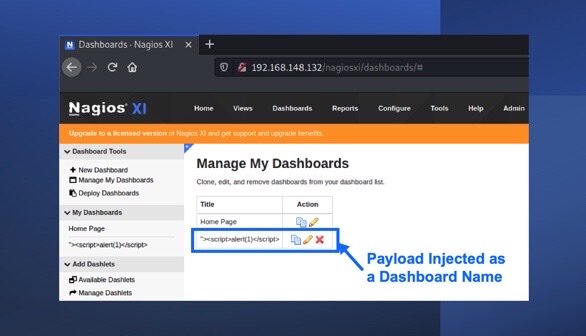
Vulnerability Summary
Recently, I discovered a stored cross-site scripting (XSS) vulnerability in Nagios XI v5.8.5. The vulnerability exists in the dashboard page of Nagios XI (/dashboards/#) when administrative users attempt to edit a dashboard. The dashboard name is presented back to the user unencoded when the edit button is clicked, which can allow dashboard names with malicious JavaScript to be executed in the browser.
Proof of Concept and Exploitation Details
The vulnerability can be triggered by inserting html content that contains JavaScript into the name field of dashboards. The following payload was used to launch an alert box with the number 1 in it as a proof of concept:
“><script>alert(1)</script>An example of this in the dashboard’s name field can be seen in the image below:
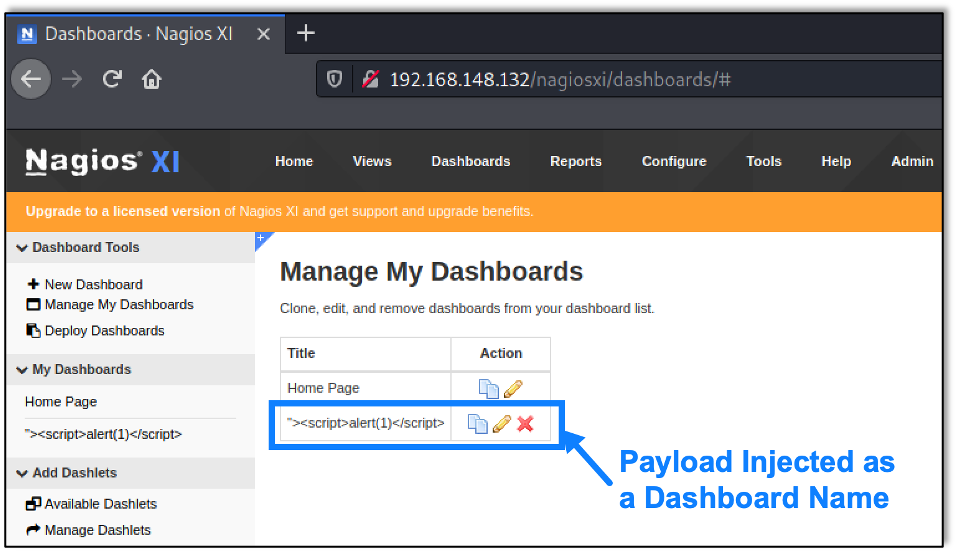
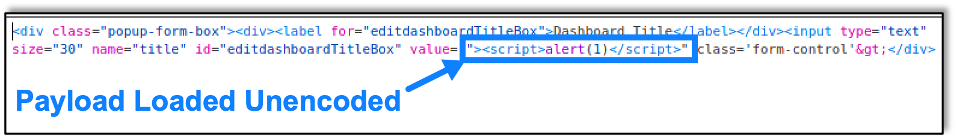
After clicking the edit button for the dashboard name, the dashboard’s name is loaded as unencoded HTML, as shown below:
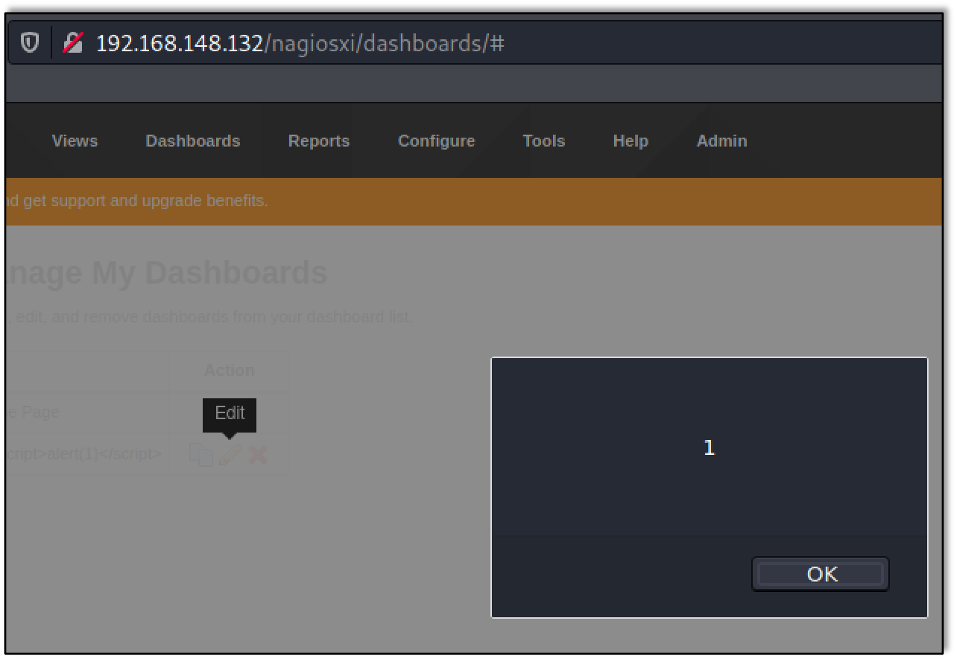
After clicking the edit button for the dashboard name, the JavaScript from the script tag is executed as shown in the following image:
Vulnerable Software Version
Raxis discovered this vulnerability on Nagios XI v5.8.5.
Remediating the Vulnerability
Upgrade Nagios XI to version 5.8.6 or later immediately.
Disclosure Timeline
- August 5, 2021 – Vulnerability reported to Nagios
- August 6, 2021 – CVE-2021-38156 is assigned to this vulnerability
- September 2, 2021 – Nagios releases version 5.8.6 addressing this vulnerability
CVE Links and More
- Mitre CVE – https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-38156
- NVD – https://nvd.nist.gov/vuln/detail/CVE-2021-38156