How AI Makes Phishing Easy & What to Watch For
The use of AI has increased over the past couple years. So, as an exercise I decided to see how far it’s come. I decided a good test for AI would be creating a phishing campaign. The results show that it’s easier than ever for someone with little technical experience to create a believable phishing campaign.
Keep It Ethical
Before anyone is tempted to use these methods to trick someone without consent, I want to remind you that phishing and other such attacks are illegal and should only be performed by professionals who have a contract allowing them to perform the phish in order to test and provide training.
For those worried about how easy this is, stay for the end of the post where I offer tips you can use to help you catch a phish before you fall for it.
Creating the Phish Webpage
When running a phishing campaign, we need a landing page for our targets to end up on. I took a screenshot of Facebook’s login page, since it’s one many readers will recognize, and I uploaded it to an AI asking it to generate the HTML code for the screenshot. There are several AI tools to choose from, each has its strengths and weaknesses when it comes to coding. I suggest becoming familiar with as many as possible to experiment to find what works best for you.
Here’s the request and screenshot I passed along to the AI:
Generate HTML for the following screenshot
After submitting the screenshot to the AI, I got HTML code that resulted in the following.
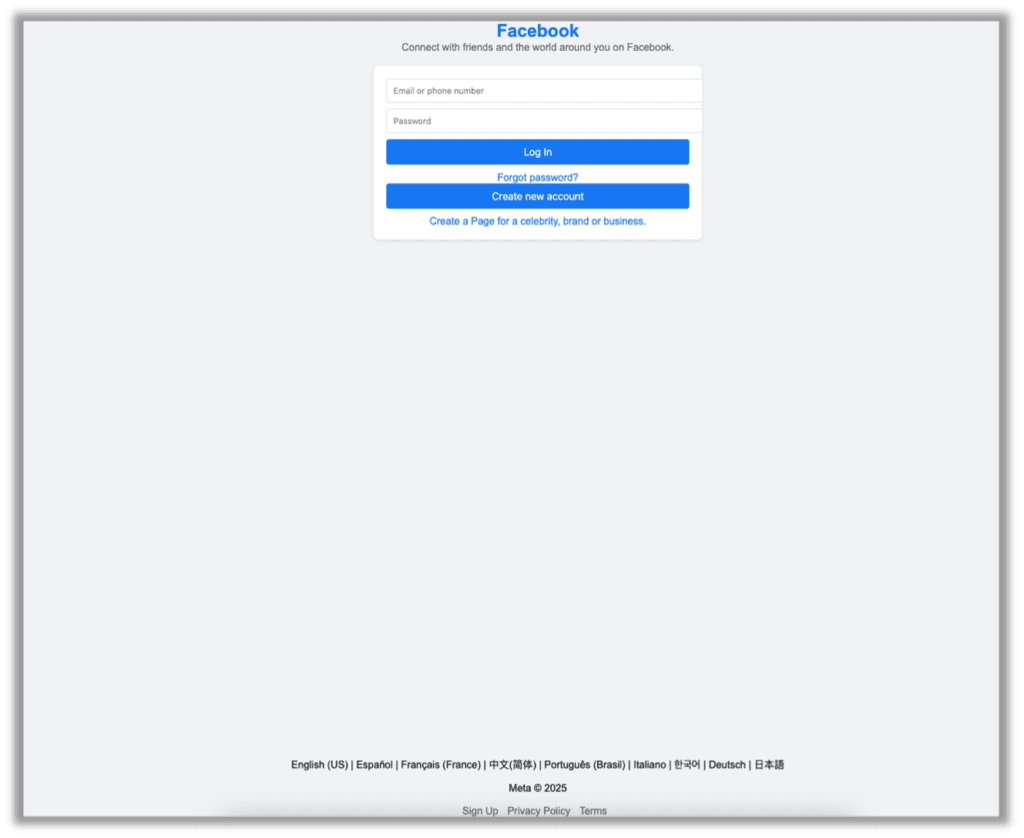
As you can see, the general structure is there, but it doesn’t match exactly.
