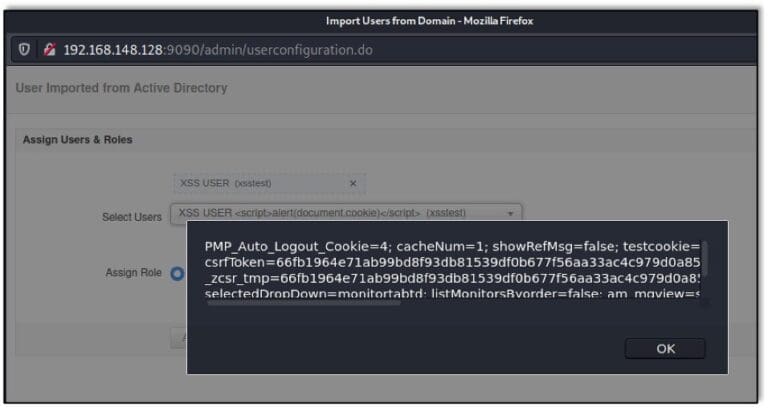
Cisco Patches Critical Security Vulnerabilities
Affected Products
The critical and high-severity vulnerabilities that were patched affect many products across Cisco’s product line including:
- Cisco SD-WAN
- Cisco DNA Center Command Runner
- Cisco DNA Center
- Cisco Smart Software Manager Satellite Web UI
- Cisco Data Center Network Manager
- Cisco Finesse OpenSocial Gadget Editor
- Cisco Secure Web Appliance
- Cisco Advanced Malware Protection for Endpoints and Immunet for Windows
- Cisco Umbrella Dashboard
For a complete list of affected products, check Cisco’s Security Center.
The Vulnerabilities Addressed
The patches addressed numerous critical vulnerabilities and exposures (CVEs), including serious threats such as command injections, SQL injections, DLL hijacking, cross-site request forgery attacks, directory traversals, and more. Some of the most critical, such as a buffer overflow in SD-Wan, allow for unauthenticated, remote code execution as the root user and should be patched immediately. Cisco does not believe these were actively being used in the wild, but they should nonetheless be treated seriously and patched immediately.
Remediation
Cisco recommends patching all affected products as soon as possible as there are no current workarounds to the newly released critical vulnerabilities. A full list of Cisco’s recent security advisories is also available from the company’s security center.
Does your company have a vulnerability management plan in place? Take a look at this video as Raxis’ CTO Brian Tant explains why you should.