Log4j: How to Exploit and Test this Critical Vulnerability on Penetration Tests
Raxis demonstrates how to obtain a remote shell on a target system during penetration tests using a Log4j open-source exploit available to all. (CVE-2021-44228)

Raxis demonstrates how to obtain a remote shell on a target system during penetration tests using a Log4j open-source exploit available to all. (CVE-2021-44228)

In the cyberworld, news of a critical vulnerability affecting OpenSSL versions 3.0 – 3.0.6 will likely be the scariest part of Halloween ’22.
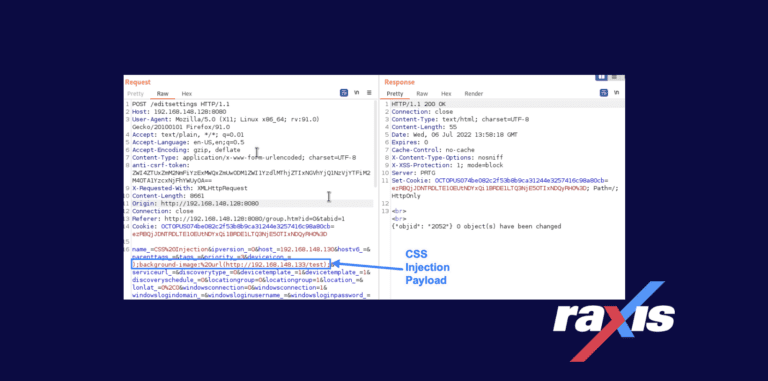
This CSS vulnerability, discovered by Raxis’ Matt Mathur, lies in a device’s properties and how they are verified and displayed within PRTG Network Monitor.

Wireless attacks are typically low-risk, high-reward opportunities that don’t often require direct interaction. See more about a wireless penetration test.

The hack of SpaceX’s Starlink shouldn’t distract security pros from the terrestrial threats that are much more likely and far more common.