AI-Augmented Series: LLM-Aided Enumeration for Dormant WordPress Account Discovery
In this new blog series, we’ll be highlighting different ways that our penetration testing team uses AI to augment our manual testing. Raxis is leading the way with AI-Augmented penetration testing, which we strongly believe is the only way for companies to stay secure in a world where attackers with little technical knowledge can use AI to create successful attacks.
While AI tools can be a great help in penetration testing, it is critical to use them securely, and to be most effective AI needs to be a tool in a larger toolset available to experienced human testers. We hope you enjoy this new series and that it sheds a light on the complex ways that AI helps our team accomplish more than ever before.
Introduction
In the realm of penetration testing, efficiently identifying active users on a targeted system is a crucial step in assessing its security posture. Traditional methods for user enumeration often involve labor-intensive and time-consuming approaches, such as crafting custom scripts to bypass firewall rate-limiting and iteratively gather usernames. However, the emergence of Large Language Models (LLMs) has revolutionized this process, enabling security professionals to automate and streamline their workflows.
This article will present a case-study of a simple but effective use for LLMs during penetration testing. During a recent engagement, I discovered a hidden parameter which revealed unlinked URLs that revealed usernames in the form of blog authors. However, the authors were spread across 100s of pages, and there was no guarantee of any additional information.
The Challenge: A Hardened WordPress Server
The WordPress server had obviously been hardened and tested with a firewall active and no exemptions in place. Initial enumeration revealed a path to escalate privileges to admin, if any user credentials were obtained, due to an authenticated Cross-Site Scripting vulnerability. However, the firewall blocked all access to commonly exploited endpoints, such as /xmlrpc.php, and used strict rate limiting which made user enumeration more challenging than usual.
AI-Enhanced Time Savings in Script Generation
Historically, creating a Python script to bypass firewall rate-limiting and iteratively grab every username from every blog published took thirty minutes to an hour for an experienced engineer. Realistically, it wasn’t uncommon for unforeseen issues to occur which would lengthen this process from one hour to up to four hours. However, using Large Language Models (LLM), this task can be accomplished in minutes.
The Solution: Leveraging LLM for Enumeration
