CVE-2022-26653 & CVE-2022-26777: ManageEngine Remote Access Plus Guest User Insecure Direct Object References
Raxis lead penetration tester Matt Dunn uncovers two more ManageEngine vulnerabilities (CVE-2022-26653 & CVE-2022-26777).
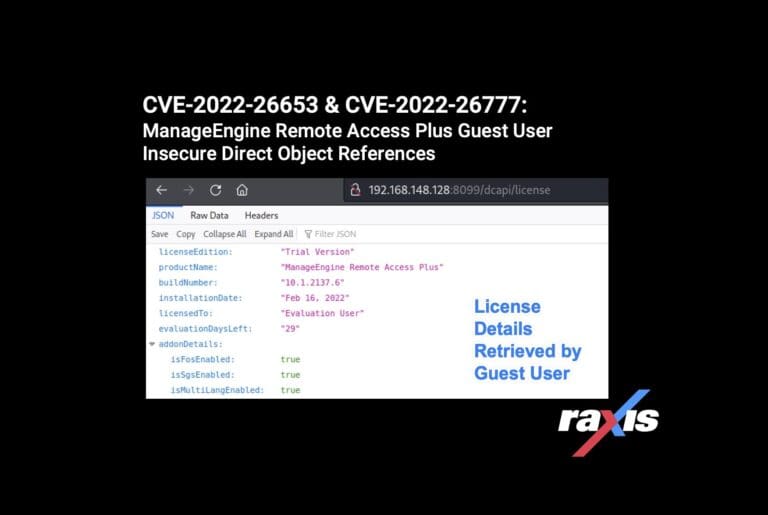
Raxis lead penetration tester Matt Dunn uncovers two more ManageEngine vulnerabilities (CVE-2022-26653 & CVE-2022-26777).
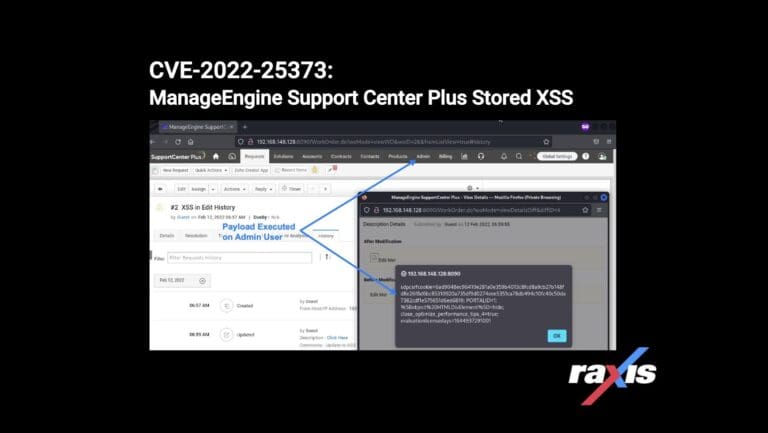
Matt Dunn discovers another ManageEngine Cross-Site Scripting vulnerability, this one in the Support Center Plus application.
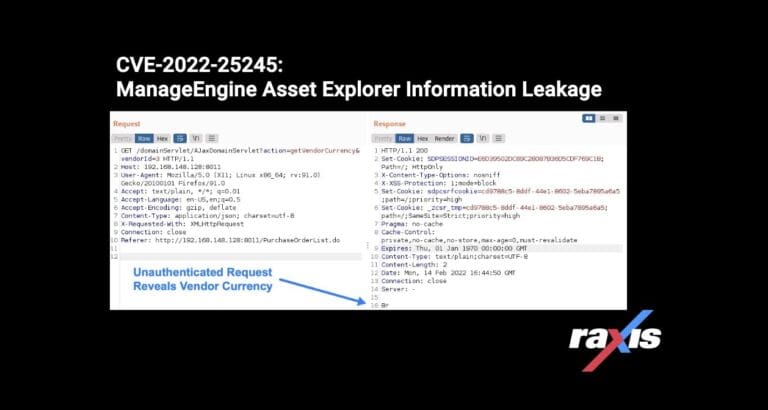
Raxis lead penetration tester Matt Dunn discovers an information leakage vulnerability in ManageEngine’s Asset Explorer CVE-2022-25245
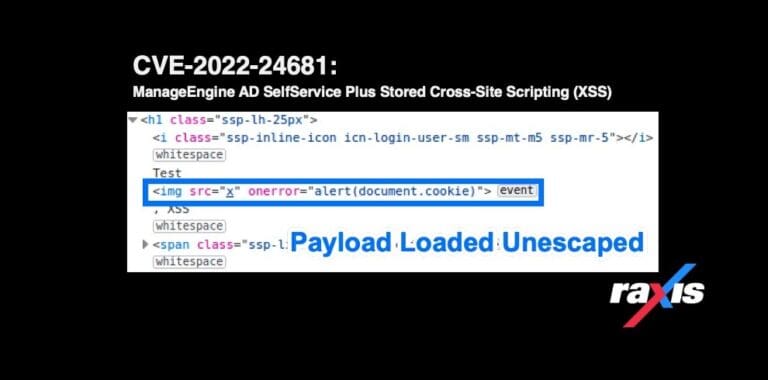
Raxis’ Matt Dunn continues his prolific discovery of new CSS CVEs. This one affects ManageEngine AD SelfService Plus Stored Cross-Site Scripting.
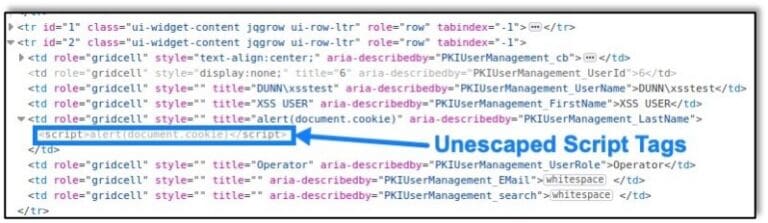
Raxis’ Lead Penetration Tester Matt Dunn discovers another cross-site scripting vulnerability in Zoho’s MangeEngine Key Manager Plus (CVE-2021-28382).