Password Series: Defeating Emerging Password Security Trends with Psudohash for Penetration Testing
Changes in Authentication
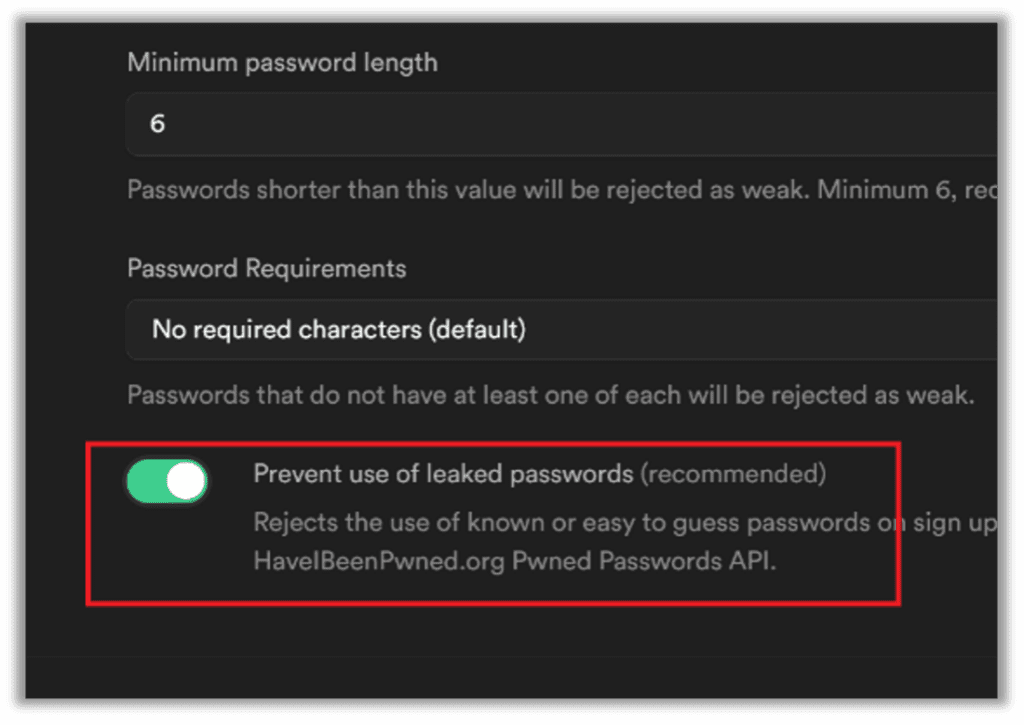
One interesting trend emerging among developers, which could impact the methodologies required when attempting to crack a hash, is Have I Been Pwned’s database of leaked credentials and the corresponding API that has made it easier than ever for developers to check for leaked credentials while users sign up.
An example of this can be seen with Supabase, a leading open-source alternative to Firebase. Supabase incorporates a check for leaked credentials by default, automatically opted-in, with no additional plugins or developer time needed. A simple toggle in an administrative interface allows developers to automatically check each of their clients’ credentials against leaked passwords and prevents clients from using known leaked credentials.
As more developers incorporate either this API or a similar one, it could eventually discourage password reuse, reducing the effectiveness of several wordlists. Traditional attacks should still work, even if the majority of organizations adopt these methods, because many people will just modify their original password slightly, making rule and mask attacks even more important for catching minor variations of the same original password. It will also make tools that are used to make supplemental lists even more important.
Supplementing wordlists using tools like CeWL, crunch, or CUPP, is a key part of every penetration tester’s repertoire. This category is where one of my favorite new tools for password dictionary attacks appeared just two years ago.
Psudohash is great for those times when you want to create tons of permutations of something common, such as the business name or the product name that you are testing. It will create hundreds of millions or even billions of permutations of the same word.
