What do we know?
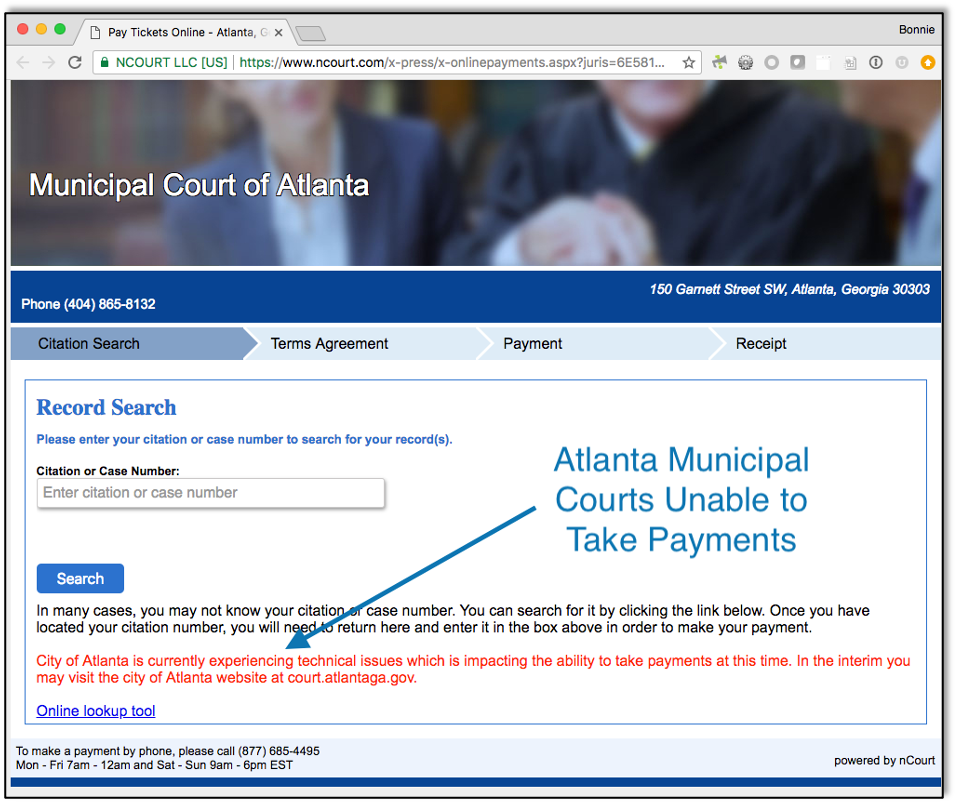
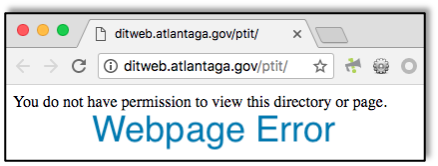
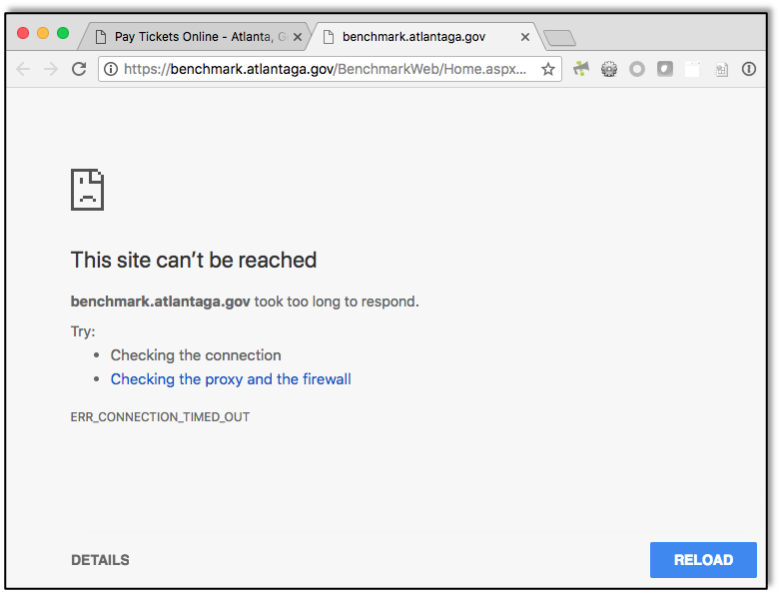
While events are still unfolding, we’re piecing together facts pertaining to the March 22nd ransomware attack on the City of Atlanta. As an Atlanta-based company, my colleagues at Raxis and I have been keeping a close eye on the happenings since the attack. The City of Atlanta has so far successfully kept people informed without revealing information that may be critical in responding to the attack.It appears that the epicenter of the attack was Atlanta’s municipal court (including tickets, citations, and other information) and bill-payment systems. I examined the Municipal Court of Atlanta website as I researched this post late Monday and found that the site displayed an error message explaining that payments could temporarily be made at a different site. When I clicked through to that site, I was given two options: a link back to the original site where I had started and a link to an error message, both seen here. Whether these sites were directly affected by the attack or are disrupted as part of the aftermath, people using these sites are affected just the same. The ‘Online lookup tool’ on the same page leads to a webpage that times out. It is possible that this service was not affected by the ransomware attack directly, but access to this page may have been removed as a precautionary measure to prevent further attacks. Based on these observations, we can infer that the attack has effectively diverted Atlanta’s resources to understanding, containing, and recovering from the attack. A trusted source tells Raxis that Atlanta is still working to fully confirm that critical infrastructure systems, such as fire, water and the airport, have not been impacted. All systems that may have been impacted have been taken offline until their state of compromise can be determined.Employees have been directed not to turn on or login to their workstations, which is another proactive security measure implemented in immediate response to the attack. A source has informed Raxis directly that vendors have physically been locked out of city buildings since the attack took place. A direct source has also confirmed to Raxis that construction companies have been unable to obtain permits that had already been submitted for approval due to the attack.Raxis also noted Atlanta’s Outlook Web App (OWA) and GIS server were displaying application errors after the attack. The City of Atlanta appears to be working around the clock to fix these services, nonetheless, these issues speak to the severity of the attack and the breadth of Atlanta’s response to an active threat.
