
Penetration Testing Services
As a leading penetration testing company, Raxis delivers expert-led, authorized cyberattacks.
Raxis Attacks. Raxis Protects.

Uncover Hidden Risk
Our penetration testing services pinpoint vulnerabilities in your systems before cyber attackers exploit them.

Adversarial Simulation
By simulating real-world attacks, companies can evaluate and improve their overall security strategies and controls.

Reduce Exposure Time
A Raxis Strike Penetration Test can preemptively identify security vulnerabilities, saving organizations from the devastating impact of data breaches, which on average take 277 days to detect and contain and cost $4.35 million.

Protect Your Brand
Raxis penetration testing services and the resulting attestation letter demonstrate your commitment to data security, helping build and maintain customer confidence in your brand.

Adhere to Regulatory Requirements
Penetration testing is an essential component of several regulatory compliance organizations, including PCI, HIPAA, GLBA, SOC 2, ISO 27001 and many others.

Justify Cybersecurity Spending
Safely demonstrating the effects of a real hack against your infrastructure is a highly effective method to justify the investment in cybersecurity.
Two Penetration Testing options
Raxis Attack
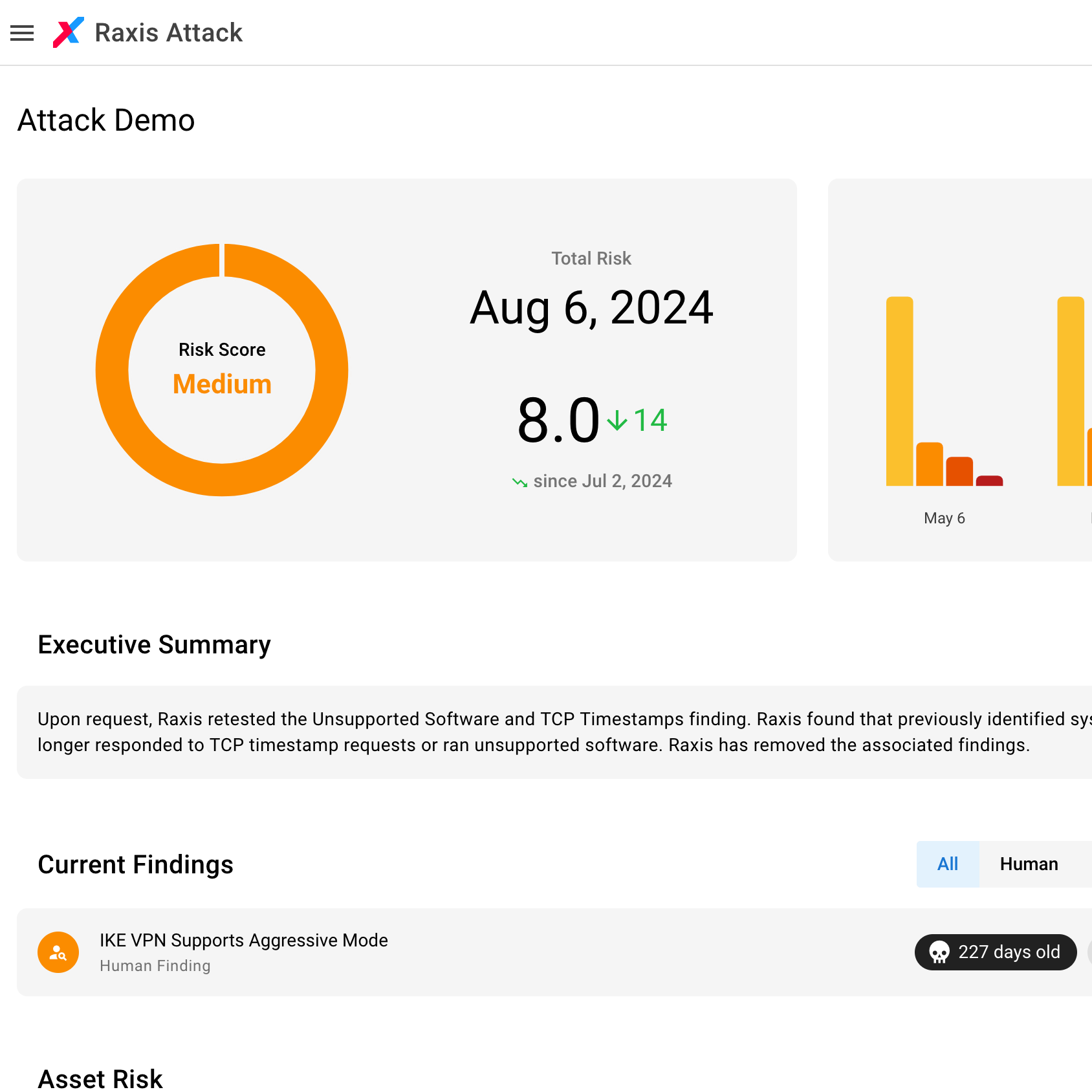
Penetration Testing As A Service (PTaaS)
Raxis Attack* delivers continuous security assessment, real-time feedback, and direct access to ethical hacking experts through a user-friendly platform built for DevSecOps. This includes providing unlimited PTaaS for external networks, internal/VPC networks, web applications, and APIs—seamlessly integrating into your pipeline.
