Advanced Penetration Testing for Networks, Apps, and APIs
Born from the hacker mindset. Built for penetration testing service excellence.
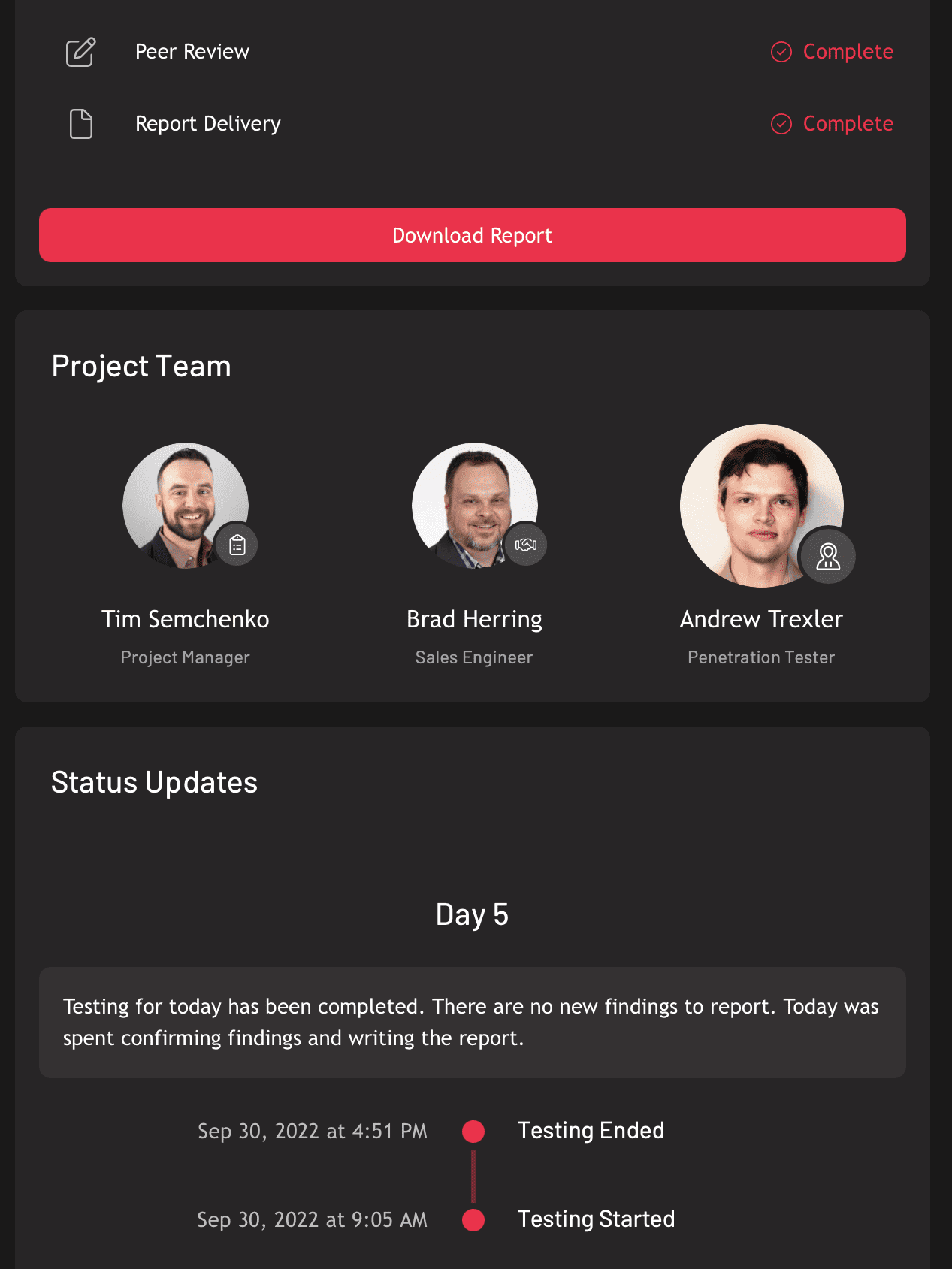
Two Penetration Testing Approaches
Raxis offers unlimited continuous penetration testing services as well as point in time assessments.

