OWASP Top 10 for 2025: What’s New in Web Application Security
Web application security continues to dominate conversations in cybersecurity and for good reasons. As web applications grow in scope and complexity, vulnerabilities become increasingly difficult to manage, making this a persistent challenge for organizations everywhere.
The Open Web Application Security Project (OWASP) remains the industry leader in identifying and classifying these threats. Their newly released OWASP Top 10 for 2025 replaces the 2021 list, bringing with it a mix of re-ranked, redefined, and newly introduced risks.
In this post, we’ll break down what’s changed, what stayed familiar, and how your teams can start preparing for the next evolution of application security and the risks on the horizon for 2026.
What Has Changed?
OWASP’s latest update refines and reshuffles the risk categories to reflect the modern web ecosystem. While some long-standing issues persist, others have broadened to capture new supply-chain and configuration-driven challenges. Here’s a quick overview:
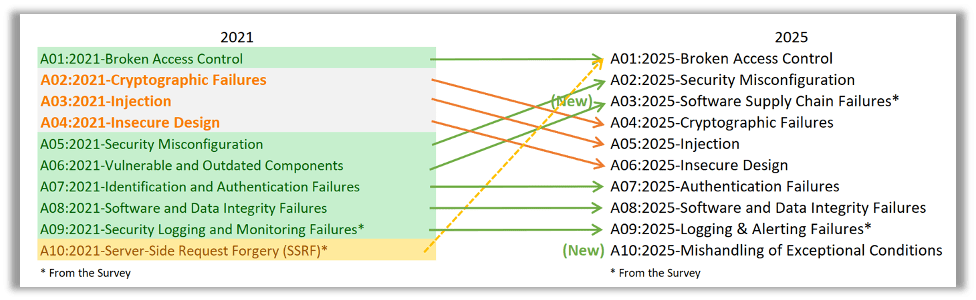
A01:2025 – Broken Access Control
Still the number one threat. It continues to be the most prevalent and dangerous issue across modern applications.
A02:2025 – Security Misconfiguration
Previously fifth, now takes second place due to the explosion of configuration-driven vulnerabilities in cloud and containerized environments.
A03:2025 – Software Supply Chain Failures
Formerly “Vulnerable and Outdated Components,” this expanded category has moved up in the list and now covers the entire software supply chain dependencies, build systems, and distribution infrastructure.
A04:2025 – Cryptographic Failures
Dropping slightly in rank, this category still highlights the ongoing risks of weak or broken encryption and exposure of sensitive data.
A05:2025 – Injection
Once in third, injection flaws remain widespread, with SQL, NoSQL, and command injections still driving a large portion of reported CVEs.
A06:2025 – Insecure Design
Insecure design moves down from the fourth position as threat modeling and an emphasis on secure design have led to improvements in this risk over the last four years.
A07:2025 – Authentication Failures
Previously “Identification and Authentication Failures.” Modern authentication frameworks have reduced these risks, but they remain a consistent area of concern.
A08:2025 – Software or Data Integrity Failures
Unchanged from 2021, this continues to cover failures in verifying software and data integrity across deployment pipelines.
A09:2025 – Logging and Alerting Failures
Slightly renamed from “Security Logging and Monitoring Failures” to emphasize the importance of real-time alerting and incident response readiness, this category also remains in the same position as the 2021 list.
A10:2025 – Mishandling of Exceptional Conditions
A new category that replaces “Server-Side Request Forgery (SSRF).” It focuses on improper error handling, logic flaws, and unexpected application behavior.
What Should Your Organization Do Next?
Now is the perfect time to review your organization’s web application risk posture. Conduct a new risk assessment to determine which of these updated vulnerabilities apply to your systems and partner with your development and security teams to implement proactive controls.
Raxis offers a number of options to help organizations keep web applications aligned with the OWASP Top 10. Our expert team can identify and exploit real-world vulnerabilities in your applications before attackers do. Add Raxis Attack PTaaS to your DevSecOps processes for continual testing of your applications or choose a traditional Raxis Strike penetration test to verify your controls annually and after major updates.