What can we speculate about the attack itself?
The city has not released details about the attack yet, but we can speculate. A Raxis source stated that the attackers were demanding three bitcoin per decrypt key. Internet sources shows that the attackers are asking $6,800 per system or $51,000 to unlock the entire Atlanta system. While the math does not quite add up (currently Bitcoin rates are $8,056.44), we can see that the costs are high but also possible for Atlanta to pay.Raxis has spoken to a trusted source who confirmed that it is believed that the attackers gained access to Atlanta systems using MS-RDP (Microsoft Remote Desktop Protocol) and then installed SamSam ransomware which made the ransom demand. Our source stated that, as of close of business on Monday March 26th, Atlanta had not made a determination of whether to pay the ransom or to pursue other methods to recover business continuity.
RDP (Remote Desktop Protocol)
As noted above, a trusted Raxis source has informed us that the current belief is that attackers used MS-RDP as the entry point to Atlanta’s network. Raxis’ source, while not privy to the passwords that were harvested in the attack, believes that passwords likely were weak, which may have contributed to the success of the attack.While the focus currently is on the ransom demands, the full access that the attackers may have achieved in this type of attack likely may have allowed them to create back doors to Atlanta systems that they accessed, which would allow them to maintain a persistent presence for use in future attacks. Atlanta now finds itself in a position where it does not know whether a persistent threat is present on the internal network. It will need to maintain ongoing vigilance to determine the effectiveness of its response.Both the externally accessible MS-RDP service and the possible use of weak passwords are security issues that many companies deal with. This attack makes clear the importance of basic security housekeeping in protecting any network.
