE):
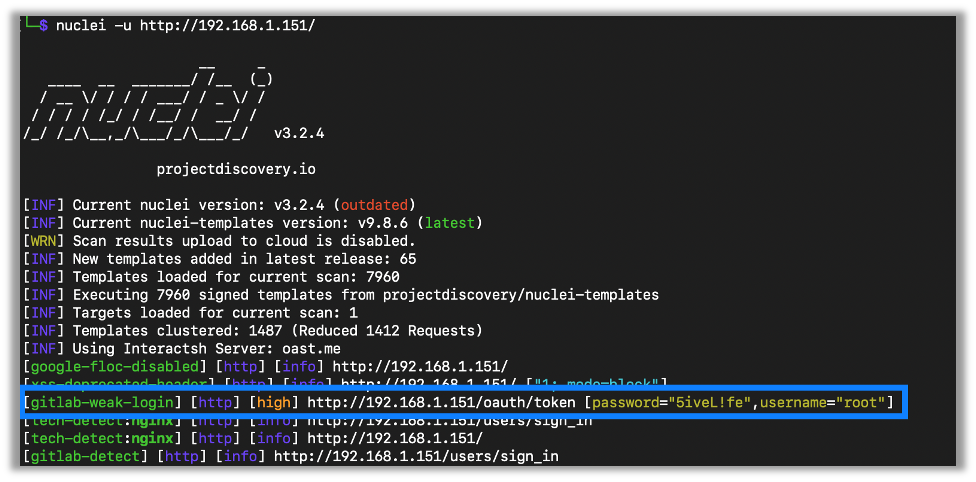
I’ve also found Nuclei’s ability to try default passwords to come in handy when testing.
As an example, I use a self-hosted Git instance and changed the root account’s password to one that Nuclei uses. You can see how Nuclei successfully logged into the GitLab and notified me:
Thanks for Reading
There’s a lot more to Nuclei, but this is a good start. Thanks for taking a look at this post, and I hope you’ll take a look at the next post in the Cool Tools series as well.