Cool Tools Series: CeWL for Penetration Testing
Are you performing a password audit for your internal domain or performing an authorized penetration test and need to crack some password hashes? Employees often select predictable passwords containing a root word related to the company or the industry the company operates in.
CeWL (Custom Word List generator) is a tool that helps automate the creation of a custom word list based on web content by pulling out words associated with the company and industry to help populate a custom word list.
Using CeWL
CeWL is a Ruby program that is available on GitHub and also comes installed natively on Kali Linux.
Installation is as simple as ensuring you have Ruby available and following the instructions on the GitHub repository.
In this example, we’ll assume we have the following password hash for a fictional agriculture company:
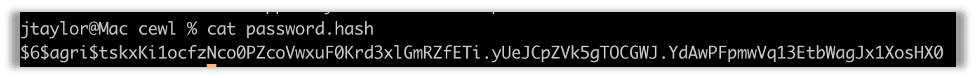
We can try running this through hashcat using the rockyou.txt word list, but this password hash will not be cracked with that word list. We need something more customized.
Here we see the website for our fictional company, agriculture.local.
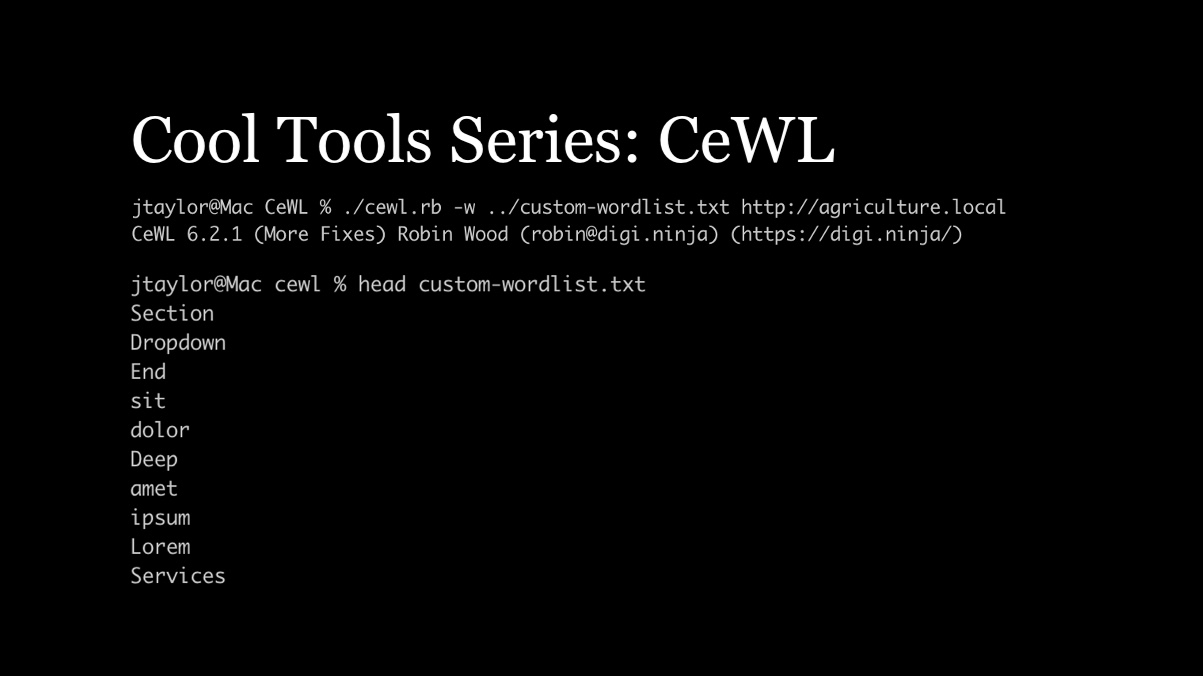
If we point CeWL to this website, it will pull out each word that is used on the website. We can run it by entering this command. Using -w outputs the word list to a file.
