CIS vs. NIST: Understanding Cybersecurity Standards and Frameworks
The nature of cybersecurity is that threats evolve rapidly, and hackers often strike unpredictably. Despite the dynamic nature of the field, however, there are security frameworks in place to guide the development of effective cyber defenses. The ones used most frequently by security professionals are the National Institute of Standards and Technology (NIST) Framework for Improving Critical Infrastructure, also known as the NIST Cybersecurity Framework (NIST CSF), and the Center for Internet Security’s 18 CIS Critical Security Controls (CIS 18).
Depending on their industry and/or company size, Raxis customers are sometimes required to assess the maturity of their cybersecurity using these tools. Other times, they simply want to have a better internal understanding of their overall security posture and gaps. Regardless of the reason, the question we get most often is which standard is best for the company. Our team has vast experience with both CIS 18 (formerly SANS Top 20 or CIS 20) and NIST CSF v1.1 requirements, and we can develop a scope of work based on either.
That said, it’s important to understand exactly what these frameworks are and how they help improve your cybersecurity posture. Let’s start with CIS 18 as we’re asked about that one most often.
CIS 18
As the name suggests, the CIS 18 is a list of 18 primary security controls organized by activity. It is designed to measure an organization’s level of maturity as compared to a set of recommended standards.
The 18 CIS controls each include three categories of sub-controls, called implementation groups, that increase in complexity based on the maturity of the organization’s cyber defenses.
- IG1 includes the base-level security controls every enterprise-level organization should have in place. Think of this as the minimum standard, designed to help companies with limited cybersecurity expertise thwart general, non-targeted attacks. There are 56 additional safeguards in this group.
- IG2 is designed to help organizations that manage multiple IT departments, with varying degrees of risk, cope with increased operational complexity. It includes 74 additional safeguards.
- IG3 is aimed at organizations that employ IT security experts and is designed to help them secure sensitive data and lessen the impact of cyberattacks. There are 23 additional safeguards included in IG3.
For customers who need a detailed analysis of each control, Raxis recommends our Enterprise CIS 18 Analysis. This includes an extensive interview and documentation process that will yield a detailed gap analysis and roadmap for hardening your defenses in accordance with the CIS controls.
NIST
The NIST CSF Version 1.0 was created in 2014 in response to the US government’s call for a voluntary framework to establish a “prioritized, flexible, repeatable, performance-based and cost-effective approach to managing cyberthreats.” Version 1.1 was released in 2018 and includes additional guidance and clarification.
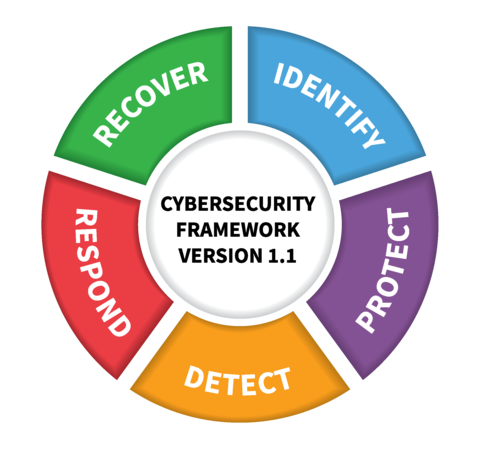
Unlike CIS, the NIST framework is intended as a gap-analysis tool based on the organization’s target operational state. It includes a core set of five cybersecurity functions that present industry standards and guidelines for all levels of an organization. These are broken out as follows:
- Identify: Develop an organizational understanding to manage cybersecurity risk to
systems, people, assets, data, and capabilities.
Protect: Develop and implement appropriate safeguards to ensure delivery of criticalservices.
- Detect: Develop and implement appropriate activities to identify the occurrence of a
cybersecurity event.
Respond: Develop and implement appropriate activities to act regarding adetected cybersecurity incident.
Recover: Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
Within each function are categories which are groups of cybersecurity outcomes closely tied to needs and activities. An example would be “Data Protection.” Within each category are sub-categories which identify specific outcomes or operational states. For the preceding example, sub-categories include: “data is protected at rest” and “data is protected in transit.”
Another difference between CIS 18 and NIST CSF is that the latter also includes informative references, which map the CSF’s applicability to other frameworks, such as COBIT, ISO, ISA, CIS, and others.
For customers needing detailed reviews of each of the 108 NIST CSF sub-categories, Raxis recommends our Enterprise NIST Analysis. Like the Enterprise CIS 18 Analysis, this includes an extensive interview and documentation process that will yield a detailed gap analysis and roadmap for hardening your defenses, but this time in accordance with the NIST controls.
Security Framework Analysis (SFA)
For organizations that don’t have to meet regulatory compliance standards, it may still make sense to evaluate your security against a meaningful framework. This approach will look at groupings of controls versus individual controls and provide a gap analysis with road mapping based on your organization’s needs. Toward that end, Raxis offers security framework analysis (SFA) engagements that are based on the CIS 18 or the NIST CSF (as well as customized engagements for other frameworks that may fit your industry best).
Similar in purpose to our enterprise analyses, but reduced in scale, the Raxis SFA is designed for small and midsized businesses that want peace of mind knowing that they are addressing the broader security standards, but that don’t need the intensive, granular focus of the enterprise analyses.
Conclusion
Whether your goal is to satisfy a legal or industry requirement, to gain a better understanding of your security posture, or both, Raxis has the experience and expertise to guide you to the service that matches your needs. Our goal is to help you reach the highest level of security possible to protect your data, your customers, and your reputation.
The best place to start is a conversation with our experts. Just give us your contact information and we’ll be in touch.