AI-Augmented Series: AI Scripting for Brute-Forcing on a Web App Pentest
On a recent web app pentest, Andrew Trexler used AI to find client-side code that stopped his brute-force attack then used AI again to thwart that code.
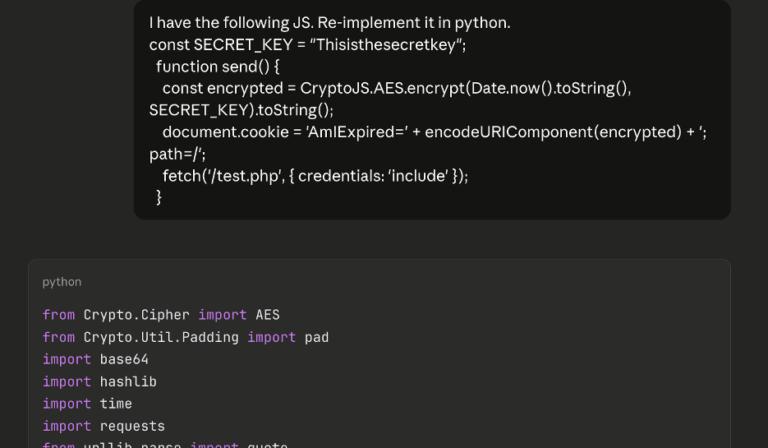
On a recent web app pentest, Andrew Trexler used AI to find client-side code that stopped his brute-force attack then used AI again to thwart that code.
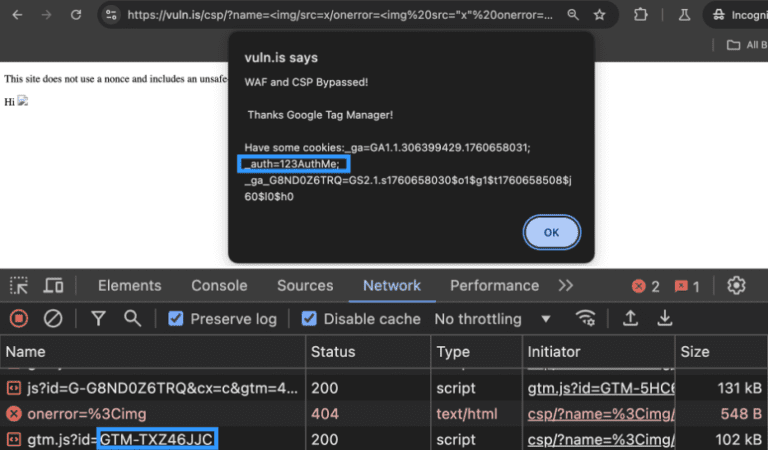
Ryan Chaplin takes an in-depth look at how attackers can use unsafe directives to bypass CSP, notably in Google Tag Manager, and how to remediate the issue.

Recent attacks, including GitVenom and Lumma Stealer, underscore the threat of Attackers using GitHub repositories as malware staging mechanisms.

We reached into our vaults to bring you the final video in our cross-site scripting (XSS) series. Learn about cookie theft, website defacement, and CSRF attacks.

The OWASP Top 10 2025 for web applications release candidate was released last week. Take a look at which categories have moved as well as one new category.