./cewl.rb -w custom-wordlist.txt http://agriculture.local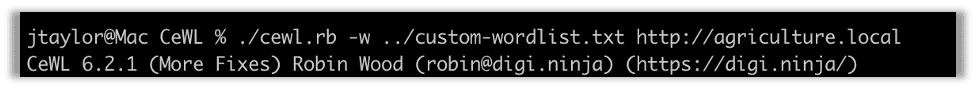
After the tool runs, we can take a look at what it found:
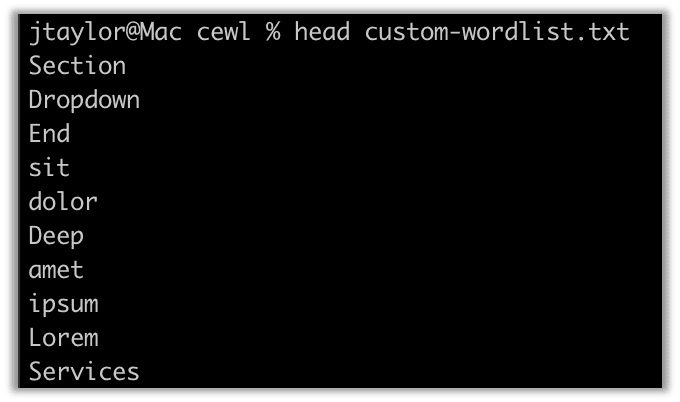
We can run this word list through hashcat using a couple of extra flags to extend the candidate word list using rules. The word list will just be the single words found on the site. It is likely the employees would add a year or special character as well if they used a word from the site as part of their password.
hashcat -m 1800 -r append_year -r append_special.rule password.hash custom-wordlist.txt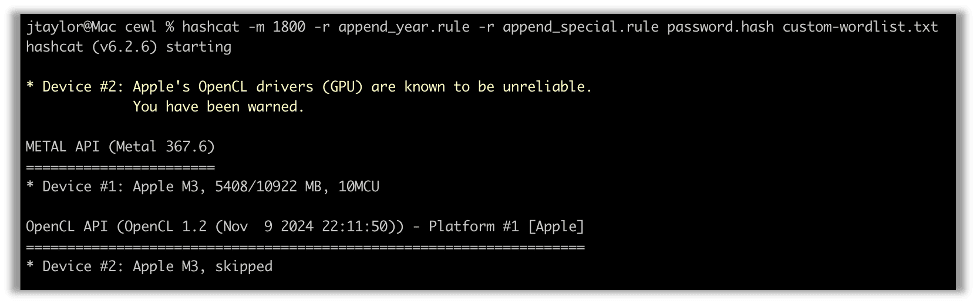
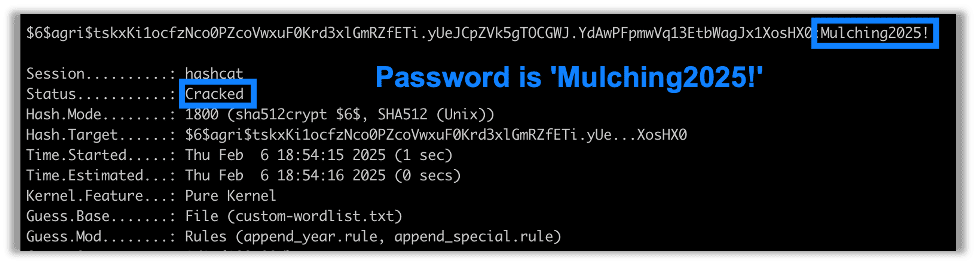
Running hashcat with rules to append the current and previous year as well as a special character, we find that the password is cracked in no time:
Summary
When employees choose a password, it’s often the case that a number of them will use the company name or a phrase based around the company. If there’s a motto or common industry terms, people may also choose those as the base syntax for their passwords.
CeWL can help you generate a custom word list based around a specific company by pulling words from the company’s website. When combining a custom word list from CeWL with a series of rules to modify the password by adding year or special characters, your chances of cracking a password are greatly increased.
Please check back for the next post in the Cool Tools series!