PSE & Red Team Series: Physical Entry Bypass
In my last post in this series, we discussed the OSINT and reconnaissance to do before you are onsite and when you first arrive for a physical security assessment or red team test. This time we will move on to tools and techniques used to bypass common physical controls.
We’ll discuss badge cloning and social engineering attacks in later posts – in this post we’ll focus only on tools and methods used to bypass locked doors.
Getting Started
During your OSINT and reconnaissance phase, you will have discovered entry points to your client’s buildings and physical properties. The next step is to gain entry.
There are myriad of options to choose from, but I recommend starting with the attacks that present the least risk before moving on to more risky techniques. This allows us to err on the side of caution and reduce the chance of being discovered and potentially burned early in the engagement.

The methods we talk about here can usually be considered lower risk when performed off hours.
Bypassing an Unprotected Door Latch
An unprotected door latch is usually pretty easy to spot. If you have a single door that swings out towards you, there should be some kind of metal plate protecting the latch that holds the door next to the doorframe.
If you have a double door, it doesn’t really matter which way it swings. It should also have a protective metal plate covering the latch(s) between the two doors.

If the latch is unprotected, all that needs to be done is to insert a tool into the latch to disengage it allowing the door to swing open.
Canned Air Attacks
Performing a canned air attack can range in difficulty from “easy peasy” to “feels impossible, and why is it so hard to breathe in here”.
The first step is identifying an entryway that has a Passive Infrared (PIR) – based Request to Exit (REX) sensor. Next slide the nozzle of a can of compressed air into the crack around the edge of the door and the door frame. This can be on the sides of the door as well as the top or bottom of the door.
Turn the can upside down, and spray the contents into the path of the REX sensor. When you find the right spot, the sensor should trip and the door should open as if someone was on the other side attempting to exit.

There are common ways for organizations to defeat these attacks, including guarding the bottom of the door to prevent anything from sliding underneath it and adjusting REX sensor installations, to prevent unwanted entry. A combination of these defenses, will at the very least, make it hard for someone to bypass the sensor.
Under-Door Tool
The under-door tool can be tricky to get the hang of but also a lot of fun. It works for two types of doors.
First, when dealing with a door that has a lever instead of a knob, you can use the under-door tool to grab onto it, pull it down, and open the door. Slide the tool under the door and attempt to maneuver the tool to get the handle-shaped portion of the tool around the door handle. Then use the string to pull it down, opening the door.
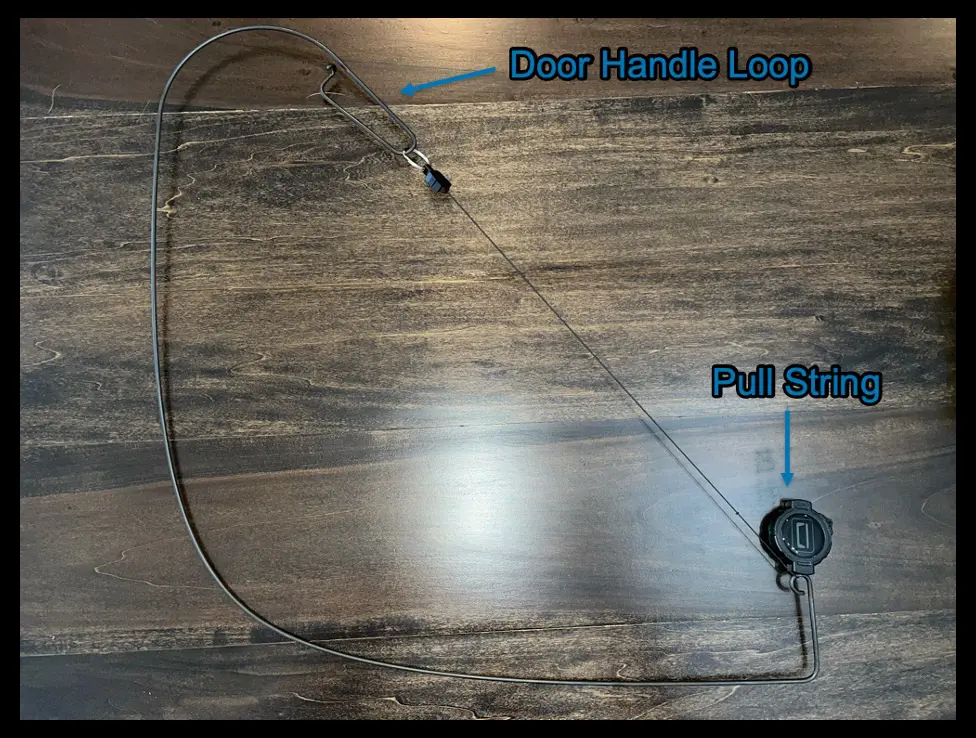
The second type of door this tool works for is a capacitive door release. These sensors work by triggering the door to open when a person touches something, usually the handle, causing its capacitance to change. Thankfully, they can often be triggered by touching the handle with a conductive object, such as the metal rod that you happen to be holding.
As with the door lever maneuver, slide the under-door tool under the door and hold the tool against the door handle as you pull the door open.
Take a look at Brad Herring’s post to learn a critical enhancement that makes an under-door tool easier to use.
Lock Picking
Most door locks can be picked in a lab environment. It gets a bit harder when you are squatting down, trying to pick a door lock and simultaneously worried security is going to round the corner and find you. This is more of a last-ditch effort and not necessarily a go-to.
But, when all those fails, this technique has a high success rate given that you have all the time in the world. We don’t have time here to explain how to perform lock-picking in detail, but a basic example uses a combination of a tensioner and a pick to manipulate the pins into proper position to allow the lock cylinder to turn, actuating the lock.

An On-the-Job Story
Once while performing a solo Physical Security Assessment (PSE), I reconnoitred the premises and found that the target was a suite inside a larger building. The building had no cameras, and the main door locked after 6pm. I found that there was a second unlocked and empty suite across the hallway that was under construction and unlikely to have much traffic. I entered the building around 4pm and waited in that suite until everyone left.
After checking numerous times to ensure that everyone was gone, I began to break into the suite. In this case, the door latch was unprotected, so I inserted my shrum tool into the latch and disengaged the lock. It took less time than using an actual key.

I hope you’ll check back for future posts in this series!