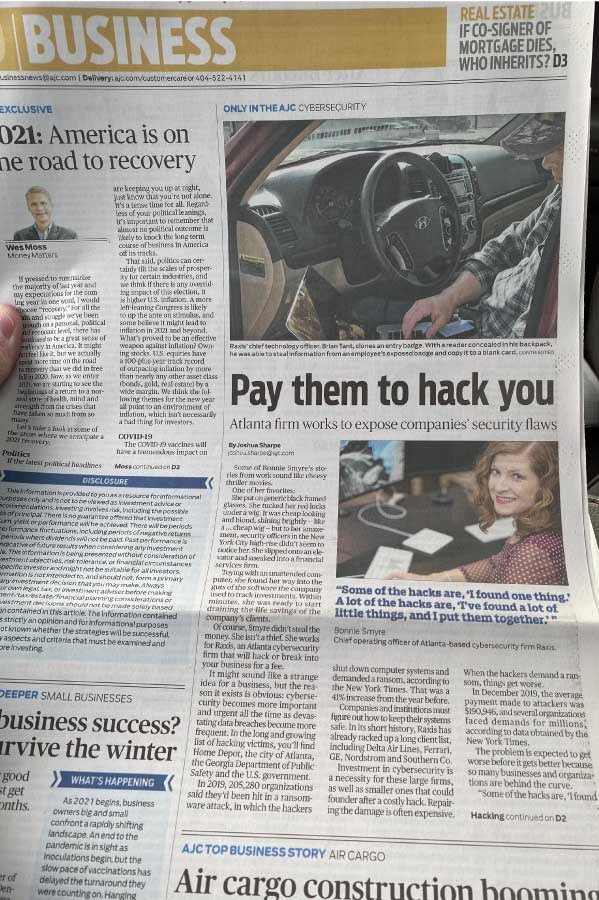
What is Attack Surface Management (ASM)?
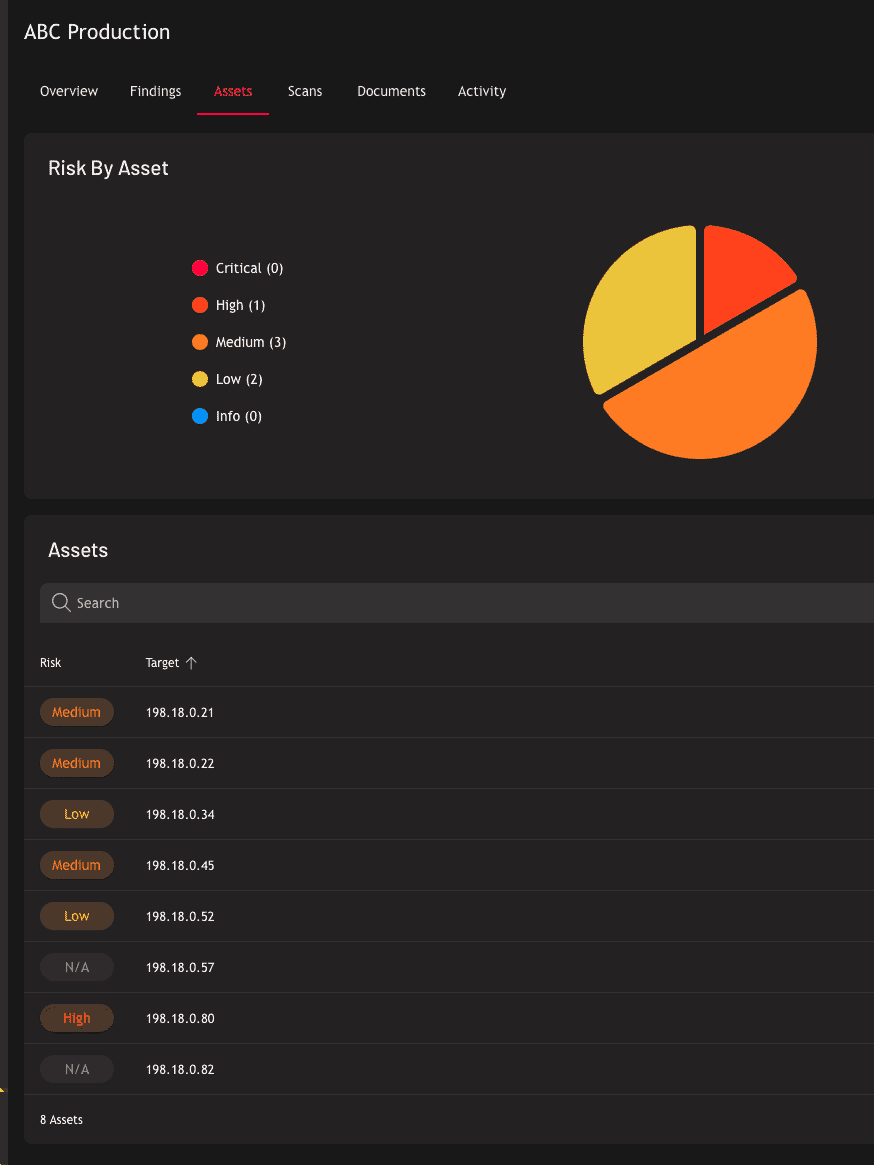
Expert-Led Attack Surface Management
Most ASM Tools are Automated Scanners. Raxis Brings Penetration Testing Expertise.
Benefits of Expert-Led Attack Surface Management
Our breach and attack simulation services are conducted by the same elite penetration testers who perform Red Team operations for Fortune 500 companies.
Complete Visibility
Discover all internet-facing assets, including forgotten servers, shadow IT, cloud resources, and third-party services that traditional inventories miss.
Proactive Risk Reduction
Address vulnerabilities and exposures before attackers find them, reducing your organization’s overall attack surface and breach likelihood.
Compliance Support
Demonstrate due diligence and asset awareness for PCI DSS, HIPAA, SOC 2, ISO 27001, GDPR, and other frameworks requiring attack surface management.
Merger & Acquisition Support
Assess the security posture of acquisition targets or identify inherited risks from merged companies, including rogue assets and undisclosed infrastructure.
Third-Party Risk Management
Understand your exposure through vendors, partners, and subsidiaries whose security posture extends your attack surface.
Continuous Improvement
Track your attack surface over time, measure reduction efforts, and demonstrate security posture improvements to leadership and stakeholders.
Attack Surface Management Engagement Options
Continuous ASM
Ongoing monitoring and assessment through our Raxis Attack platform, with automated alerts for new assets, emerging threats, and configuration changes.
Duration: Subscription-based
Best For: Dynamic environments, continuous compliance, proactive security
M&A Due Diligence
Rapid assessment of acquisition targets to identify hidden infrastructure, security debt, and inherited risks before the deal closes.
Duration: 1-2 weeks
Best For: Pre-acquisition, merger integration, subsidiary assessment
ASM + Penetration Testing
Combine attack surface discovery with targeted penetration testing on high-risk assets for maximum security validation.
Duration: 3-6 weeks
Best For: Comprehensive security assessment, high-risk environments
Why Choose Raxis for Attack Surface Management?
With Raxis Attack Surface Management, we use AI to accelerate reconnaissance, pattern detection, and initial scans—then our experts take over.
Penetration Testing Expertise
Attacker Methodology
AI-Augmented Efficiency
U.S.-Based Team
14+ Years of Experience
Actionable Intelligence