Basic Psudohash Usage
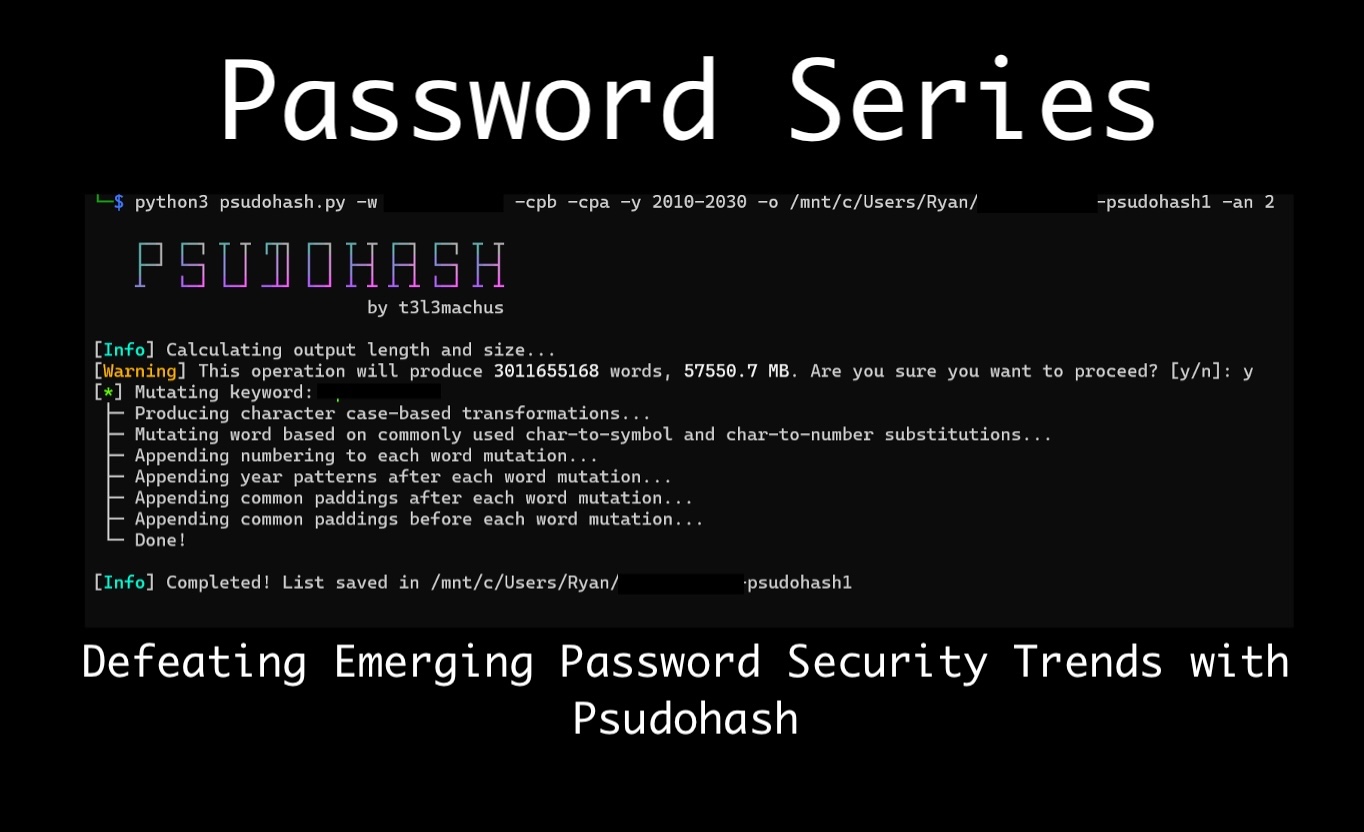
The command below shows some of the options available where -cpb -cpa adds common paddings before and after. This list of common paddings by default is a list of 108 characters such as !!! or 123 that it will add to either side of the word if given the cpb or cpa argument. It can be modified to include whatever common paddings one chooses.
