Attack Surface Management
Raxis One allows you to Discover, Analyze, and Monitor assets across your platform.
This Is What Attack Surface management Was Meant to Be
Unrivaled Penetration Testing
The Raxis Pentest Team uses the same techniques that today’s malicious hackers use, including detection evasion, recent exploits, social engineering, and chained attacks. This is not a vulnerability scan, as our pentesters will breach your perimeter, pivot to other opportunities, exfiltrate critical data, obtain and crack password hashes, and demonstrate how a foothold would be maintained.
Advanced Social Engineering
Social engineering is a powerful attack vector that targets the greatest weakness in any organization: its people. Whether it’s through phishing, smishing, vishing, whaling, direct interaction, or other pretext, a well-executed social engineering test can manipulate your employees to reveal sensitive data in ways you never imagined.
Security Framework Analysis
A robust enterprise solution that gets down to brass tacks, we map your policies and procedures’ maturity across industry standard security controls. An extensive interview and documentation process leaves no stone unturned. Your greatest strengths, weaknesses, and all points between are spelled out in a detailed gap analysis and roadmap.
Red Team Assessment
In most of our Red Team assessments, physical security is deemed in scope to gain a full view of every potential avenue of attack. We test physical security to ensure that intruders can’t gain access to systems that may be protected by physical access controls. This often includes badge readers, wireless networks, electronic door locks, and network-connected cameras.
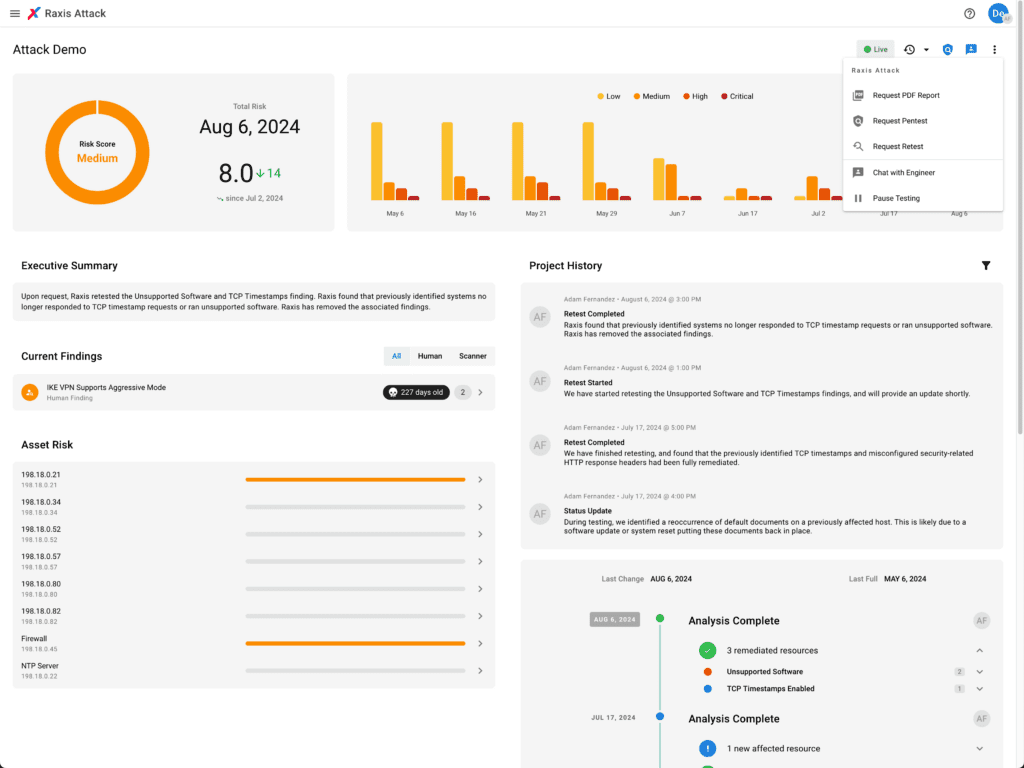
See Your Attack Surface Like Never Before
Use Raxis One, our innovative console for Attack Surface Management, to manage the latest details on your attack surface in real time, prioritize remediation, and easily retest your technology platforms.