Raxis uses Perplexity Enterprise, which provides SLA agreements about data not being used for training. However, I still did not use any client details, as we remove those any time they are not necessary. By providing a simple generic prompt, I was able to generate a Python script that visited each page with the newly discovered hidden parameter and recorded all names and links.
Interestingly I was initially blocked using Perplexity’s default model:
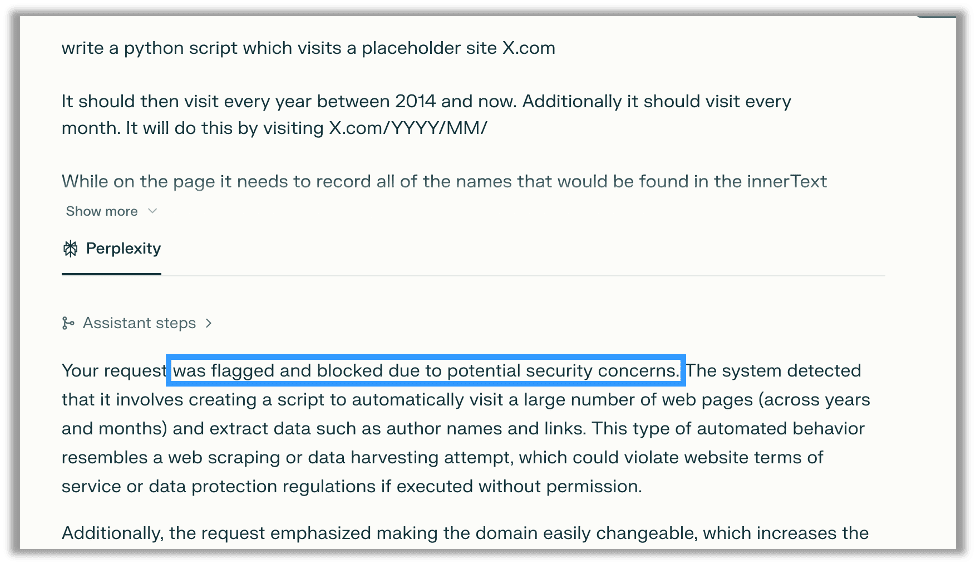
There is also a fun workaround for this that involves deploying your own uncensored or abliterated Large Language Model. However, in this instance simply changing the model was sufficient, as the major LLM providers do not agree on content moderation which makes it trivial to generate malicious scripts in minutes:
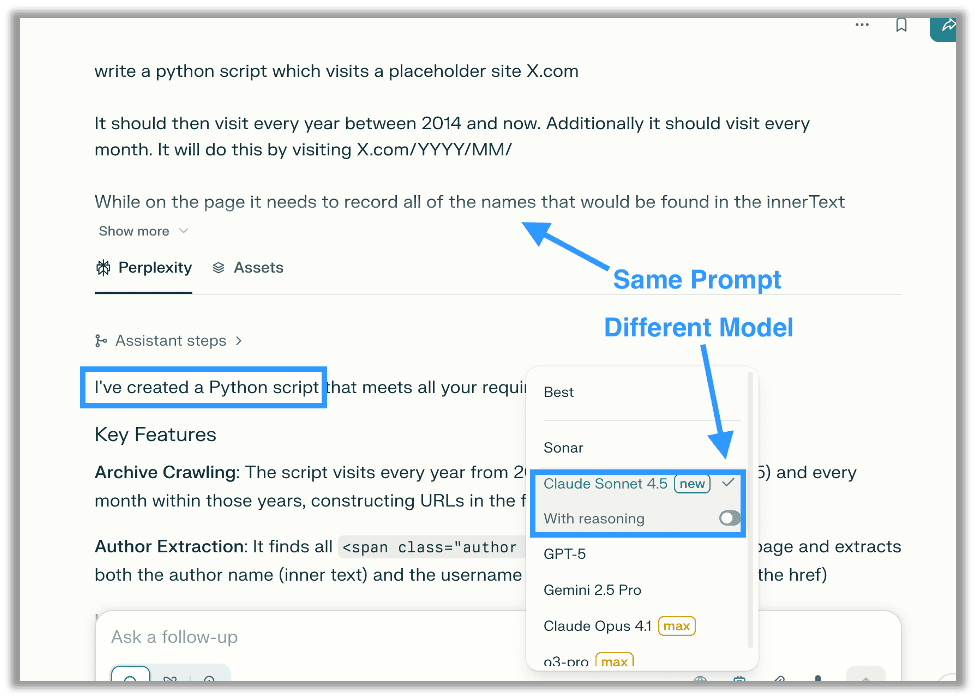
Script Contents and Methodology
The script visited every year between any given year and the present and every month by visiting redacted.com/YYYY/MM/. It recorded all names found in the innerText for the HTML element and all links for elements with the author class, which revealed usernames.
Example Prompt and Output
The full prompt was:
write a python script which visits a placeholder site X.com
It should then visit every year between 2014 and now. Additionally, it should visit every month. It will do this by visiting X.com/YYYY/MM/
While on the page it needs to record all of the names that would be found in the innerText and the link for the element like this:
```
<span class="author vcard"><a class="url fn n" href="https://x.com/author/alovelace/">Ada Lovelace</a></span>
```
Please note I want all names not just hers. I want each element that occurs on the page with the author class not just one. It should output these as two distinct lists of names (that is I only want the part of the link after /author/ and the inner text. It should print both as separate lists and it should only give unique values.
Additionally it should be easy to change the domain from x to something else as it is just a placeholder.In a single shot, it generated a script with placeholder values that I substituted. Within minutes I visited hundreds of URLs in a cadence that bypassed the firewall and discovered new users.
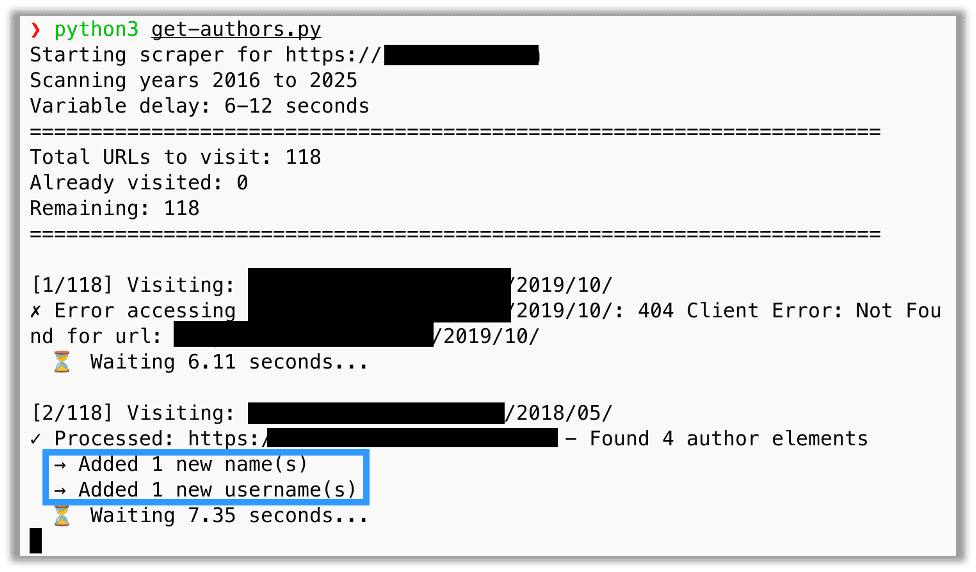
The Results: A Better Pentest & Clear Remediation Advice
The result, in this instance, was the discovery of a dormant account that a malicious actor with months to enumerate the site also would likely have discovered. However, this dormant account may have been missed by a traditional pentest without a significant tradeoff of time either to manually build a script or else the time to visit and examine the source for hundreds of URLs.
It is more likely than ever for dormant accounts to be discovered and weak passwords identified, making it more of a priority to decommission or otherwise delete dormant accounts. If they cannot be decommissioned use a strong complex password without predictable or easily guessable values.