python3 psudohash.py -w -cpb -cpa -o /mnt/c/Users/Ryan/ -psudohash -an 2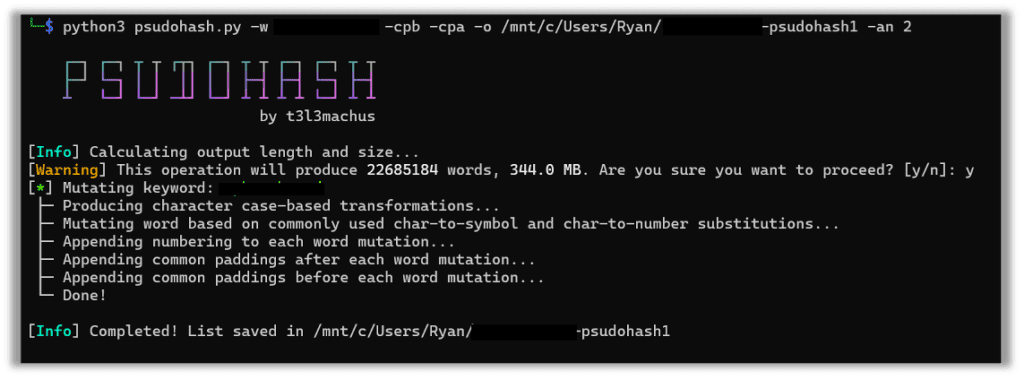
One thing to keep an eye on while using this tool is the size of the operation you are performing. I simply added years and common paddings -y 2010-2030 -cpb cpa, and, as a result, it will take over 50,000MB. This can produce output that challenges even the most contemporary password cracking rig, especially if additional permutations are applied while cracking.
python3 psudohash.py -w -cpb -cpa -y 2010-2030 -o /mnt/c/Users/Ryan/ -psudohash -an 2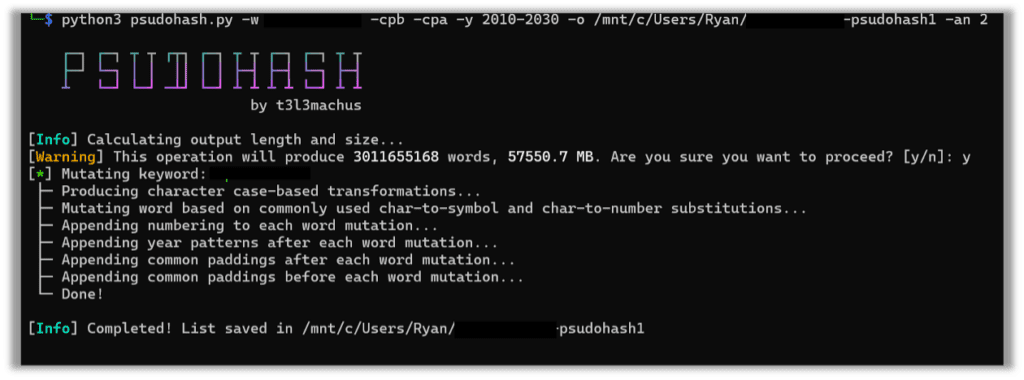
Of course, there are numerous options available, and transformations can be as simple as character transformations such as a = @. Here I pass the tool multiple words to transform:
./ psudohash.py -w ‘david,maria,lassie,metallica’ –common-paddings-after –common-paddings-before -y 1990,2022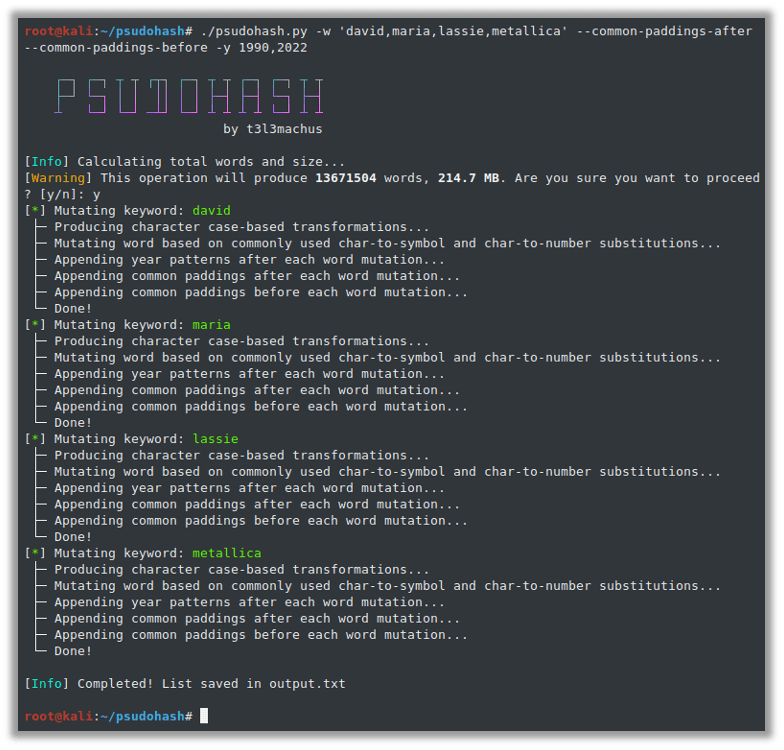
