Raxis Blog Posts By Author
-
 Tips to Stay Secure at DefCon 2024The Raxis pentesting team is at DefCon in Vegas this weekend. It’s an awesome conference that has lessons and contests for everything from lock picking and car hacking to new network and application exploits that our team may try on your next penetration test. For those of you who may not have attended before (or […]
Tips to Stay Secure at DefCon 2024The Raxis pentesting team is at DefCon in Vegas this weekend. It’s an awesome conference that has lessons and contests for everything from lock picking and car hacking to new network and application exploits that our team may try on your next penetration test. For those of you who may not have attended before (or […] -
 Ongoing Cyber Attack Disrupts Car DealershipsWednesday thousands of car dealerships across North America experienced a cyberattack resulting in widespread outages and significant operational degradation.
Ongoing Cyber Attack Disrupts Car DealershipsWednesday thousands of car dealerships across North America experienced a cyberattack resulting in widespread outages and significant operational degradation. -
 Password Length: More than Just a Question of CompliancePassword length requirements are a key part of password security, but, with PCI, NIST, OWASP, and CIS offering different recommendations, what length is best?
Password Length: More than Just a Question of CompliancePassword length requirements are a key part of password security, but, with PCI, NIST, OWASP, and CIS offering different recommendations, what length is best? -
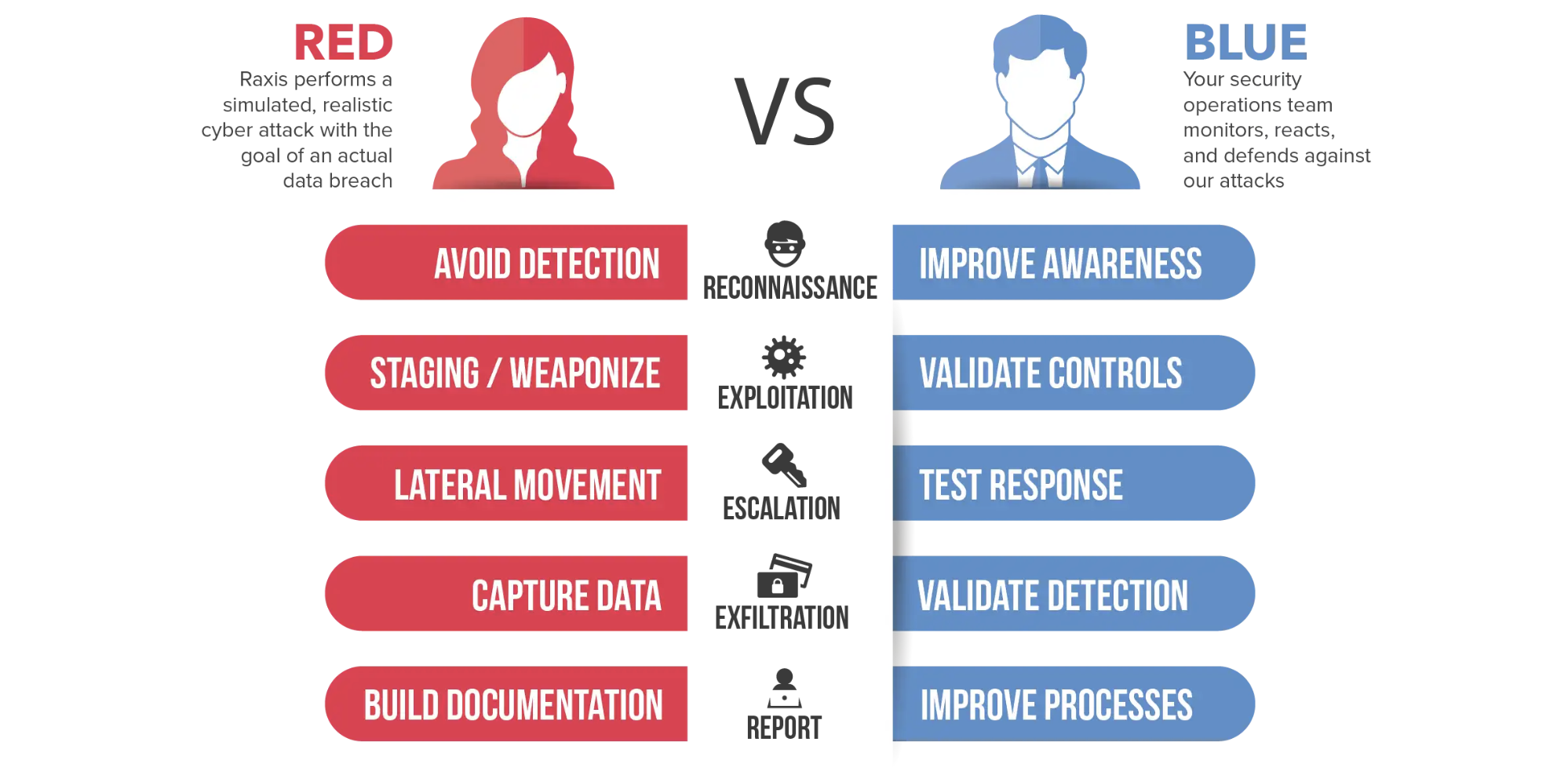 Red Teams, Blue Teams, and Purple Teams, Oh My!Red Teams, Blue Teams, and Purple Teams are cybersecurity terms describing different approaches to testing & improving security measures within an organization.