*Raxis has been acknowledged as a Sample Vendor for Penetration Testing as a Service in Gartner’s 2024 Hype Cycle reports for Security Operations and Application Security.
Raxis Strike
Penetration Testing
Raxis Strike is a powerful penetration testing solution to uncover hidden vulnerabilities in your website through comprehensive, manual assessments conducted by our expert team. Our approach simulates real-world attack scenarios, providing in-depth insights and actionable recommendations to strengthen your security posture and ensure compliance with industry regulations.
You get more with Raxis
Our Proven Penetration Testing Methodology
For over 14 years, Raxis has been a trusted name in cybersecurity, delivering exceptional penetration testing through our Raxis Strike service. As a leading penetration testing provider, we partner with organizations across industries and sizes, using the industry-standard MITRE ATT&CK framework to guide our approach. Our US based expert team identifies and addresses vulnerabilities with precision, providing top-quality testing to strengthen your security.
The following process applies to Red Teaming, Traditional Penetration Testing, and our PTaaS options:
Scoping
Every organization faces unique security challenges, so we begin by working closely with you to define the scope of the penetration test. This includes identifying the systems, applications, or networks to be tested and setting clear objectives for the engagement. Whether you need an external network test, internal system evaluation, or application-specific assessment, we tailor our testing scenarios to align with your specific needs and industry requirements.
Intelligence Gathering
Raxis meticulously gathers and analyzes publicly available data about your organization and its employees to identify potential security risks. From public websites and social media profiles to domain registries and dark web sources, we uncover critical information that cybercriminals could exploit. Our expert team evaluates this data to detect vulnerabilities, such as exposed credentials or sensitive details, enabling you to mitigate risks before they’re weaponized.
Vulnerability Identification
Once the scope is defined, our expert penetration testers begin identifying vulnerabilities within your systems. Using a combination of manual techniques and advanced tools, we analyze your environment for weaknesses such as misconfigurations, outdated software, insecure protocols, or exploitable code. Unlike automated scans that often miss complex issues, our manual testing ensures a thorough assessment of even the most intricate systems.
Strategic Threat Modeling
Raxis elevates security through a dedicated threat modeling phase, meticulously designed to fortify your defenses. We begin by identifying and cataloging your critical assets, from infrastructure to data repositories. Next, we map potential threats, leveraging intelligence gathered from public sources, dark web data, and industry insights. Our experts then craft detailed attack plans, simulating real-world adversary tactics to expose vulnerabilities. This deliberate, proactive approach empowers your organization with actionable strategies to prioritize risks and strengthen resilience against sophisticated cyber threats.
Adversarial Simulation
To provide a realistic evaluation of your security defenses, we simulate real-world cyberattacks on your systems. Our team employs the same tools and techniques used by malicious hackers to test your organization’s ability to detect and respond to threats. These simulations include testing for common attack vectors such as phishing attempts, privilege escalation, lateral movement, and data exfiltration.
Exploitation
Within the parameters defined during scoping, we take testing a step further by safely exploiting identified vulnerabilities. This controlled exploitation demonstrates how attackers could leverage weaknesses to gain unauthorized access or exfiltrate sensitive data. By showcasing the potential impact of these vulnerabilities through detailed proof-of-concept scenarios, we help you understand their severity and prioritize remediation efforts effectively.