However, it is only good at creating permutations of words you pass to it. This makes it a great supplemental tool for your cracking efforts, but it should remain supplemental. I personally always pass company and product names to this when I have a hash that I am trying to crack for a penetration test.
./psudohash.py -w Microsoft –common-paddings-after -y 2020-2023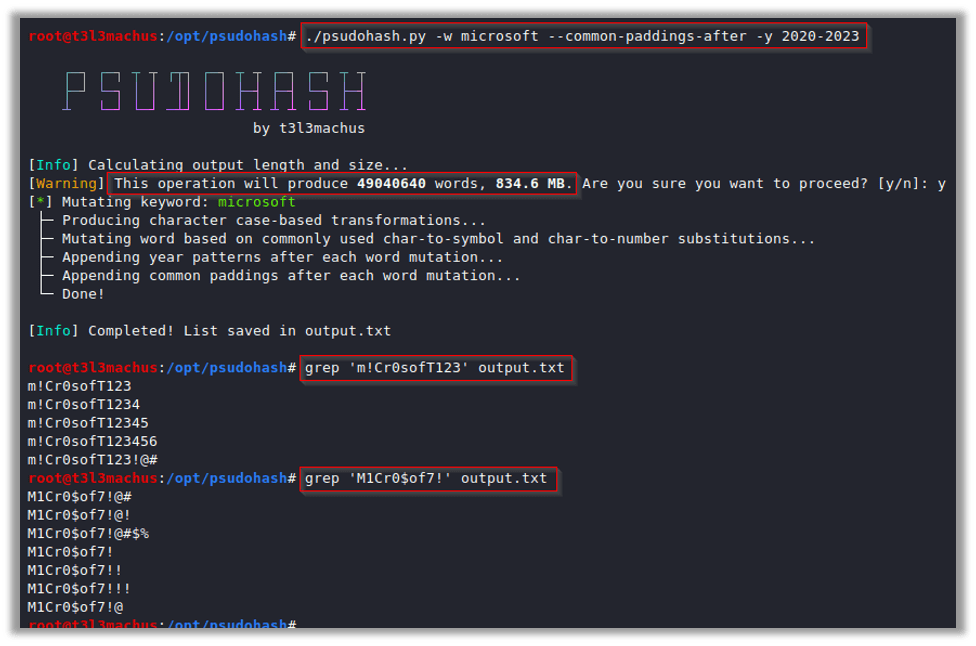
Up Next
This tool has helped me establish some major wins. In my next posts in this series, I will share how this tool has inadvertently helped me, not only to stay ahead of changes like this with Supabase, but also to identify biases in some of our datasets. I will provide an example of how this tool can not only fill in the gaps but also illustrate common gaps that many security professionals make when cracking passwords.
Take a look at a detour password series post I wrote as well: Password Series: 8 Practical First Steps To Crack Difficult Passwords