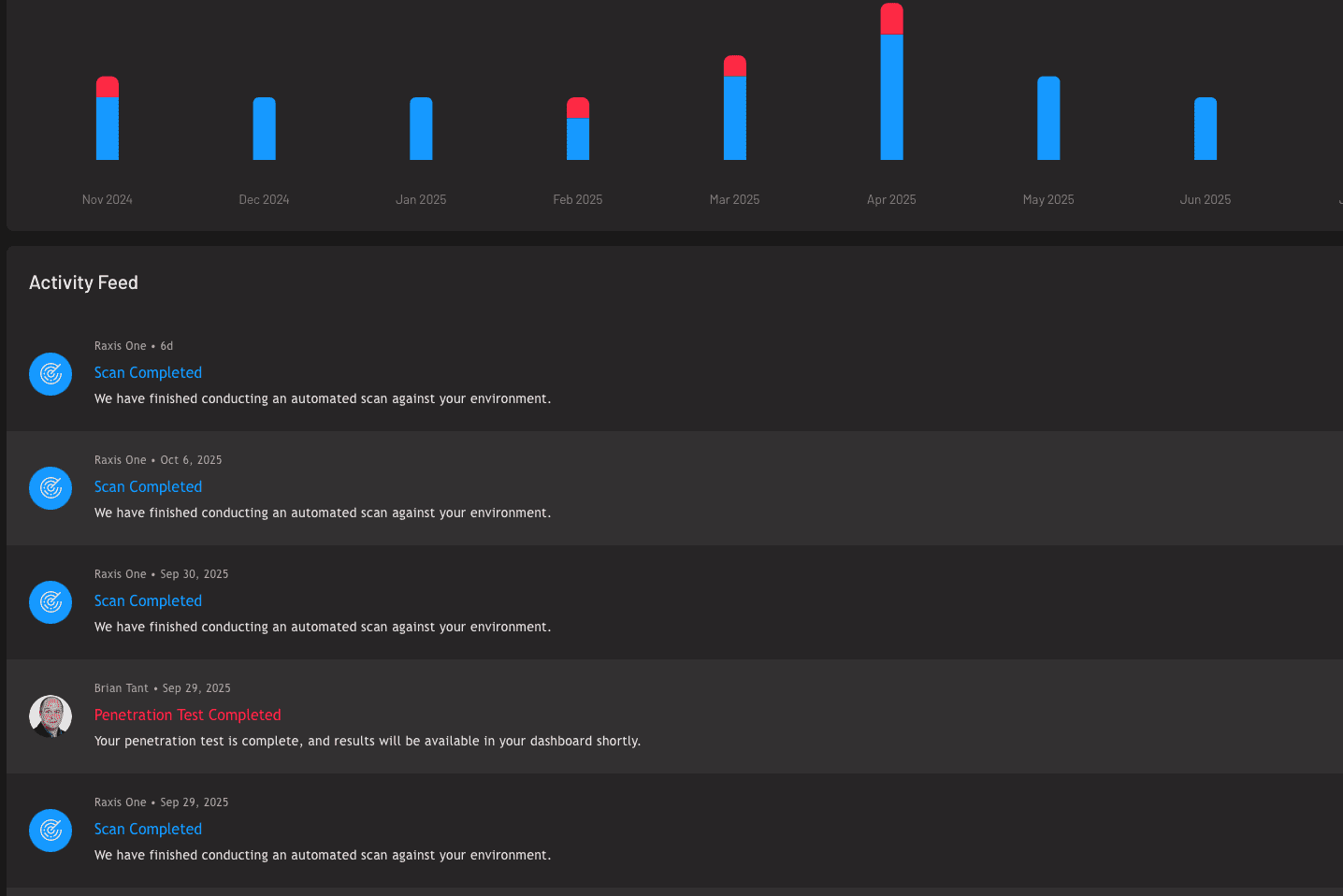
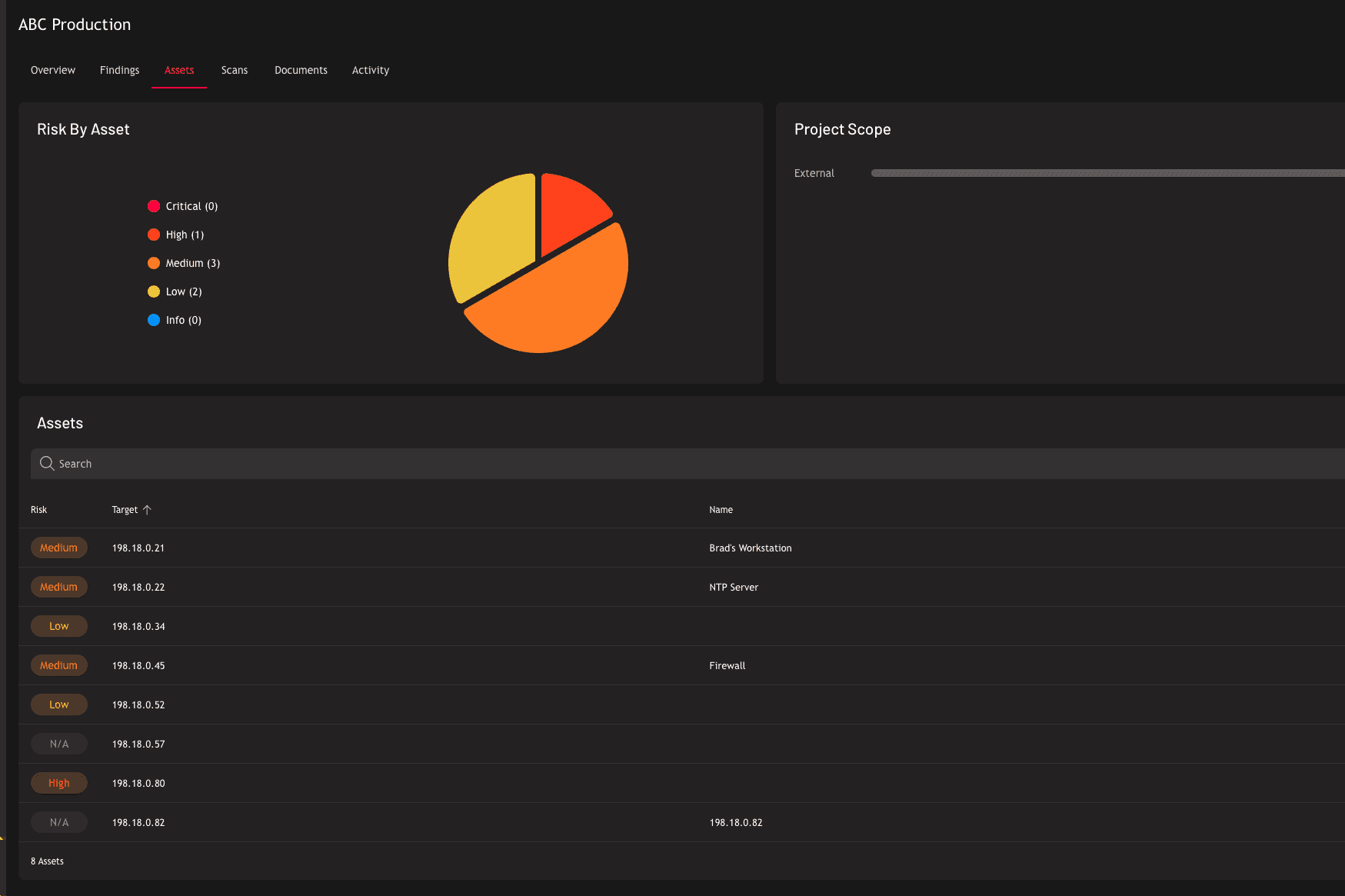
Penetration Testing as a Service (PTaaS)
Annual pentests leave you blind 364 days a year. Raxis Attack keeps you covered every single one.
Your Attack Surface Changes Faster Than Annual Tests Can Keep Up
New code ships daily. Cloud environments shift weekly. Attackers don’t wait for your next scheduled pentest — they exploit the gaps between them. Continuous penetration testing closes that window by embedding expert-led security validation directly into your development and release cycles.
2025 PENETRATION TESTING THREAT DATA
SOURCES: VERIZON DBIR 2025, IBM COST OF A DATA BREACH 2025
Why Annual Penetration Tests Aren’t Enough Anymore
What’s Included with Raxis Attack
Everything you need to shift from annual checkbox testing to continuous security validation — backed by real penetration testers, not just dashboards.
Continuous Testing vs. Point-in-Time Assessments
Raxis offers continuous penetration testing and point-in-time assessments — both powered by the same elite team and AI-augmented methodology.
Penetration Testing Services Available Through Raxis Attack
Expert-led assessments across every layer of your technology stack — available through both Raxis Strike and Raxis Attack.
How Raxis Attack Works
Guided by the MITRE ATT&CK framework and grounded in NIST 800-115, our methodology reflects how real adversaries operate — not how textbooks say they should.
Compliance
Continuous Penetration Testing for Regulatory Compliance
Raxis Attack satisfies ongoing testing requirements across every major compliance framework — with audit-ready reports generated directly from the Raxis One platform.
ISO/IEC 27001:2022
Comprehensive assessments aligned with Annex A.12.6.1 requirements.
CMMC 2.0
Supports DoD contractors with specialized CUI penetration testing (SI.3.218).
NIST SP 800-115
Testing methodology aligned with federal technical assessment guidelines.
NIST 800-171
Continuous testing aligned with CUI protection requirements for DoD contractors and subcontractors.