Penetration Testing Reveals More Than Vulnerability Scans
Vulnerability scans provide a solid foundation and meet basic compliance needs, and often is performed by the customer. Penetration testing delivers deeper assurance by proving what attackers could actually achieve.
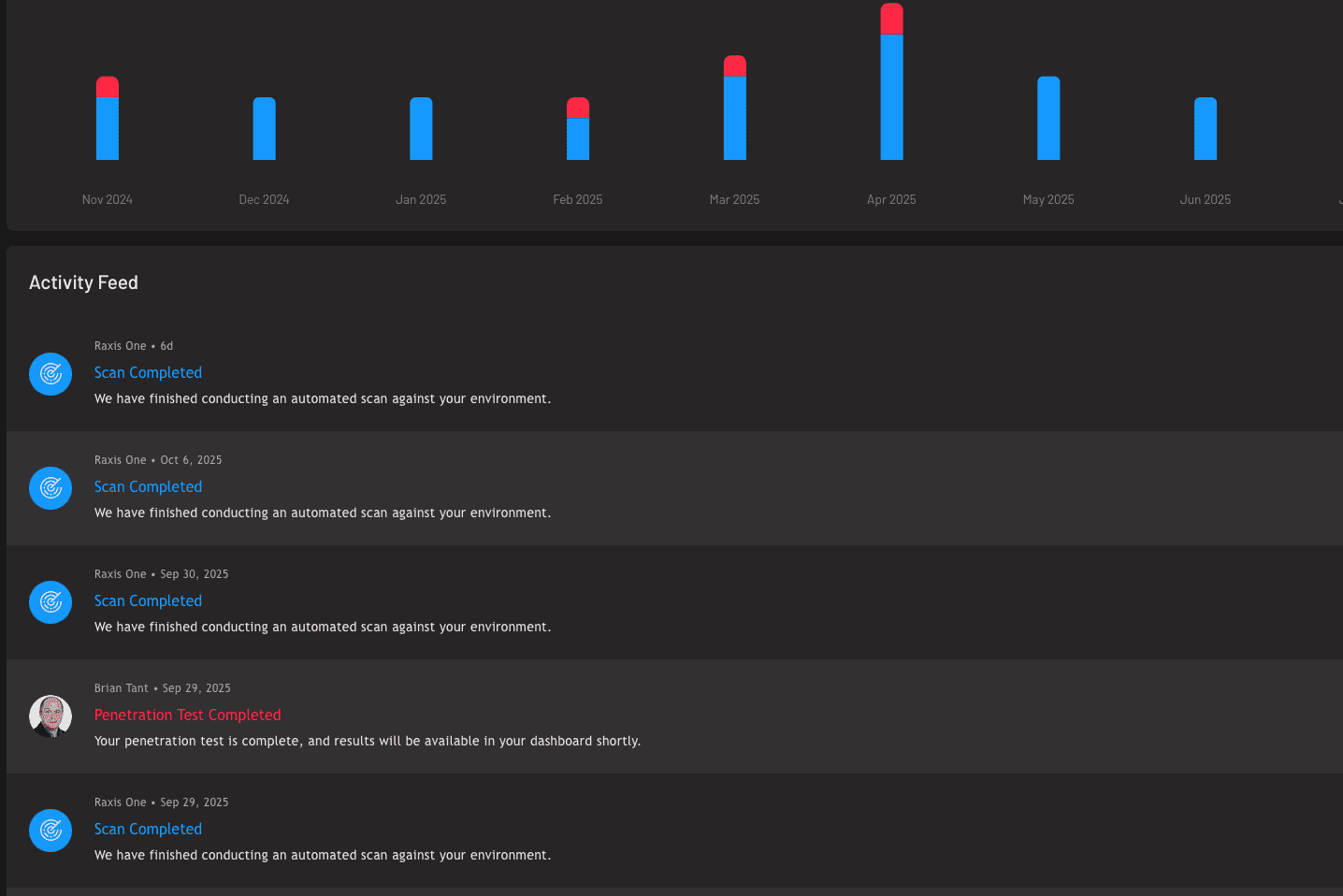
Types of Penetration Testing Services
Applicable to both Raxis Strike and Raxis Attack (PTaaS), our engineers are well versed in all types of systems and technologies.
