
Red Team Services
“Everybody Has a Plan Until They Get Punched in the Face.” -Mike Tyson
Red Teaming
Are you prepared for a cyber attack?
Red Teaming is where we excel. Since 2011, we’ve empowered Fortune 500 companies and mission-critical businesses with battle-tested expertise. The Raxis Red Team doesn’t just probe your defenses—we redefine them. Unlike standard vulnerability scans or penetration tests, a Red Team assessment is a full-scope attack simulation designed to test your people, processes, and technology under realistic conditions. This holistic approach identifies security gaps that automated tools and conventional tests often miss.
Key components to successful Red Teaming include:
Social Engineering
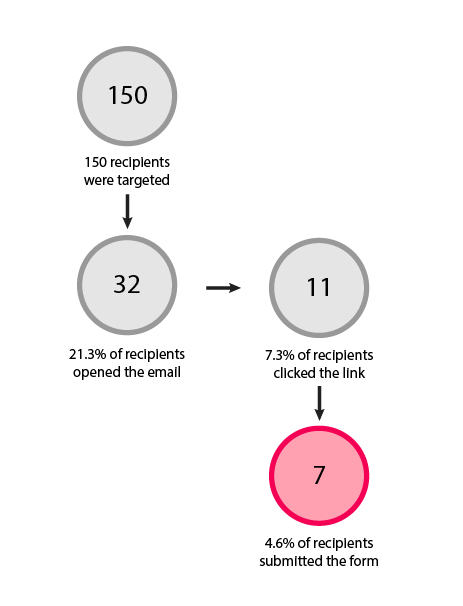
Email Phishing
We craft custom phishing campaigns tailored to your organization’s unique profile, ensuring maximum effectiveness and relevance. Our targeted approach allows us to focus on specific high-risk roles or conduct company-wide assessments, providing comprehensive insights into your cybersecurity awareness.
Physical Social Engineering
We’re experts at talking our way in, tailgating, and even circumventing digital locks to gain access to your network.
Telephone Social Engineering
Phones are increasingly being used to breach companies, and we will utilize similar tactics to assess the effectiveness of your security training.
Vulnerability Exploitation
Safe Exploitation
Our red team uses advanced techniques to find and exploit system vulnerabilities with tools like Nmap and Metasploit. Leveraging our collective expertise, the Raxis Red Team consistently outperforms industry rivals, delivering superior results. Our reputation for excellence has led clients to engage us when other security firms fall short, solidifying our position as the go-to experts for challenging cybersecurity assessments.
Pivoting and Lateral Movement
Once we gain a foothold, we pivot laterally through your network using tools like Mimikatz and PAExec to expand reach and access sensitive materials.
Privilege Escalation
We will elevate privileges by leveraging methods such as misconfigured permissions, exploiting vulnerabilities in the kernel, and taking advantage of weaknesses in local accounts.
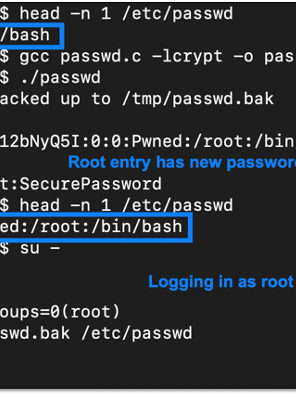
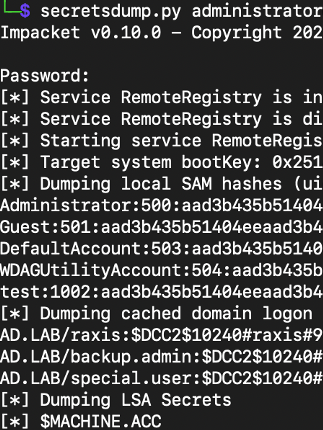
Password Hacking
Harvesting Credentials
Upon gaining access, we’ll securely extract and analyze critical authentication data, including password hashes and digital certificates. This comprehensive approach allows us to identify potential vulnerabilities in your authentication mechanisms and provide targeted recommendations to enhance your overall security posture.
Password Hash Cracking
Leveraging our GPU-accelerated password recovery system running Hashcat, we’ll employ substantial dictionaries and advanced rules to crack as many hashed credentials as we can.
Password Analysis
The Raxis Red Team conducts a comprehensive analysis of your cracked passwords, delivering detailed insights into password strength and complexity. We provide actionable recommendations to enhance your overall password security posture, helping you implement better defenses against potential threats.
Data Exfiltration
Search For The Goods
The Raxis Red team will comprehensively scan file shares, databases, and even local workstations to pinpoint the most critical information. This highlights the potential risk of a cyber attack, helping you justify budget allocation for security measures.
Exfiltrate Data
Once we identify the most vital components, we will demonstrate that we can extract data without physically removing anything from your network. This enhances the evidence of cybersecurity risk.
Test Detection and Response
Our simulated data exfiltration exercise tests your existing security controls, providing valuable insights to enhance your incident response capabilities. This process allows us to identify potential gaps in your defenses and offer targeted recommendations for strengthening your overall security posture against real-world threats.

