Why Raxis Attack PTaaS is a Huge Win for Organizations
With the recent launch of Raxis Attack, a powerful PTaaS service, Caroline Kelly is excited to share how it can help organizations of all sizes stay secure.
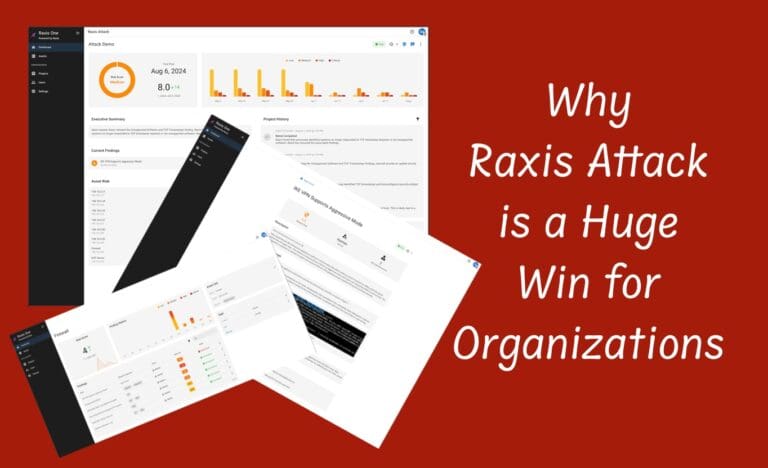
With the recent launch of Raxis Attack, a powerful PTaaS service, Caroline Kelly is excited to share how it can help organizations of all sizes stay secure.
Just a few days ago the world felt the rippling effects of a third-party push to networks across the globe. What would have normally been a routine undertaking instead caused mass disruption of information systems and brought businesses of all sizes to a standstill. Almost everyone was impacted by this incident in one way or…

Wednesday thousands of car dealerships across North America experienced a cyberattack resulting in widespread outages and significant operational degradation.

Password length requirements are a key part of password security, but, with PCI, NIST, OWASP, and CIS offering different recommendations, what length is best?

SOC 2 is a compliance and privacy standard that outlines how to manage customer data & related systems to ensure confidentiality, integrity, and availability.