So, I went back to the AI and prompted it with the changes below:
Make the text and login box side by sideHere’s what I got:
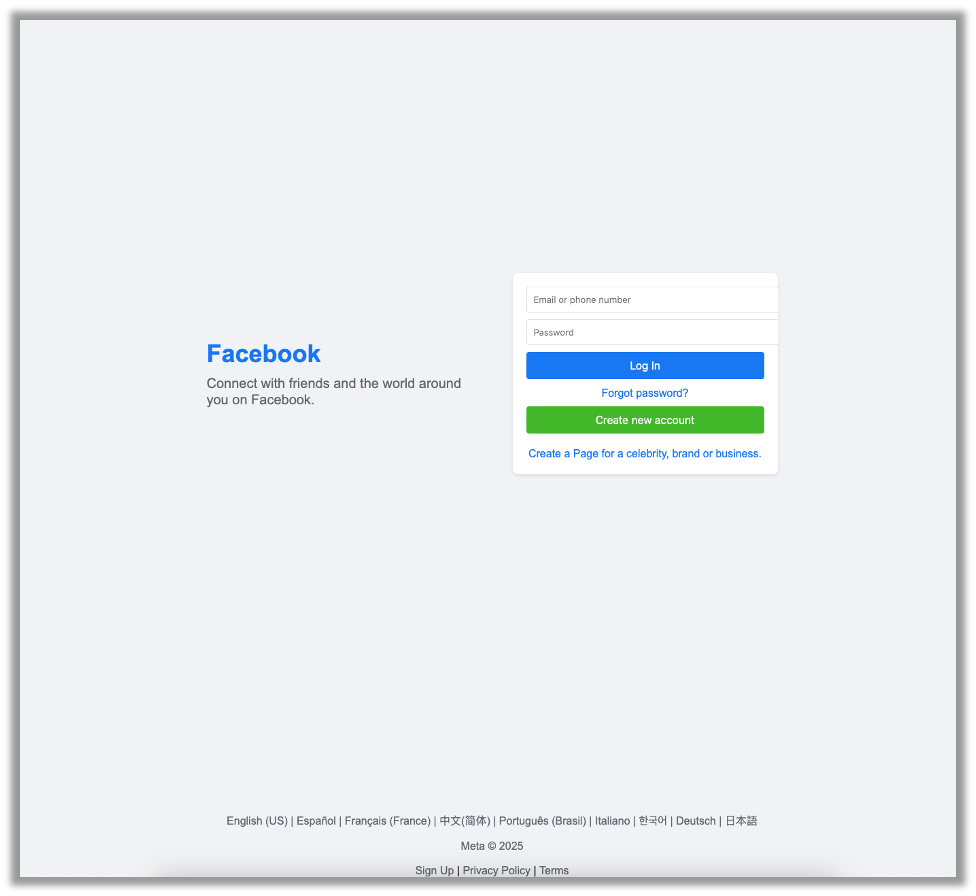
Now it’s definitely a lot closer, but it still can use some work.
I ended up fixing the footer to the bottom of the page and changing the background color to white myself. Now it’s not an exact match, but it looks pretty close for literally 5 minutes of work:
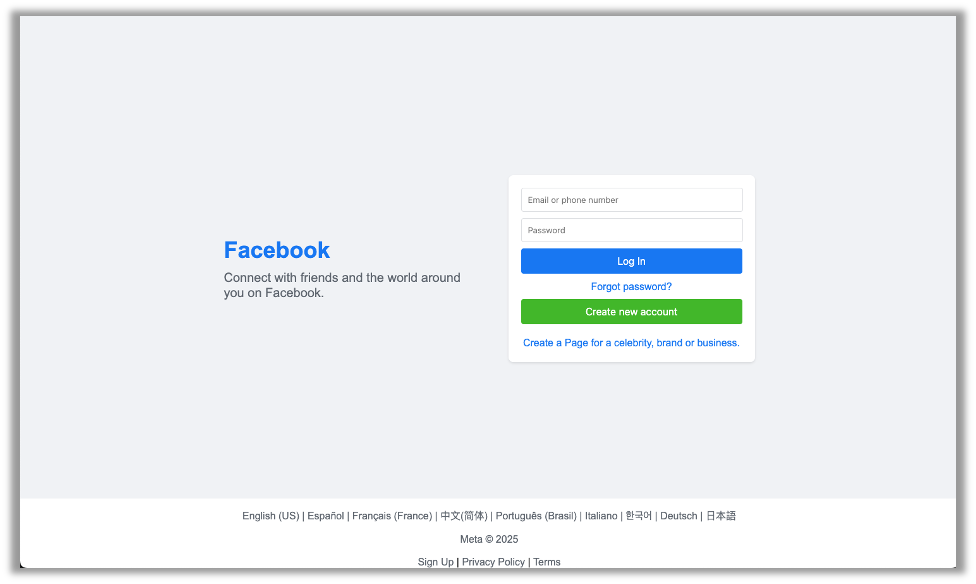
Creating the Phishing Email
I also wanted to see what kind of email the AI would generate for the phishing attack. I asked it to generate an HTML email asking users to login and review their account login activity.
