Exploiting GraphQL for Penetration Testing
Exploiting GraphQL, a query language inspired by the structure & functionality of online data storage & collaboration platforms Meta, Instagram & Google Sheets.
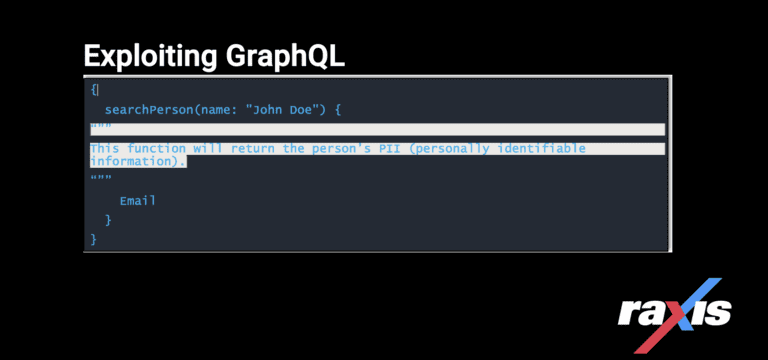
Exploiting GraphQL, a query language inspired by the structure & functionality of online data storage & collaboration platforms Meta, Instagram & Google Sheets.

Raxis demonstrates how to obtain a remote shell on a target system during penetration tests using a Log4j open-source exploit available to all. (CVE-2021-44228)
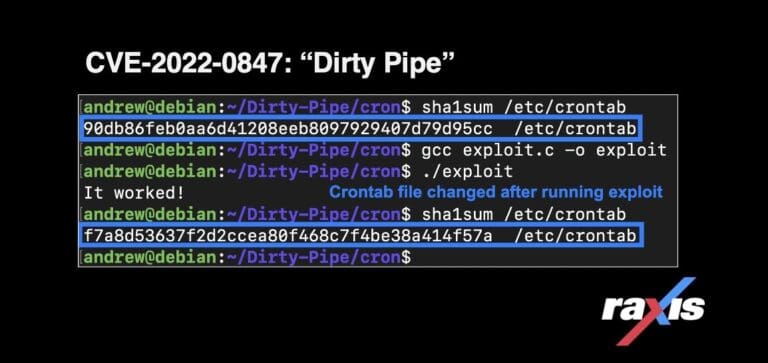
The Dirty Pipe vulnerability (CVE-2022-0847) allows any user to write to read-only files, including files that are owned by root, allowing privilege escalation.

In this post, Raxis VP Brad Herring explains how web proxy tools can turn even simple buttons and check-boxes into avenues for an attack.

Is your organization is in the market for a penetration test? Raxis’ COO Bonnie Smyre continues her two-part series on how to hire a penetration testing firm.