AI-Augmented Series: AI Scripting for Brute-Forcing on a Web App Pentest
On a recent web app pentest, Andrew Trexler used AI to find client-side code that stopped his brute-force attack then used AI again to thwart that code.
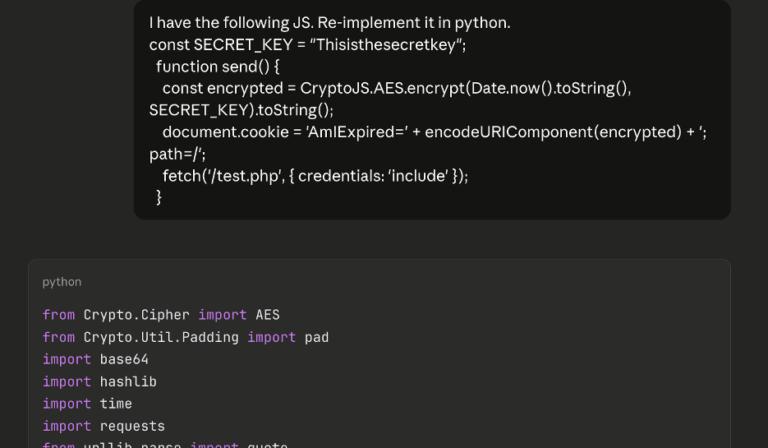
On a recent web app pentest, Andrew Trexler used AI to find client-side code that stopped his brute-force attack then used AI again to thwart that code.
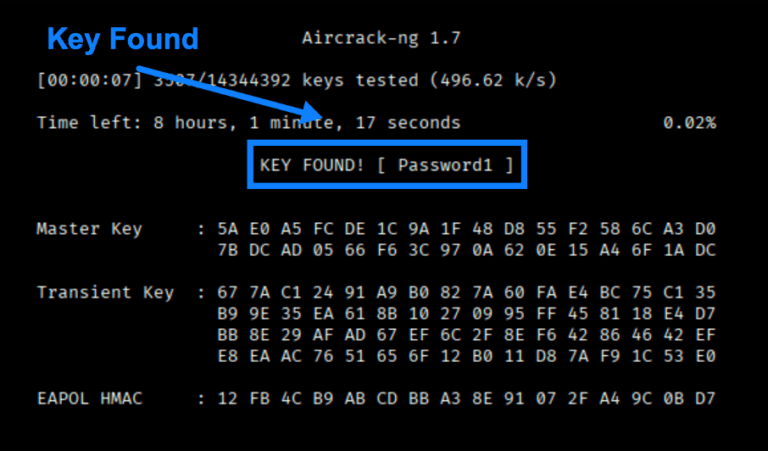
Principal Penetration Tester Scottie Cole continues our wireless series with the Aircrack-ng Suite, a set of tools for wireless pentest discovery and exploits.

Raxis’ Jason Taylor is back with a detailed tutorial on performing both manual and automated DNS exfiltration attacks for pentesting.

With the start of 2026, the Raxis team is already busy. A new upgrade to our password-cracking system shows how quickly 8-character passwords can be cracked.

Raxis CEO Mark Puckett looks back at a year of many changes and forward to the ways AI-augmented pentesting is changing the industry.