Every Asset in View
At Raxis, we get it. Cybersecurity can seem like a never-ending battle, and it’s easy to retreat into safe harbors and big-box, checkbox solutions.
With your reputation and your revenue at stake, however, it makes sense to bring on a partner who understands what you’re up against and who can help you focus your resources where they are most effective in terms of both cost and security.
This is where Raxis shines. We see security differently because our team includes some of the most skilled and experienced certified hackers in the world. We have former IT and database administrators, system admins, software developers and architects, embedded device and IoT experts, as well as corporate cybersecurity leaders, internal red team and blue team members, and even fireworks specialists and improv performers.
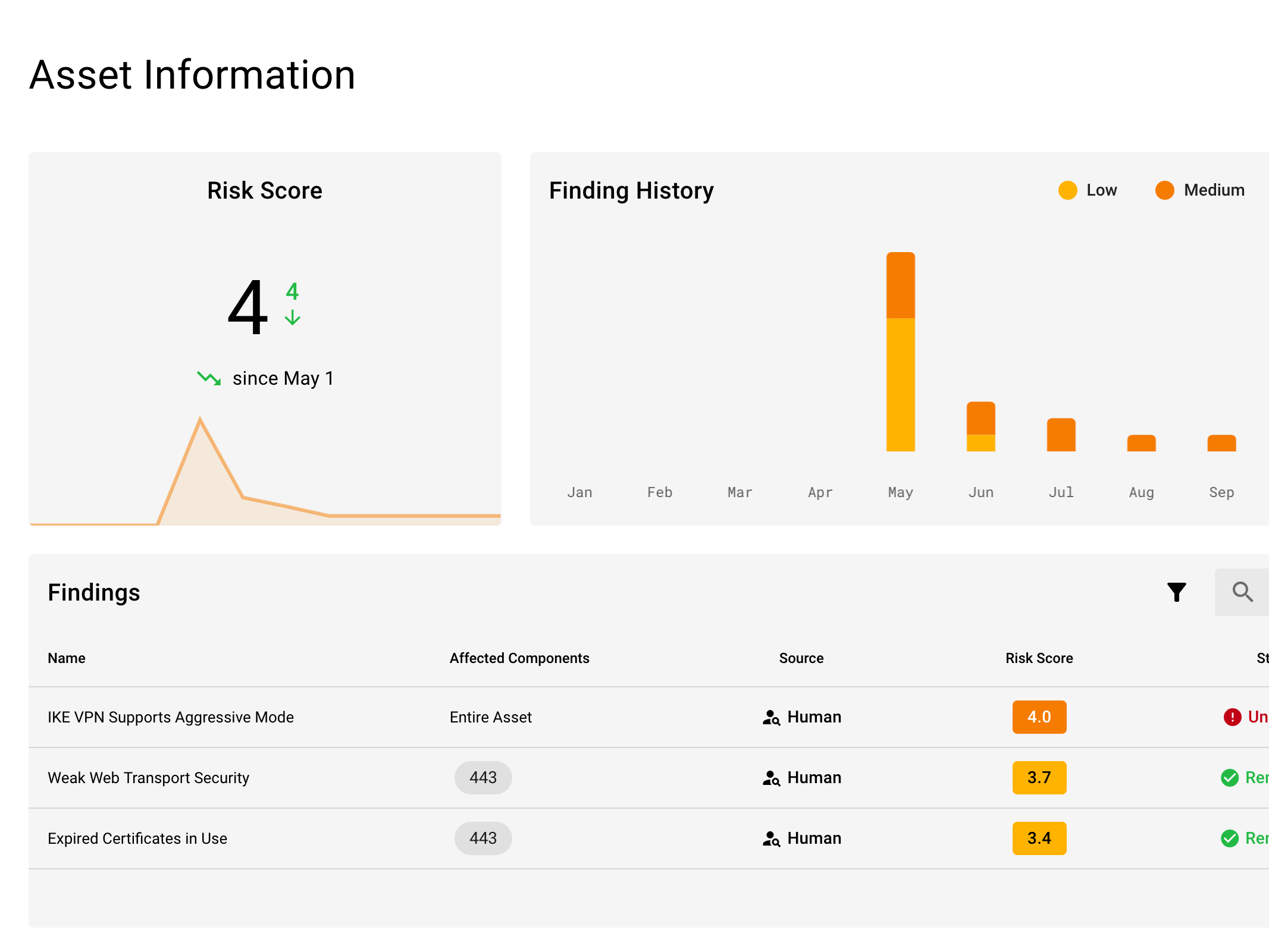
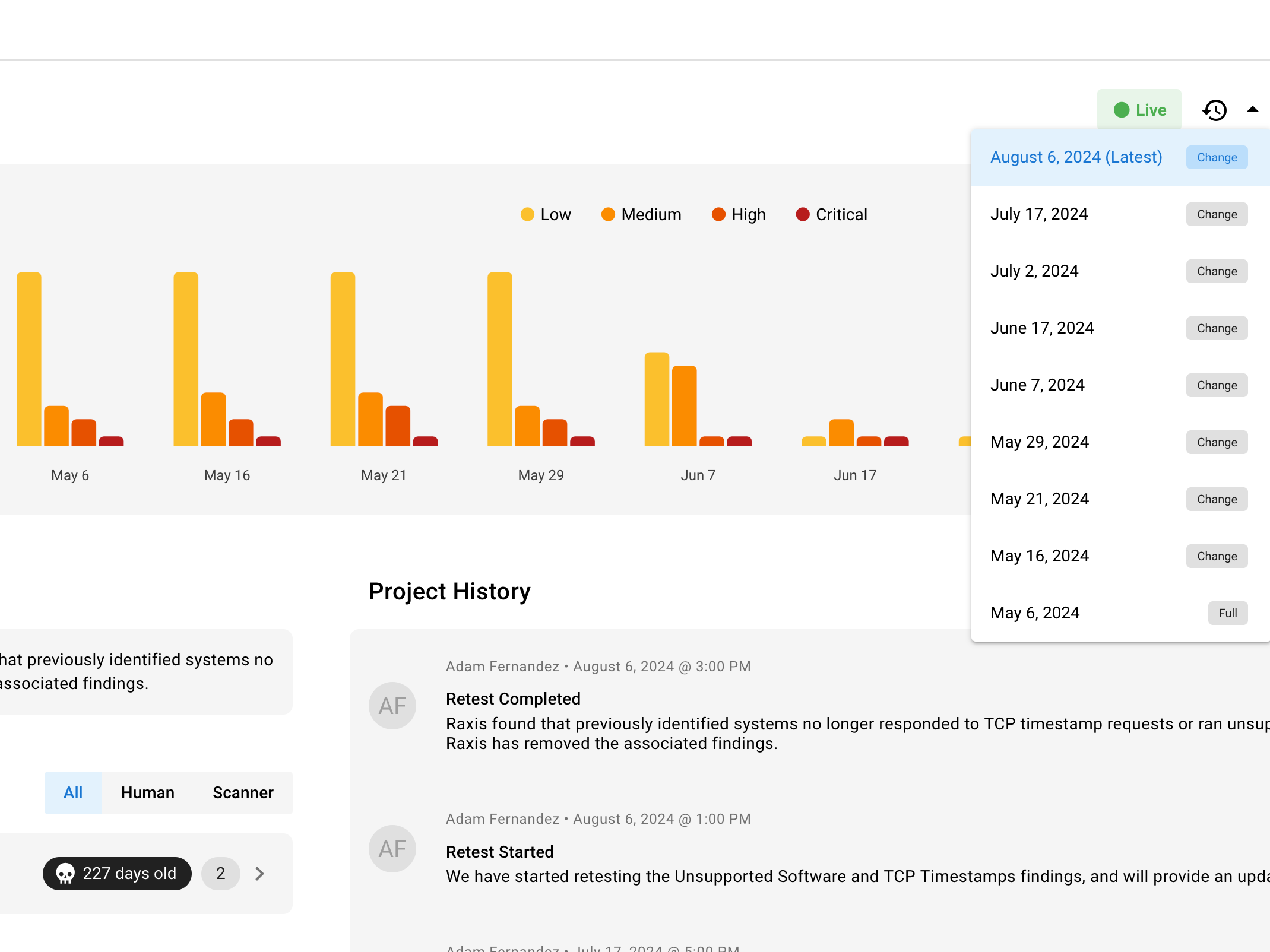
Scanning Isn’t Seeing
Much of the conversation around Attack Surface Management involves staying ahead in a technological arms race. Companies, including Raxis, are turning more to automation to stay ahead of the threats. But there is a tremendous difference between set-it-and-forget-it tech and integrated systems that extend the capabilities of human experts.
