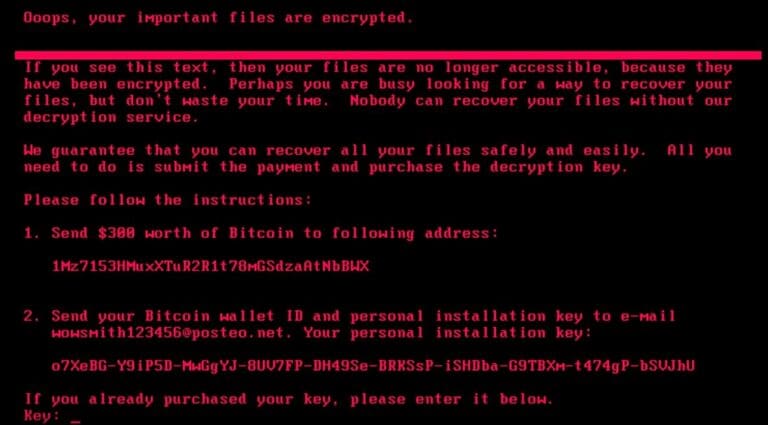
The @ctrl/tinycolor NPM Attack: The Brutal Anatomy of a Cascading Supply Chain Breach
Supply chain security never snoozes, but the recent @ctrl/tinycolor compromise has pushed the boundaries of how we model supply chain threats. Over 40 major packages, including one downloaded millions of times weekly, were exploited in a truly impressive malware campaign that deployed self-propagating, credential-harvesting payloads with the extensibility to spread themselves through ongoing infections.
Breaking Down the Attack Chain
At the heart of this breach was a minified Webpack bundle dubbed “bundle.js.” Executed asynchronously during routine npm installs, this payload identified and targeted Linux and macOS systems with developer credentials. In an interesting departure from convention, it skipped Windows platforms entirely.
- Self-Propagation: Using the NpmModule.updatePackage function, the malware leveraged the NPM API to discover other packages belonging to a compromised maintainer, then auto-published tainted updates. The result was a spiraling web of infected dependencies.
- Credential Harvesting: The worm repurposed open-source tools like TruffleHog and cloud SDKs to scrape secrets from a myriad of sources, including AWS keys, GitHub tokens and ephemeral credentials via process.env, and even cloud secrets via direct API access. AWS, GCP, Azure, and NPM tokens were all fair game.
- Persistent Backdoor: The malware injected a GitHub shai-hulud-workflow.yml Actions workflow, which exfiltrated repository secrets to a remote endpoint on every push. It also created a dedicated branch, named “shai-hulud,” using GitHub’s API, ensuring that the backdoor remained operational until explicitly removed.
- Exfiltration via GitHub: Aggregated credentials and system details were uploaded to newly created public GitHub repositories, also named “Shai-Hulud”. This novel exfiltration technique blended in with normal developer activity, forestalling detection while ensuring the exfiltrated data was readily accessible to attackers.
Evading Detection: Silent, Modular, and Fast
Unlike many prior NPM compromises, Shai-Hulud operated with the stealth of an assassin. Errors were snuffed through silent failure, and TruffleHog executions masqueraded as legitimate security scans. No logs, no noise, just the business of direct exfiltration and propagation.Stuxnet much?
StepSecurity’s Harden-Runner flagged these anomalous npm install behaviors by tracking unauthorized outbound API calls, file modifications, and suspicious process executions, a solid testimonial for runtime detection and proactive monitoring at every supply chain node.
Identifying and Remediating Compromised Assets
The result is a proper hot mess, and the fallout from this incident means every organization with affected packages should take immediate action:
- Inventory and Remove: Run npm ls @ctrl/tinycolor to check dependencies. Uninstall all compromised packages and scan for malicious bundle.js via its SHA-256 hash (46faab8ab153fae6e80e7cca38eab363075bb524edd79e42269217a083628f09).
- Clean Repos: Remove .github/workflows/shai-hulud-workflow.yml, audit for a shai-hulud branch, and delete any malicious repository artifacts.
- Rotate All Credentials: Change all NPM, cloud, GitHub, and CI/CD tokens and secrets, as the malware is comprehensive in its harvesting.
- Cloud Audit: Inspect AWS CloudTrail and GCP logs for unusual secret access activity; investigate batch secret operations and unauthorized key generation.
Recovery Tooling and Hardening Tips
So, what now? Tools like StepSecurity Harden-Runner, Artifact Monitor, and Threat Center provide runtime detection, supply chain release monitoring, and rapid identification of dangerous dependency changes. Implement NPM cooldown periods to block too-fresh dependency upgrades and ensure secret scanning alerts are enabled across GitHub repositories.
Takeaway: What This Attack Means for Developers
The Shai-Hulud incident all but blows up traditional threat modeling for package ecosystems:
- Self-propagating malware can breach not just projects but maintainers’ entire portfolios.
- Credential theft now directly targets CI/CD, cloud, and code infrastructure, conveniently often in a single install.
- Blending exfiltration with routine developer workflows bypasses many legacy detection strategies.
The classic mantra of embracing defense-in-depth still resonates, which includes runtime anomaly detection, rapid dependency checks, secrets management, and regular credential rotation. The age of AI is upon us, and the level of sophistication in attacks continues to increase geometrically. Rest assured; the next one is already in the works.