Penetration Testing for Software Development and DevSecOps

Raxis One is DevSecOps Ready
Protect your pipelines, repositories, and code from real-world attackers. Partner with Raxis for AI-powered penetration testing built for software development organizations.
Raxis provides unlimited Penetration Testing using a mix of AI and real ethical hackers.
Interface directly with our team to learn where gaps are and strategies to resolve.
Plug Raxis One directly into your DevSecOps workflow.
What is AI Augmented Penetration testing?
Why Penetration Testing Is Critical for DevSecOps
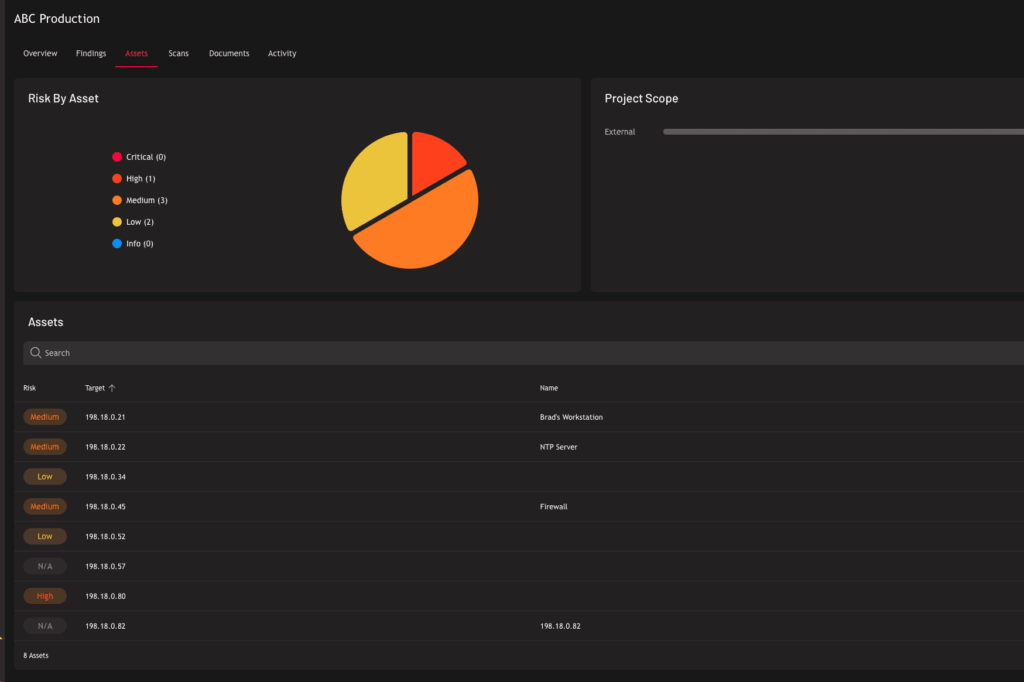
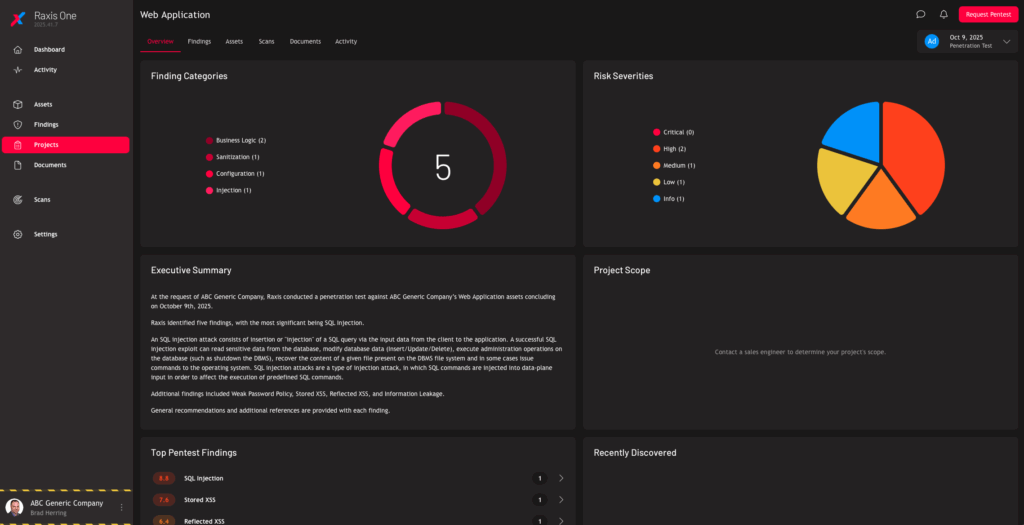
Penetration testing simulates real-world exploits against code repositories, build automation, APIs, and cloud systems. It validates the security of your development lifecycle from commit to deploy.