Red Teams, Blue Teams, and Purple Teams, Oh My!Red Teams, Blue Teams, and Purple Teams are cybersecurity terms describing different approaches to testing & improving security measures within an organization. -
 CIS vs. NIST: Understanding Cybersecurity Standards and FrameworksThe CIS 18 and NIST 800-53 are important gap analysis tools security professionals use to assess cyber defenses. Learn more about them from Raxis’ CTO Brian Tant.
CIS vs. NIST: Understanding Cybersecurity Standards and FrameworksThe CIS 18 and NIST 800-53 are important gap analysis tools security professionals use to assess cyber defenses. Learn more about them from Raxis’ CTO Brian Tant. -
 Meet the Team: Brian Tant, VP of EngineeringBrian Tant is Raxis’ Chief Technology Officer. Learn more about how he became a rock-star ethical hacker.
Meet the Team: Brian Tant, VP of EngineeringBrian Tant is Raxis’ Chief Technology Officer. Learn more about how he became a rock-star ethical hacker. -
 Why Our Team is Excited about the Purchase of BosclonerHere’s what the Raxis team members have to say about our recent purchase of the Boscloner electronic access badge-cloning technology.
Why Our Team is Excited about the Purchase of BosclonerHere’s what the Raxis team members have to say about our recent purchase of the Boscloner electronic access badge-cloning technology. -
 A High-Tech Take on an Old-Time ScamDon’t fall prey to scammers trying to convince you that your domain name is about to be stolen by an overseas company.
A High-Tech Take on an Old-Time ScamDon’t fall prey to scammers trying to convince you that your domain name is about to be stolen by an overseas company. -
 Why Companies Shouldn’t Overlook Mobile Application TestingPenetration tests are as important for mobile applications as they are for their web app counterparts. Here’s why.
Why Companies Shouldn’t Overlook Mobile Application TestingPenetration tests are as important for mobile applications as they are for their web app counterparts. Here’s why. -
 Understanding Vulnerability ManagementOne of our most common findings in Raxis penetration tests is the lack of an effective vulnerability management system. Here’s why that’s important.
Understanding Vulnerability ManagementOne of our most common findings in Raxis penetration tests is the lack of an effective vulnerability management system. Here’s why that’s important. -
 Imminent Threat for US Hospitals and Clinics, RYUK Ransomware Alert (AA20-302A) – Updated 11/2/2020A new nationwide cyberattack appears to be targeted at U.S. based hospitals, clinics, and other health care facilities. All health care operations should be on heightened alert for anomalous behavior or other Indications of Compromise (IOCs).
Imminent Threat for US Hospitals and Clinics, RYUK Ransomware Alert (AA20-302A) – Updated 11/2/2020A new nationwide cyberattack appears to be targeted at U.S. based hospitals, clinics, and other health care facilities. All health care operations should be on heightened alert for anomalous behavior or other Indications of Compromise (IOCs). -
 Why Network Segmentation is a Best Security PracticeNetwork segmentation can be an important line of defense against hackers. Raxis’ CTO Brian Tant explains why in this continuation of our Top 10 Vulnerabilities series.
Why Network Segmentation is a Best Security PracticeNetwork segmentation can be an important line of defense against hackers. Raxis’ CTO Brian Tant explains why in this continuation of our Top 10 Vulnerabilities series.
Raxis Attack
Continuous, expert-led PTaaS combined with advanced automation to uncover and address hidden vulnerabilities, ensuring your business stays ahead of evolving cyber threats while maintaining regulatory compliance.
Raxis Protect
Continuous vulnerability scanning, real-time asset management, and expert guidance to proactively identify and address security gaps across your entire digital ecosystem, ensuring 24/7 protection against evolving cyber threats.
Raxis Strike
Tailored, expert-led penetration testing that uncovers hidden vulnerabilities using real-world hacker techniques, providing actionable insights to strengthen your defenses and protect against sophisticated cyber threats.
Partner With Raxis
Partnering with Raxis empowers your business with elite penetration testing services, competitive reseller pricing, and recurring revenue opportunities, all backed by a proven track record of excellence and a commitment to staying ahead of evolving cybersecurity threats.