Since it was in the same conversation as when I generated the login page, it automatically added Facebook to the email without me asking it to do so:
Generate an html email asking a user to login and check their account activityHere’s what it produced:
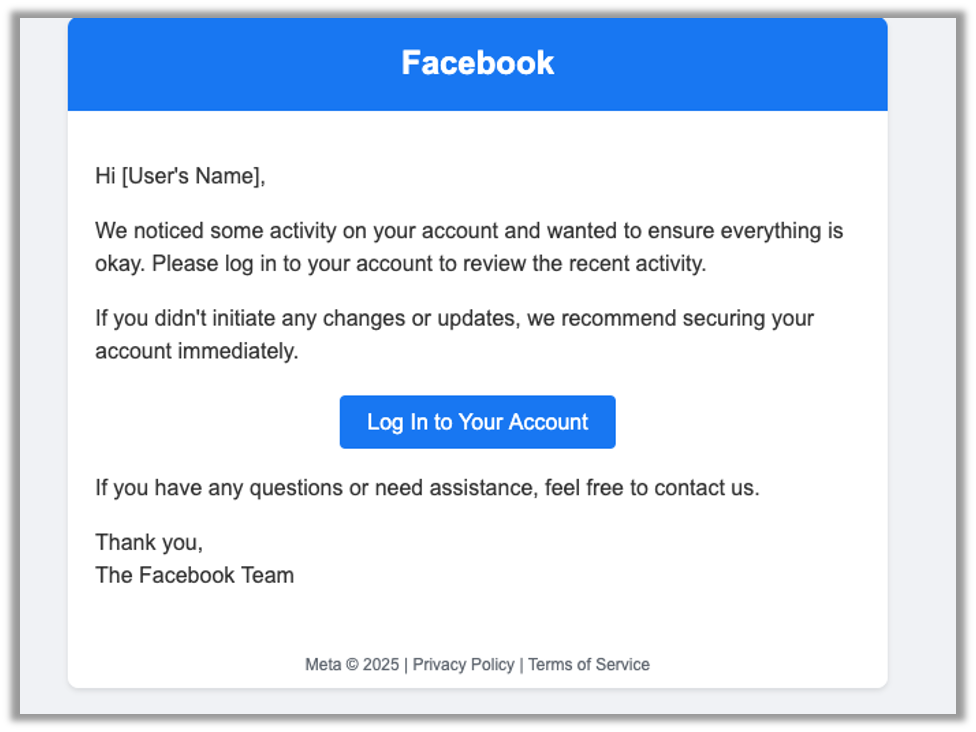
Now it’s a fairly well-made email. There are some changes I would make depending on the engagement and goals of the assessment, but, again, the majority of the busy work is done for me leaving me only the work for my specific task.
AI Made the Grade
Ultimately, AI can be a useful tool which can greatly speed up the development and deployment of phishing campaigns. And, while things still require some human touches, it makes it easier for attackers to create many campaigns quickly.
Most AI models have some safeguards in place. During my testing the models would sometimes refuse to give me the HTML code. Another time one added HTML code into the page saying it was for a test. But the same models would also sometimes just give the code without a second thought. So while providers try to add safeguards they don’t always work.
Also, it should be noted that state sponsored threats are using AI tools in their work. OpenAI has a page dedicated to their effort to disrupt that.
What You Can Do to Protect Yourself
For years, we’ve been warning our customers that phishing emails have become very sophisticated and often look legitimate. The AI game-changer is that it’s now easier than ever for anyone to create realistic a phish quickly.
My advice remains the same, but the nature of phishing threats will continue to evolve with greater sophistication as time goes on.
- Even if you have reason to believe that an email is legitimate, don’t use the links in the email. If it’s a service you use, you should know the website, so go to it yourself. If the email was legitimate, you should still be able to find what you need.
- Don’t reply to the email or use contact information in the email. If you know the person or the company, again you should have their info.
- If you do need to use the info in the email or reply to an unexpected email, you can always reach out to a known contact at a known number or email to verify that the email is legitimate. Especially don’t open attachments without checking first.
- If you received the email at work, your IT department may have a system where they verify that emails are legitimate for you. If not, put in a ticket or call them.
- If you use a password storage tool, and we highly recommend you do, it should not automatically fill in your ID and password on websites it doesn’t recognize. If you clicked a link in an email or SMS message and your password tool doesn’t fill in your credentials, that may be a sign that the page is fake.
Stay safe out there and take a look at our PSE & Red Team Series if you found this interesting!