Source Code & Repo Security Testing
Secure GitHub, GitLab, Bitbucket, or on-prem SCM.
CI/CD Pipeline Security
Identify insecure tokens, plugins, and integrations.
Application & API Testing
Validate security before release.
Cloud Infrastructure Testing
Ensure secure configurations in AWS, Azure, and GCP.
Why Choose Raxis for Software Industry Penetration Testing
Raxis brings deep offensive security expertise and modern software fluency. Our testers understand how developers work—and how attackers think.
AI-augmented testing that accelerates vulnerability discovery
Specialists in code and CI/CD pipeline exploitation
Testing aligned with NERC CIP, ISO 27001, and ISA/IEC 62443
Safe testing in active development environments
Reports developers can act on, not just security teams
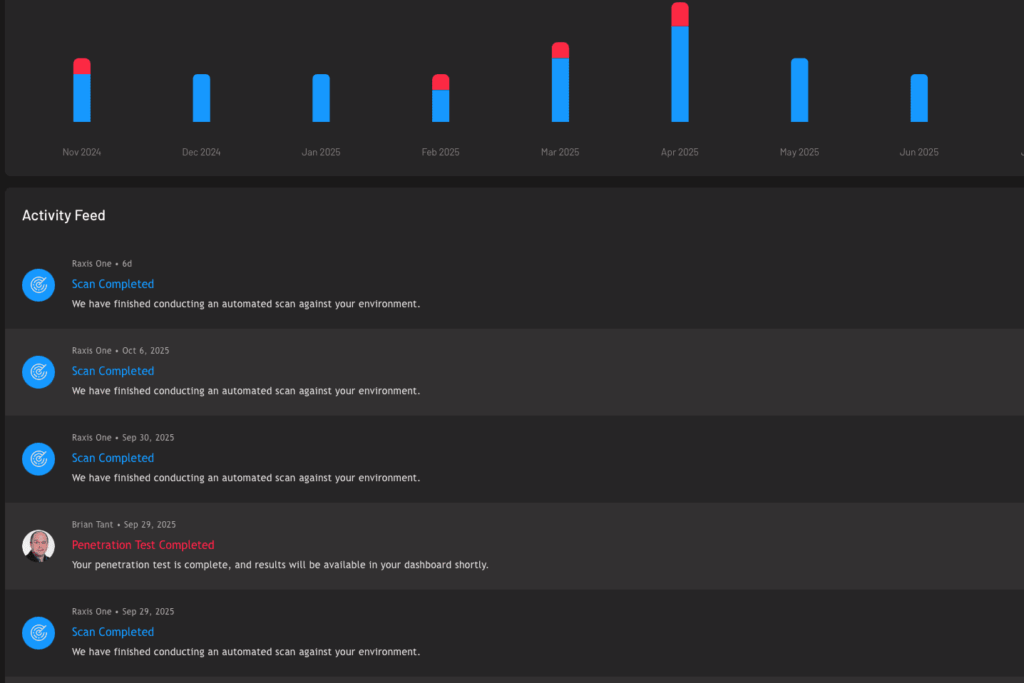
Continuous protection through Raxis Attack (PTaaS)
The Raxis Testing Process
Raxis brings unmatched experience in securing energy and critical infrastructure environments through human-led and AI-augmented penetration testing. Our experts understand the operational realities and regulatory frameworks that govern the sector.
Scoping & Planning
Define repo, pipeline, and application scope with your DevSecOps team.
Testing & Exploitation
Combine human expertise with AI-driven techniques to simulate real-world attacks.
Reporting
Deliver prioritized, developer-friendly findings with proof-of-concept detail.
Retesting
Verify that patches and configuration fixes are effective.