Impactful Post-Exploitation Analysis
Raxis demonstrates the real-world consequences of a breach through meticulous post-exploitation testing. We assess the value of compromised systems based on the sensitivity of stored data and their potential to enable further network attacks. Using manual techniques that mirror current threats, we simulate pivoting, privilege escalation, and data compromise to highlight critical risks. Where applicable, we safely exfiltrate and redact data to underscore true exposure, providing clear, actionable insights to strengthen your defenses against sophisticated adversaries.
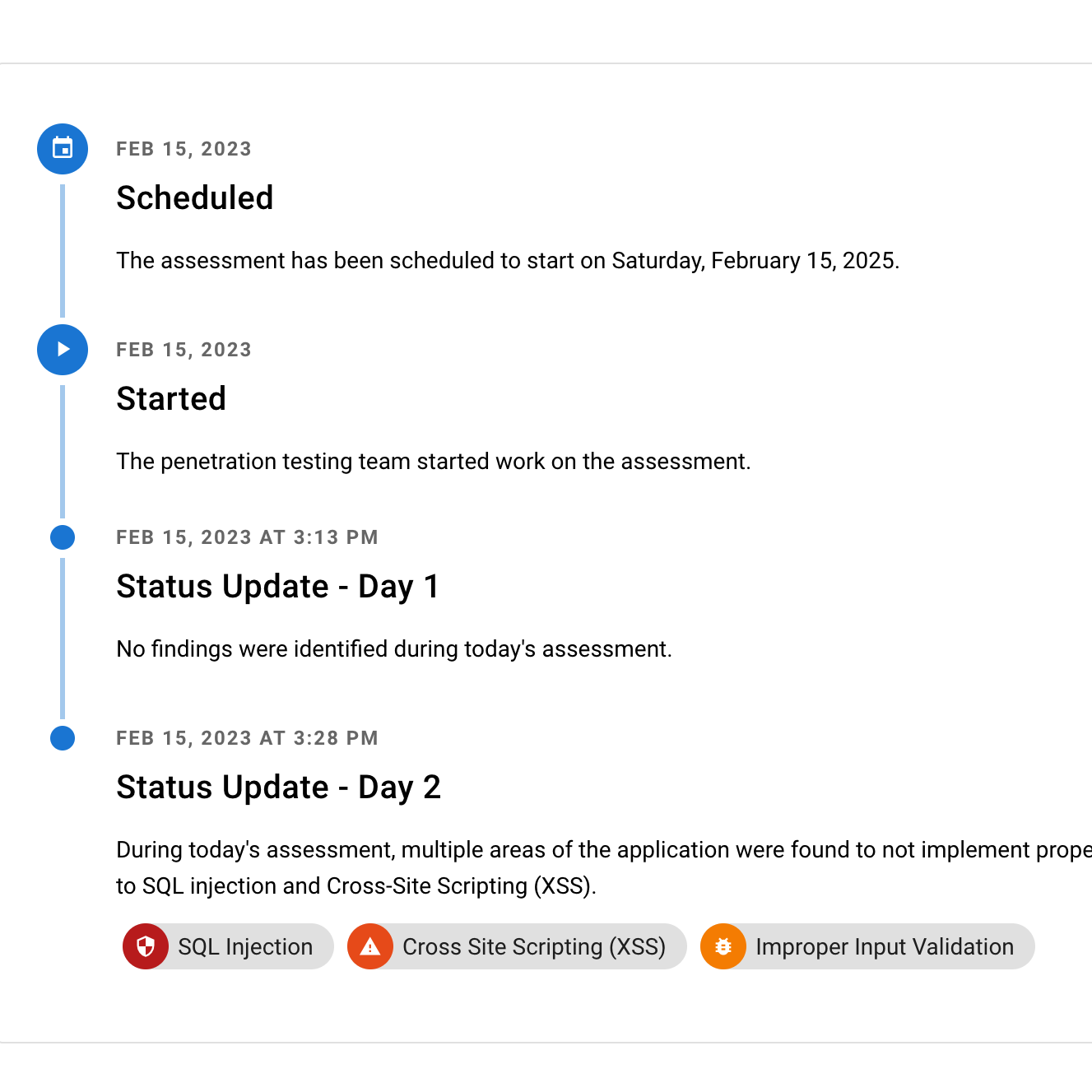
Reporting
At the conclusion of testing, you receive a comprehensive report detailing all findings from the engagement. This report includes a prioritized list of vulnerabilities categorized by severity level (e.g., critical, high, medium), along with their associated risks and potential business impact. Each finding is accompanied by proof-of-concept exploits and clear remediation recommendations tailored to your technical team’s needs. Additionally, we provide a detailed storyboard that illustrates how an attacker could exploit multiple vulnerabilities in sequence.