Patching & EternalBlue Rumors

While our sources do not point to patching issues such as EternalBlue being involved in this attack, there are multiple rumors circulating on the internet stating that EternalBlue was the entry point the attackers used. Even if EternalBlue was not a part of this attack, it has been used in other recent attacks, such as the RedisWannaMine cryptominer attacks.EternalBlue was one of several exploits released by ShadowBrokers in April 2017. Microsoft released a patch (MS17-010) the previous month on March 14th. EternalBlue was also used in the WannaCry and Petya/NonPetya attacks that made headlines in 2017. It exploits SMB 1.0 and affects several versions of Windows and Windows Server, including newer versions such as Windows 10 and Windows Server 2016. Using Shodan, a search engine that focuses on the configuration aspects of publicly exposed systems, Raxis confirmed that a system reported to be a part of Atlanta’s infrastructure still allowed SMB 1.0 as of Monday afternoon. As a career penetration tester, I know how easy this attack is to perform. In many cases, a successful exploit of EternalBlue leads to administrative rights on the system itself. An experienced hacker can often use other vulnerabilities, such as weak passwords and inappropriate delegation of administrative privileges, to gain further access on the network.
SamSam Ransomware
A trusted Raxis source has confirmed that SamSam (also known as Samas or SamsamCrypt) ransomware, first seen in late 2015, was used in the attack. Once the attackers infiltrated Atlanta’s systems using RDP, they appear to have deployed the SamSam ransomware that alerted Atlanta. Attacks of this type have been widespread, victimizing governments, the healthcare industry, and educational institutions, as well as businesses of all sizes. The attacks have been profitable because the ransoms have often been affordable, often making it more appealing to pay to decrypt the affected files, rather than take on the expense and administrative burden of adjusting operations to compensate for lost data. Even with backups in place, it can take days or even weeks to restore systems fully. It seems best not to pay an attacker who is holding your information at ransom, but, in many cases, restoring business operations in a timely manner takes precedence.
What now?
While our source tells us that the initial internal response efforts were disorganized, Atlanta now appears to be engaged with the Microsoft and Cisco experts that they’ve brought in. The current lack of details is a positive; like any active investigation, managing communications is paramount until as many facts as possible have been discovered.A trusted source tells Raxis that Atlanta has made it clear that brand management is a priority as its bid to become the second Amazon headquarters and the 2019 Super Bowl loom large.That said, Atlanta has demonstrated effective triage measures in response to the attack. As mentioned above, employees were told not to login to their workstations, decreasing the surface area for the attack. An airport spokesman told the Associated Press that the airport Wi-Fi network (as well as part of the webpage) had been taken down as a precaution.Atlanta has also been updating the public actively with news that is considered appropriate to release. Atlanta has leveraged their Twitter account, @cityofatlanta, to great effect, using it to post videos of press conferences with Atlanta Mayor Keisha Lance Bottoms as well as alerting constituents as city information services are restored to service.
Finally, what can your company do to not end up in this position?
Test, test, test. Working at Raxis I’ve seen penetration tests open customer’s eyes to issues they may not have known about or did not understand. While a penetration test may feel scary (you’re asking a hacker to enter your systems; the fear is understandable!), if you choose a good company, you should find that a penetration test is an indispensable tool to discover and prioritize your security tasks. The report you receive at the end of each test should do just that. To learn more about Raxis’ penetration testing services or just to find out more about the types of tests we recommend, see our site at https://raxis.com/penetration-test/. At Raxis, we’ve also worked with smaller companies that don’t need or can’t afford a full penetration test. We’ve recently launched a new service, the Baseline Security Assessment, that is meant to provide the benefit of security awareness for these companies that may not require the full depth of engagement that comes with our penetration testing services. Mature organizations that have mastered the art of managing a strategic security program that includes regular testing, vulnerability and patch management, as well as identity and access control, will benefit from the next step in security readiness. Investing in our Rapid Response Incident Response retainer is a strong measure of preparedness for when a security incident does occur. See Specialized Services to learn more about how Raxis can help you with this as well.If you have questions about where to start and what services could be right for you, fill out the contact form at https://raxis.com/contact/, and we’ll be happy to discuss how we can help fortify your defenses to keep you open for business and out of the headlines.