Wireless Series: The Aircrack-ng Suite for All Your Wireless Pentesting Needs
Principal Penetration Tester Scottie Cole continues our wireless series with the Aircrack-ng Suite, a set of tools for wireless pentest discovery and exploits.
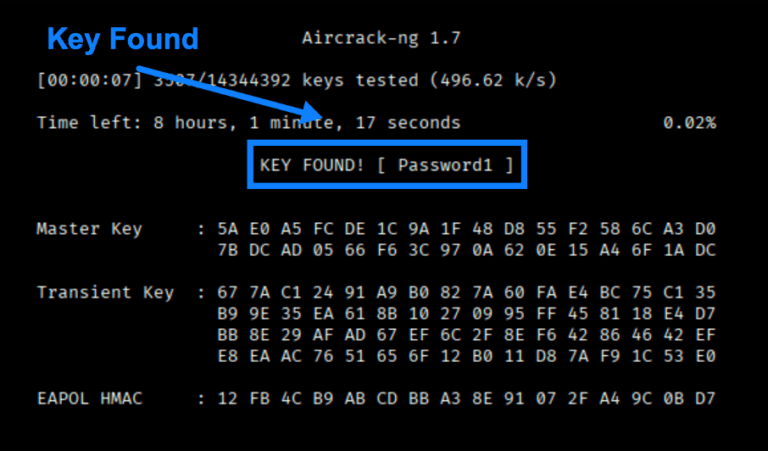
Principal Penetration Tester Scottie Cole continues our wireless series with the Aircrack-ng Suite, a set of tools for wireless pentest discovery and exploits.
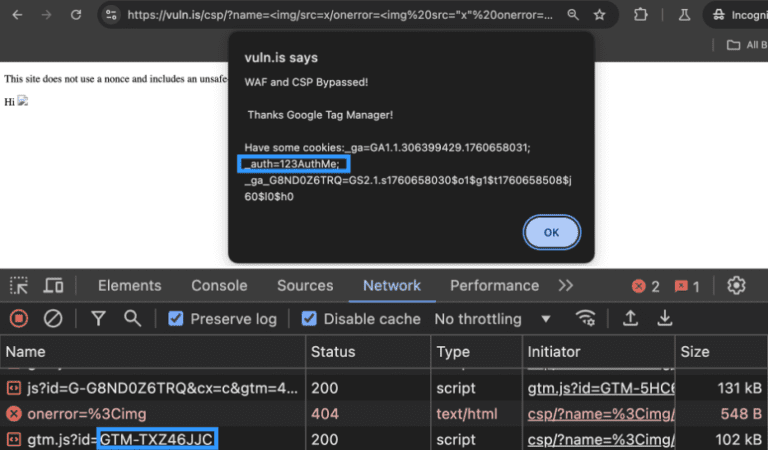
Ryan Chaplin takes an in-depth look at how attackers can use unsafe directives to bypass CSP, notably in Google Tag Manager, and how to remediate the issue.

Lead Penetration Tester Nathan Anderson is back with more PSE and red team tips, including tailgating, impersonating, and pretexts to gain onsite access.

Raxis’ Jason Taylor is back with a detailed tutorial on performing both manual and automated DNS exfiltration attacks for pentesting.

We reached into our vaults to bring you the final video in our cross-site scripting (XSS) series. Learn about cookie theft, website defacement, and CSRF attacks.