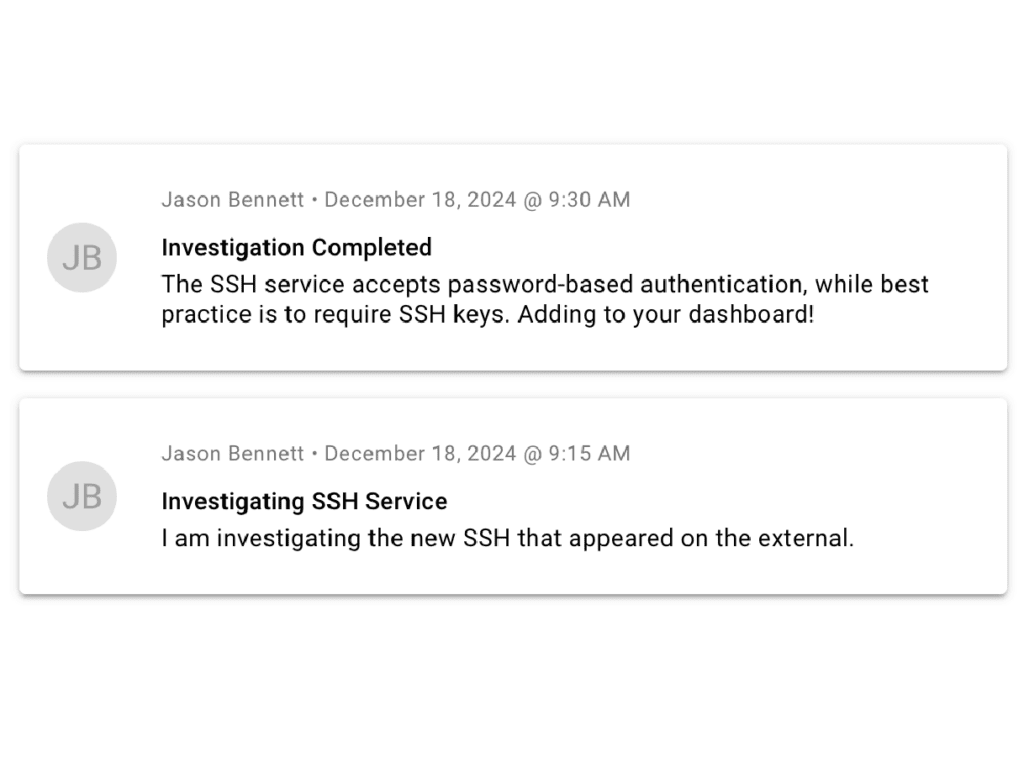
- Time Machine – Raxis One enables you to track the evolution of your threat landscape over time, showcase its value to your team, and implement proactive risk mitigation strategies by leveraging real-time threat intelligence updates.
- Penetration Testing – Prove the vulnerability is a threat to your environment and demonstrate potential impact, uncover additional risks that scanners miss, and learn how to properly remediate findings.
- Access to an Engineer – Gain expert human insight into identifying, prioritizing, and addressing vulnerabilities that automated tools often miss, enabling teams to proactively secure applications, networks, and systems against real-world threats.
Human Powered Automation
Corporate security isn’t capture-the-flag. Hackers don’t stop just because they’ve successfully penetrated your network.
Automation tools, while efficient and fast, lack the ingenuity, adaptability, and creativity of real hackers. They follow predefined rules and algorithms, which makes them excellent at identifying known vulnerabilities but incapable of uncovering complex, context-specific weaknesses or anticipating novel attack vectors. This is where Raxis steps in, leveraging the expertise of seasoned penetration testing engineers who think and act like real attackers. These professionals simulate sophisticated, real-world attack scenarios that automated tools simply cannot replicate, uncovering hidden vulnerabilities that could otherwise remain undetected.