Exploiting GraphQL for Penetration Testing
Exploiting GraphQL, a query language inspired by the structure & functionality of online data storage & collaboration platforms Meta, Instagram & Google Sheets.
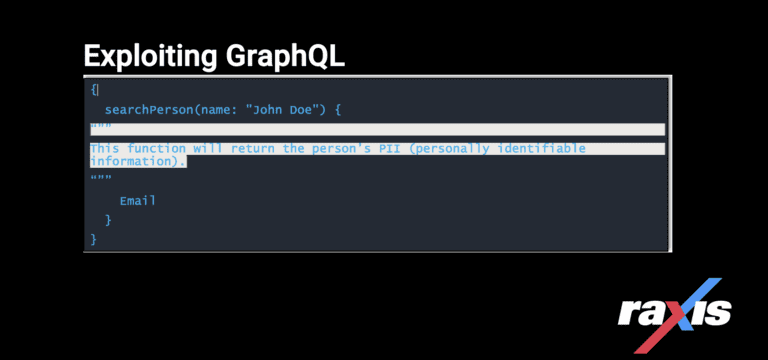
Exploiting GraphQL, a query language inspired by the structure & functionality of online data storage & collaboration platforms Meta, Instagram & Google Sheets.

Raxis demonstrates how to obtain a remote shell on a target system during penetration tests using a Log4j open-source exploit available to all. (CVE-2021-44228)
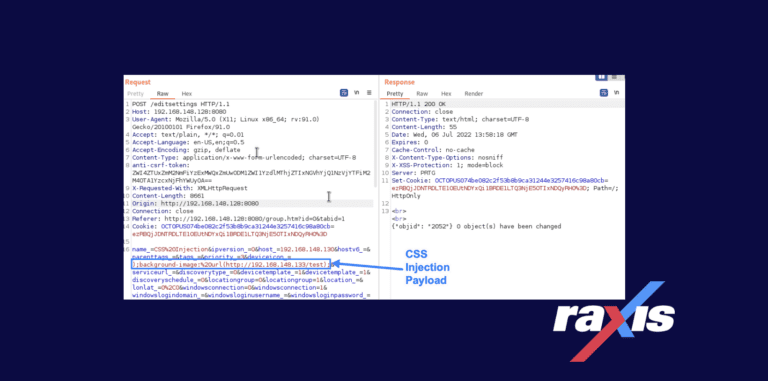
This CSS vulnerability, discovered by Raxis’ Matt Mathur, lies in a device’s properties and how they are verified and displayed within PRTG Network Monitor.

Is the threat of full-scale retaliation enough to prevent large-scale cyberattacks? Raxis’ Bonnie Smyre explains why this Cold War strategy is not effective.

LDAP passback exploits are easy when companies fail to change default passwords on network devices or fail to assign a password at all. If you connect it, you must protect it.