Achieve and Maintain Compliance with Expert Penetration Testing
Meet rigorous standards like PCI DSS Requirement 11.3, SOC 2 Trust Services Criteria, and HIPAA Security Rule through Raxis’s human-led, AI-enhanced testing.
CCPA/CPRA (2020/2023)
Raxis helps California-focused businesses meet CCPA/CPRA “reasonable security” requirements with comprehensive penetration testing. We uncover vulnerabilities in systems handling personal information, providing executive-level reports and fix validation to support risk assessments and minimize exposure to lawsuits.
New York SHIELD Act (2019)
Raxis ensures SHIELD Act compliance for organizations handling New York residents’ data through rigorous penetration testing. Our methodical approach exposes weaknesses in web applications and security systems, delivering quantifiable risk insights and retesting to help you maintain reasonable safeguards.
Massachusetts Data Security Regulation (2010)
Raxis fulfills Massachusetts 201 CMR 17 requirements with expert penetration testing and ongoing monitoring of systems containing residents’ personal information. We provide thorough assessments and clear remediation plans to demonstrate effective security controls and prevent breach notifications.
FTC Act – Section 5
Raxis aligns penetration testing with FTC “reasonable security” expectations, as outlined in Start with Security. Our real-world simulations identify exploitable gaps in consumer-facing web applications, supplying defensible evidence and guidance to help you avoid enforcement actions.
ISO/IEC 27001:2022
Raxis supports ISO 27001 certification and ongoing compliance with Annex A.12.6.1-compliant penetration testing. Our skilled engineers deliver comprehensive assessments across your ISMS scope, identifying vulnerabilities and providing prioritized recommendations to maintain a robust information security management system.
NIST SP 800-115
Raxis follows NIST SP 800-115 guidelines to deliver technically sound penetration testing for federal, healthcare, and financial clients. Our human/AI hybrid methodology uncovers hidden risks in web applications and infrastructure, producing detailed reports that align with FISMA, HIPAA, and FedRAMP requirements.
OWASP Testing Guide
Raxis leverages the OWASP Testing Guide as a foundation while enhancing it with expert manual testing and AI augmentation. We thoroughly assess web applications for top risks like XSS and SQL Injection, delivering deeper insights and actionable fixes that elevate your security beyond standard compliance.
PTES
Raxis adheres to the Penetration Testing Execution Standard (PTES) framework for structured, comprehensive engagements. Our experienced team executes all seven phases with precision, uncovering complex vulnerabilities and providing enterprise-grade reports that support ISO 27001, NIST, and regulatory compliance.
OSSTMM
Raxis incorporates OSSTMM’s scientific methodology to deliver quantifiable, repeatable penetration testing results. We measure operational security across channels—including web applications—providing risk scores and evidence-based recommendations that strengthen compliance with ISO 27001 and critical standards.
FINRA Cybersecurity Guidelines
Raxis helps broker-dealers meet FINRA cybersecurity expectations with targeted penetration testing of trading platforms and investor-facing web applications. We identify real exploitable risks and provide clear, actionable reports to protect sensitive data and maintain regulatory confidence.