Actionable Advisory and Remediation Planning
Raxis goes beyond reporting vulnerabilities—we partner with you to build a stronger security posture. In our comprehensive debrief session, our experts guide you through penetration test findings, clarifying results and answering your questions in detail. We provide tailored, actionable recommendations to address vulnerabilities effectively and prioritize remediation efforts. By collaborating on a strategic remediation plan, we empower your team to mitigate risks efficiently, ensuring your organization is equipped to maintain robust defenses against evolving cyber threats.
Thorough Retest Validation
Raxis ensures your remediation efforts are effective with our comprehensive retesting services. We meticulously re-evaluate previously identified vulnerabilities to confirm they have been fully resolved and are no longer exploitable. Our rigorous process also verifies that no new risks have emerged during remediation, providing you with confidence in your strengthened security posture. With Raxis’ retesting, you gain assurance that your organization is protected against evolving threats, backed by thorough validation and expert analysis.
AI-Enhanced Reporting
Raxis uses cutting-edge AI to streamline our penetration testing reports, providing clear, actionable insights to boost your security. We keep your data safe with strict privacy controls and never use it for AI training, ensuring your confidence and trust.
Realistic Attack Simulations
Unlike traditional vulnerability scans, Raxis Strike employs ethical hackers who simulate sophisticated cyberattacks using actual hacker-created exploits. These simulations provide invaluable insights into how attackers could compromise systems, escalate privileges, and exfiltrate sensitive data.
Tailored Testing for Unique Needs
Every organization has unique security challenges based on its infrastructure, industry, and compliance requirements. Raxis Strike customizes its penetration tests to align with the customer’s specific environment, ensuring maximum relevance and effectiveness. Whether testing external networks, APIs, mobile applications, or IoT devices, the service adapts to meet diverse technology landscapes.
Industry-Specific Expertise
Raxis brings industry-specific knowledge to every engagement, efficiently targeting vulnerabilities that are unique to the customer’s sector. This expertise ensures compliance with regulatory standards such as PCI DSS, HIPAA, GDPR, and ISO 27001 while addressing sector-specific risks.
Black Box, White Box, and Grey Box Penetration Testing
Raxis penetration testing services are designed to uncover vulnerabilities and strengthen your defenses against real-world cyber threats. As a trusted penetration testing company, we adapt our expert-led assessments to your unique needs using industry-standard methodologies: Black Box, White Box, and Grey Box testing. Each approach provides a distinct perspective, ensuring comprehensive coverage—whether we’re simulating an external hacker or diving deep into your systems with your team’s collaboration. Each style applies to Red Teaming, Traditional Penetration Testing, and our PTaaS options.
Black Box Penetration Testing
Raxis Black Box penetration testing mimics external attackers with no system knowledge, targeting public-facing assets like web apps, networks, and APIs. Our ethical hackers uncover perimeter defense weaknesses automated tools miss, ideal for testing external security posture.
Grey Box Penetration Testing
Raxis Grey Box testing blends limited system knowledge with external attack methods. Using partial info like credentials, our experts simulate targeted breaches, identifying vulnerabilities from misconfigurations and exploits. Offers realistic assessments and remediation steps, ideal for tailored penetration testing.
White Box Penetration Testing
Raxis White Box testing provides an in-depth system review. Certified experts, with full access to source code, configurations, and architecture, simulate advanced threats like insider attacks or breaches with stolen credentials. This thorough approach uncovers all vulnerabilities, ideal for businesses requiring comprehensive cybersecurity testing for PCI DSS, HIPAA, or SOC 2 compliance.