Red Team Operations Customized For You
Let’s Work Together
Many customers use our Red Team to test the effectiveness of their Blue Team. We’ll work closely with you to orchestrate a real world cyber attack to ensure everyone is ready when the real attack happens.
Real Vulnerability Exploitation
We’ll combine open source intelligence, dark web data, social engineering, our rock star pentesting team, and evasion techniques to safely test every aspect of your defense.
Safe, Blended Attacks
While our Red Team’s real-world cyber-attack is highly effective at finding gaps in your armor, we take precautions to ensure your systems and data remain safe during this controlled simulation.
Interface With Raxis One
Your interface to your Red Team engagement is through our online customer management portal, Raxis One. Securely communicate with your Red Team or download your comprehensive report.
Physical Security
In most of our Red Team assessments, physical security is deemed in scope to gain a full-inset view of every potential avenue of attack. We test physical security to ensure that intruders can’t gain access to your technology.
Experienced Professionals
Raxis’ Red Team brings decades of clandestine experience to bear against your defenses. Certifications include the OSCP, OSWE, C|EH, GPEN, and many others.
The Raxis Red Teaming Methodology
For over 14 years, Raxis has been a trusted name in cybersecurity, delivering exceptional red teaming services through our comprehensive adversarial simulation offerings. We partner with organizations across industries and sizes, leveraging the industry-standard MITRE ATT&CK framework to guide our approach. Our US-based expert team simulates sophisticated real-world attacks with precision, identifying gaps in your defenses and providing actionable insights to enhance your overall security posture.
Scoping
Every organization faces unique security challenges, so Raxis begins by collaborating closely with you to define the scope of the red team engagement. This includes identifying key assets, systems, networks, personnel, and physical locations to be tested, while setting clear objectives aligned with your specific risks and compliance needs. We tailor scenarios to simulate realistic threats, such as advanced persistent threats (APTs), insider risks, or multi-vector attacks involving cyber, social, and physical elements.
Intelligence Gathering
Raxis conducts thorough reconnaissance by gathering and analyzing publicly available information about your organization, employees, and operations to uncover potential entry points. Sources include public websites, social media, domain registries, dark web forums, and open-source intelligence (OSINT). Our experts evaluate this data to identify vulnerabilities like exposed personal details, leaked credentials, or organizational weaknesses that could be exploited in a targeted attack, allowing you to address risks proactively.
Vulnerability Identification
With the scope established, our red team experts employ a blend of manual techniques and advanced tools to pinpoint vulnerabilities across your environment. This encompasses cyber elements like misconfigurations, outdated software, and insecure protocols, as well as social and physical weaknesses such as susceptible employees or access controls. Unlike automated scans, our manual assessments ensure a deep, contextual understanding of how these issues could be chained together in a real-world adversarial campaign.
Strategic Threat Modeling
Raxis enhances your defenses through a dedicated threat modeling phase, where we catalog critical assets—from digital infrastructure and sensitive data to physical facilities and key personnel. Drawing on intelligence from public sources, dark web insights, and industry-specific threat landscapes, we map potential adversaries and their tactics. Our team develops detailed attack trees that simulate sophisticated threat actors, exposing hidden risks and delivering prioritized strategies to fortify your resilience against targeted attacks.
Adversarial Simulation
To test your security holistically, Raxis emulates real-world adversaries by launching simulated attacks across multiple vectors, including phishing, social engineering, physical intrusions, and cyber exploits. We assess your organization’s detection, response, and recovery capabilities using tactics like lateral movement, command and control establishment, and evasion techniques. This phase evaluates not just technical defenses but also human factors and procedural gaps, providing a true measure of your readiness against persistent threats.
Exploitation
Within the agreed scope, Raxis carefully exploits identified vulnerabilities to demonstrate how an adversary could achieve objectives like unauthorized access, data exfiltration, or operational disruption. We execute controlled, ethical attacks with proof-of-concept scenarios that highlight potential impacts, such as compromising high-value assets or bypassing detection systems. This helps you understand the real-world consequences and prioritize remediation without causing actual harm.
Impactful Post-Exploitation Analysis
Raxis goes beyond initial breaches by conducting in-depth post-exploitation testing to illustrate the full ramifications of a successful attack. We evaluate the sensitivity of compromised assets, simulate pivoting to additional targets, privilege escalation, and persistent access maintenance. Using manual techniques, we safely demonstrate data compromise or further network infiltration, redacting sensitive information while providing clear evidence of risks to inform stronger defensive measures.
Reporting
Upon completion, we deliver a detailed report outlining all findings, including a prioritized vulnerability list categorized by severity (critical, high, medium) and their potential business impacts. Each issue includes proof-of-concept exploits, attack narratives, and remediation recommendations. A visual storyboard depicts how an adversary could chain exploits for maximum effect, offering a narrative-driven view of the engagement to facilitate executive understanding and decision-making.
