The Role of AI in Penetration Testing
Bonnie Smyre shows how Raxis’ AI-augmented pentesting gives their expert pentesters more time for complex chained attacks and discovery of business-logic flaws.

Bonnie Smyre shows how Raxis’ AI-augmented pentesting gives their expert pentesters more time for complex chained attacks and discovery of business-logic flaws.

Brian Tant takes a look at WPA3. While offering much deeper security than WPA2, it is still vulnerable to transition Mode and side-channel attacks.

Raxis’ Tim Semchenko explains why we can’t lower risk ratings for your penetration test findings just because you ask and why that’s a good thing.
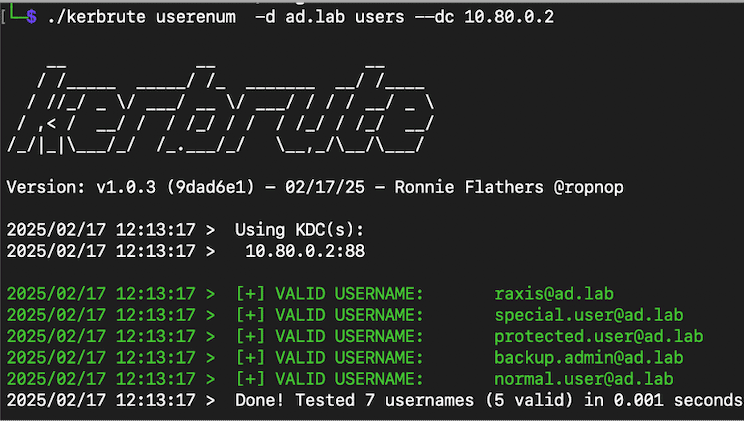
Raxis Principal Penetration Tester Andrew Trexler walks through the many uses of Kerbrute from user enumeration to brute-forcing and password spraying.

Raxis Senior Penetration Tester Nate Jernigan discusses lateral movement in penetration testing and the methods and tools he uses when performing these attacks.