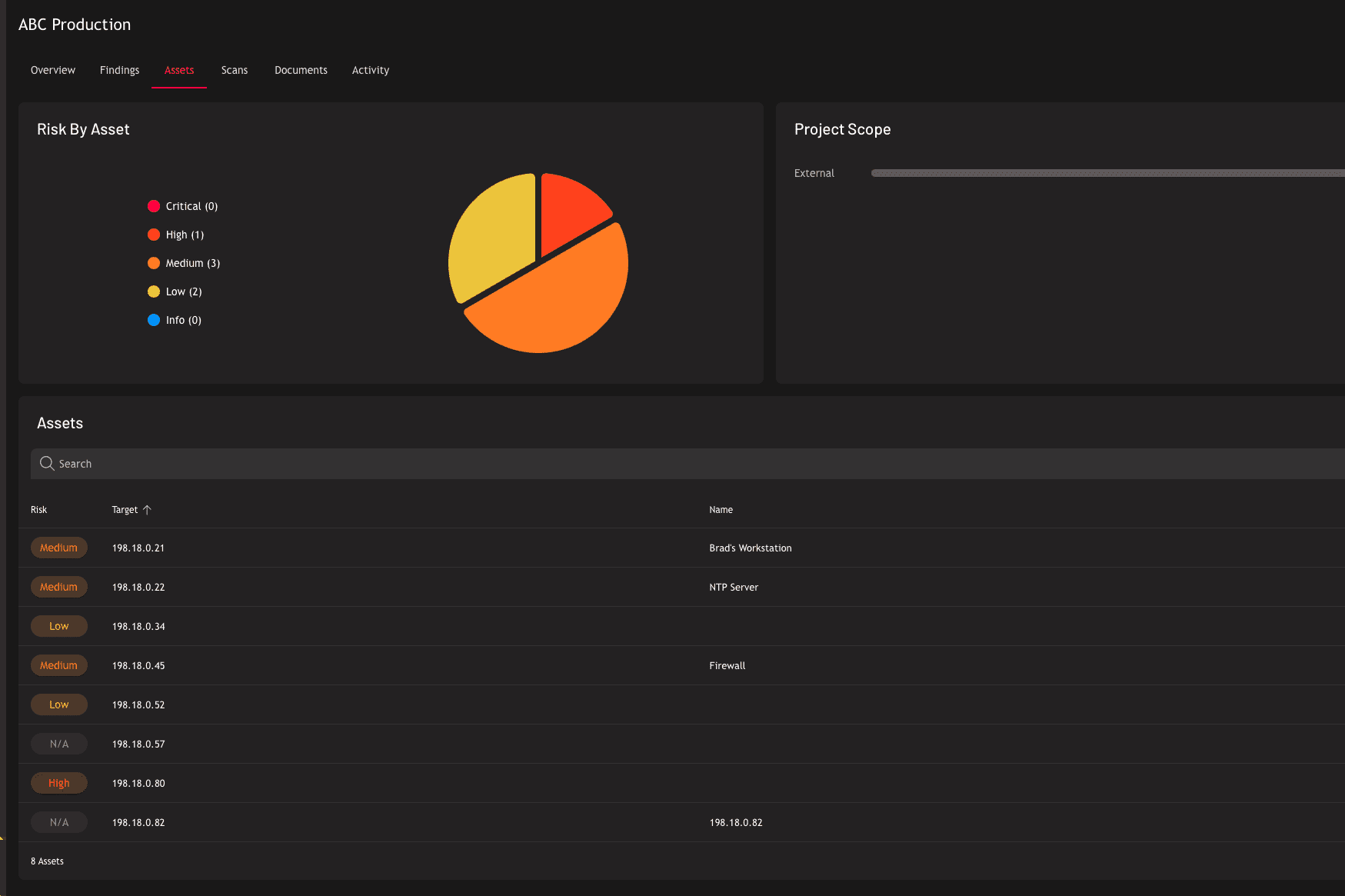
Penetration Test Feature Comparison
|
Feature |
Strike |
Attack |
Red Team |
|---|---|---|---|
|
Certified, U.S. Based Engineering Team | |||
|
Unlimited Remediation Support | |||
|
Free Manual Retest | |||
|
Supports Transporter Remote Testing | |||
|
Dedicated Project Manager | |||
|
Raxis One Platform Access | |||
|
Professional, NIST Compliant Reports | |||
|
Unlimited Penetration Testing | |||
|
Attack Surface Management and Ongoing Tracking | |||
|
Work Off Hours to Fit Time Zones | |||
|
Report Review Sessions |
1 |
Unlimited |
3 |