New Metasploit Module: Microsoft Remote Desktop Web Access Authentication Timing Attack
Raxis team member Matt Dunn has uncovered a vulnerability in Microsoft’s Remote Desktop Web Access application (RD Web Access). Learn more in this blog article.
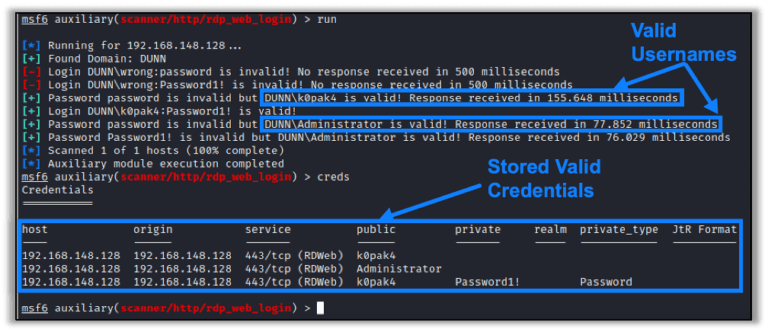
Raxis team member Matt Dunn has uncovered a vulnerability in Microsoft’s Remote Desktop Web Access application (RD Web Access). Learn more in this blog article.

Raxis’ penetration testing team demonstrates how to conduct a mousejacking attack to gain access as part of a penetration test.
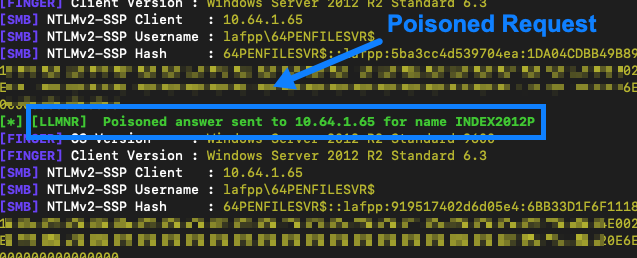
Learn an easy, effective way to test corporate networks with broadcast poisoning and SMB relay attacks used in tandem from the Raxis penetration testing team.

Does your penetration test always return a low-risk finding about TCP Timestamps? Why worry about it? Because it gives hackers info to use in other attacks.

In this post we’ll look at why IKE VPNs with Aggressive Mode enabled continue to be a vulnerability, how it can be exploited, and how to mitigate this risk.