Chained Attacks and How a Scan Can Leave You Vulnerable
The results from your vulnerability scan showed only a couple of low or moderate level findings, but there is no denying that two experienced hackers now have domain admin rights; the freshly printed summary document on your desk spells out in excruciating detail how they traversed the darkest corners of your network and gained access to critical data.
Fortunately for you, they’re Raxis team members, and you’ve paid them to do just that.
The Chained Attack
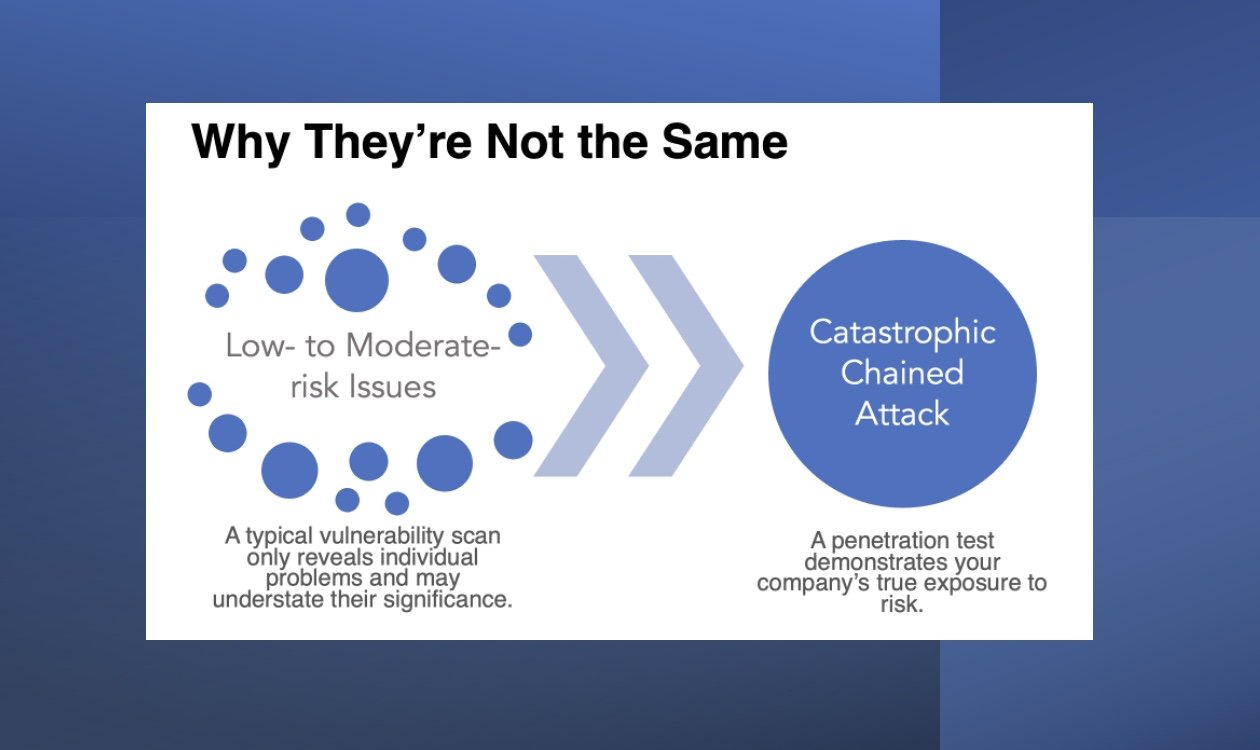
This scenario plays out frequently for Raxis customers who previously relied on companies that pass off vulnerability scans as faux penetration tests. It highlights why a scan, by itself, can give businesses a false sense of security about their cyber defenses. At their best, scans only point out individual links in what skilled and experienced hackers can turn into a chained attack – using one vulnerability to discover others, increasing or escalating network access with each move. In the case of parameter or business logic exposures, scans often remain blissfully unaware, failing to identify the exposures at all.
UNFAMILIAR WORD OR TERM? VISIT OUR GLOSSARY.
We’ll use a real-life example from a recent Red Team engagement to illustrate just how this works. Keep in mind that the following recap is just one way to employ a chained attack. There are many others. In fact, it’s such a common technique that it’s part of the test ethical hackers take to earn the Offensive Security Certified Professional (OSCP) certification. (Read about Senior Penetration Tester Andrew Trexler’s experience with the OSCP exam.)
The First Link
Using a response poisoning attack, our testers achieved Man in the Middle (MitM) and relayed Server Message Block (SMB) handshakes to hosts with SMB signing disabled, which allowed them to execute local commands and extract local password hashes stored by the security account manager (SAM). One of those hashes was associated with a local administrator account, and they used it to connect to a system on the internal network.
Once inside, they exploited a known design flaw in Windows authentication and used this local administrator hash in a Pass-the-Hash (PtH) attack using CrackMapExec (CME). They didn’t even have to crack the hash and get a cleartext password. Just sending the hash was sufficient to allow access.
Creating the Chain
Using PtH, our ethical hackers enumerated users logged on to a system, determined valid usernames, and extracted their Kerberos ticket hashes. This time, they did have to crack the hashed ticket for an administrative service account they found. A weak password and robust cracking hardware made this possible within seconds.
Having identified the cleartext password for that administrator account, they found that it was shared amongst numerous systems. They connected to other systems across the network and found a domain administrator logged into one of them. An attempt to access the Local Security Authority Subsystem Service (lsass.exe) file failed at first because the company’s security blocked “procdump.exe,” the tool we were using to gather a memory dump of the process. However, a second attempt with Process Explorer was successful and allowed our team to download a memory dump of the “lsass.exe” process, giving us access to the runtime state of the service that performs Active Directory database lookups, authentication, and replication.
Another tool, Mimikatz, enabled our testers to extract the contents of that file, including the reusable NTLM password hash of a Domain Administrator (DA). Again, using CME, they used the NTLM DA password hash to extract the contents of the entire Active Directory database. This is the database housing all Active Directory objects, including users and their password hashes for the entire domain (that often means every employee at a small company or every employee in a division of a large company).
“Vulnerability scans are excellent point-in-time snapshots of potential problems. But it takes comprehensive penetration testing to demonstrate how easily a malicious hacker can link them together to create a chained attack.”
Tim Semchenko
Owning the Network
Using this DA access, our team created a new backdoor domain administrator account in the Domain Admins group – ample proof for the customer that Raxis had in fact pwned their network.
What else could they have done? Anything they wanted, including staying on the system indefinitely or just logging in periodically to steal data or disrupt operations. Once a hacker has this type of access, it’s very difficult for a company to know if their access has been truly and completely removed.
How is this possible? Because a serious security flaw – one that would not be revealed in full by a vulnerability scan – offered our skilled team members an entry way to take down an entire network had they been bad guys.
The point is that vulnerability scans are excellent at providing a point-in-time snapshot of potential problems on your network. But it takes comprehensive penetration testing to find out just how serious those issues are and to demonstrate how easily a malicious hacker can link them together to create a chained attack.