PSE & Red Team Series: OSINT & Reconnaissance
As a penetration tester at Raxis, I enjoy (legally) hacking into customer systems and providing them with the knowledge to correct the issues I discover so that they can fix them before the bad guys find them. In the real world, though, the bad guys often put a lot of pieces together to get that network access.
Physical Social Engineering (PSE) engagements allow organizations to see the weaknesses in their buildings, offices, and other facilities. Red team engagements combine our PSE tests with phishing, network, and application tests to show our customers what a malicious hacker might accomplish using every point of access from every angle.
In this new series, I’ll focus on the steps and tools we use for PSE and Red Team engagements.
Let’s Be Ethical
First and foremost, Raxis does not condone the use of these tactics in an illegal manner, and I want to stress that doing so is likely against the law. The information we provide here is for use only by security professionals with legal contracts providing the appropriate permissions. Do not try this at home. Okay, maybe I’ve always wanted to say that!
Always have written permission from your clients with you at all times when performing PSE activities. Colloquially known as a “Get out of Jail Card,” this should be a document, providing your information and a valid date range for your testing, as well as the names, contact information, and signatures of at least two people from your customer who have the authority to explain to employees, or even the police, that you are legally allowed to be doing what you are doing. I carry one copy in my backpack, one in my wallet, and one in my pocket. In this case, overkill doesn’t really exist.
Beyond that, your company and your customer should both have access to the legal contract for your engagement, including the scope of your testing. I cannot stress enough how critical it is to follow the scope of that contract precisely.
Getting Started on your Physical Social Engineering Assessment
With that out of the way, the work for PSE assessments starts before you even leave home. Your first step should always be doing reconnaissance on the in-scope facilities. This includes performing OSINT (Open-Source Intelligence) on the locations and employees.
Offsite OSINT
I generally begin by reviewing satellite imagery of the locations and any photos I can get of the entrances and exits. This includes looking at Google Maps, looking at Google Street View, reviewing the organization’s social media (don’t forget job-related sites like Glassdoor and LinkedIn). It can also include reaching out to different building services to find out what onsite security is like.
Using all the data you get from this, you should begin to put together a list of possible entry points.
- Does the main entrance look like can be bypassed with canned air?
- Does the back entrance look like the latch is unprotected?
- Is there a designated smoking area?
- Is there a recreational area?
- Where is employee parking?
These are all questions that you want to catalog and find the answers to.
OSINT Tools
There are several tools that allow one to enumerate an organization’s digital footprint, including but not limited to, TheHarvester, ReconNG, and Amass shown below.
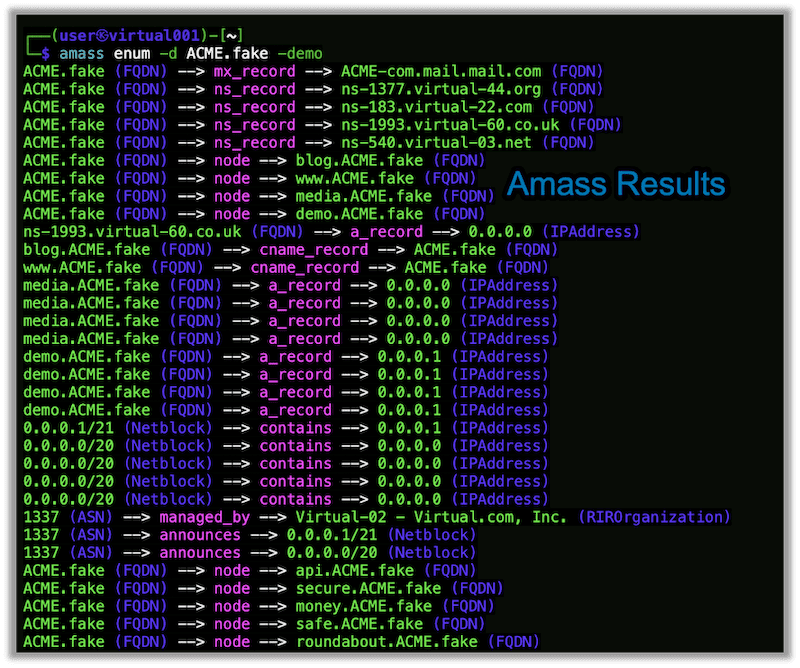
Maybe I’ll go into some of these tools more in a later post in our Cool Tools series.
Onsite Recon
Once onsite, we can perform additional reconnaissance to establish the attack surface of the facility:
- Is there building security?
- Can you enter the target area at night?
- Where can you hide until closing?
This is the time to get those answers.
While performing initial onsite recon, I usually dress differently than I plan to dress when I come back later try to gain entry. You have to expect to be seen by cameras, security guards, and employees, and, before you understand the layout and gather more info, you may look suspicious. It’s better not to have anyone associate entry-bypass you with recon-you.
Speaking of entry-bypass, I hope you’ll take a look at my next post in this series on Physical Entry Bypass Techniques.