Actionable Advisory and Remediation Planning
Raxis extends support beyond the report with a collaborative debrief session, where we walk you through the findings, clarify results, and address any questions. We provide tailored, practical recommendations to mitigate identified risks, prioritizing efforts based on threat likelihood and impact. Our experts work with your team to develop a strategic remediation plan, ensuring efficient implementation and helping build long-term defenses against evolving adversarial tactics.
Thorough Retest Validation
To confirm the effectiveness of your remediation, Raxis offers comprehensive retesting services. We revisit previously exploited vulnerabilities and scenarios to verify fixes, while checking for any new risks introduced during changes. This rigorous validation process, backed by expert analysis, gives you confidence in your improved security posture and demonstrates measurable progress in thwarting real-world threats.
Human Expertise Outsmarts AI
While AI tools offer speed in detecting known vulnerabilities, they fall short with 20-35% false positives and only 50-65% success on complex threats like business logic flaws, as per mainstream reports from Verizon and OWASP. Human penetration testers at Raxis deliver 85-90% detection rates, precise prioritization, and ethical adaptability, ensuring your organization stays ahead of real-world attacks.
Unlock Superior Security Insights
Raxis integrates cutting-edge AI into our red teaming processes to boost precision, uncover hidden vulnerabilities, and deliver transformative results that strengthen your defenses like never before.
MITRE ATT&CK Aligned Approach
Raxis structures our red teaming around the MITRE ATT&CK framework, ensuring every simulation mirrors advanced adversary tactics for precise vulnerability detection and robust defense strategies.
Expert US-Based Team
Our seasoned, US-based red team professionals bring years of hands-on experience, delivering ethical simulations that expose risks without disruption, all while prioritizing your organization’s unique security needs.

Red Teams, Blue Teams, And Purple Teams
The cybersecurity field has adopted the terms Red Teams, Blue Teams, and Purple Teams to categorize various methods of evaluating and enhancing an organization’s security.
- Red Teams simulate real-world attackers, constantly probing your defenses to find vulnerabilities before cybercriminals do.
- Blue Teams are your defenders, monitoring networks, detecting intrusions, and responding to incidents to keep your organization safe.
- Purple Teams bridge the gap between Red and Blue, fostering collaboration and continuous improvement. By sharing insights and working together, Purple Teams help both sides learn from each other, ensuring your security posture is always advancing.
Our Unique Edge
Uncovering What Others Miss
Many organizations rely on leading cybersecurity providers for their initial assessments—only to discover that complex threats and subtle vulnerabilities still remain undetected. Raxis Red Team is frequently called in after large, well-known competitors have completed their work, and time and again, we uncover critical security gaps that were completely overlooked.
Our approach is different: we don’t just scan for surface-level weaknesses. Instead, we simulate real-world adversaries, leveraging advanced techniques, persistence, and creativity to find hidden paths that could lead to a full compromise of your systems. Often, these vulnerabilities are not only missed by other teams but are the exact entry points that sophisticated attackers would exploit to move laterally, escalate privileges, and access sensitive data.
By focusing on stealth and persistence—much like actual cybercriminals—Raxis Red Team exposes flaws in your defenses that traditional testing simply doesn’t catch. Our findings frequently reveal just how close your organization might be to a serious breach, even after previous assessments by industry leaders. This makes Raxis Red Team the ultimate second opinion—and your best defense against threats that others fail to see.

The Digital Shoplifter
Raxis Hack Stories
Our stories are based on real events encountered by Raxis engineers; however, some details have been altered or omitted to protect our customers’ identities.
In a daring demonstration of cybersecurity vulnerabilities, the Raxis Red Team orchestrated a multi-stage attack that exposed critical weaknesses in a major retailer’s digital infrastructure. The operation began with our team targeting the company’s wireless network using the powerful Aircrack-ng suite. This versatile toolkit allowed us to capture the network’s encryption key during a routine handshake process and swiftly crack it using Hashcat’s advanced capabilities.
With network access secured, we obtained local system access and then pivoted to internal systems using CrackMapExec, a potent post-exploitation tool. We discovered a system protected by nothing more than a default password—a digital equivalent of leaving the keys in the ignition. This oversight became our gateway, allowing us to gain local administrator privileges. Using CrackMapExec’s –sam option, we dumped the local SAM hashes, further expanding our access.
Like master locksmiths, we moved from system to system, leveraging our newly acquired local admin rights. Eventually, we obtained a prized domain administrator hash. Overnight, our dedicated team worked tirelessly, using Raxis’ Hashcat multi-GPU system to break this high-value credential. Returning the next day, we validated our newfound domain administrative access, cementing our control over the retailer’s entire digital domain.
The crown jewel of our operation was the discovery of the application and database containing store-branded gift cards and PINs, along with the ability to generate new ones at will. This find not only highlighted the potential for financial exploitation but also underscored the critical importance of robust, multi-layered cybersecurity measures in today’s retail landscape.
