“Give a pentester a table, they submit one report. Automate making tables, they can submit reports for life.”
k0pak4
Displaying findings clearly and concisely is key to making a penetration testing report actionable. The proof of concept allows a client to replicate the finding, and a list of affected targets allows them to properly remediate all assets. On large engagements, there are often findings that affect many hosts; when presented concisely, this can be acted on much more easily. There are already amazing tools out there to scan many hosts and report their findings. (Nessus, Nexpose, and Nmap are examples.) The problem is that none were doing what I was looking for — reporting the affected hosts for one finding, concisely.
The first two tools described here quickly create tables showcasing the details behind two common findings on large external pentest reports. Clients can also use these tools to verify remediations without having to manually inspect each host. The last tool can be used to turn any list into a sorted table, which works well when you simply need a large table to display many hosts.
mass-sslscan (https://github.com/k0pak4/mass-sslscan)
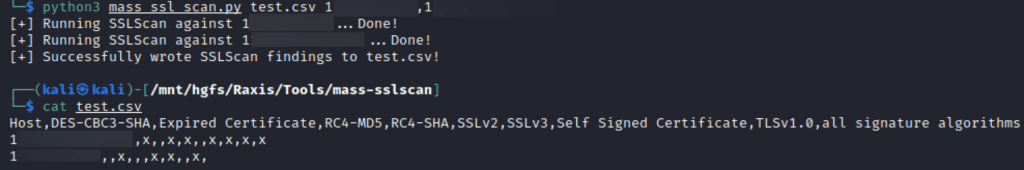
There are several tools that will break down the weak SSL/TLS protocol versions, ciphers, and signature algorithms used in TLS connections. Some of these are web-based, such as SSL Labs, and others are command-line based, such as the SSLScan tool. My mass-sslscan tool runs SSLScan against an entire list of hosts, parses the output of the tool, and creates a table with each host that displays which weak configuration(s) they have. This can also be used in remediation to ensure those servers have had their configurations strengthened. An example of running the tool is shown below:
server-header-scan (https://github.com/k0pak4/server-header-scan)
On penetration tests, it’s common to find the HTTP server header, which can disclose the web server’s software and sometimes its exact version. This information leakage is typically of low severity, but helps an attacker fingerprint the server, which may disclose a vulnerable version. In more targeted attacks, it might tell them what software to build an exploit for. My tool, server-header-scan, retrieves the server header from each target, and inserts the results into a table with each retrieved value, as shown in the following example:
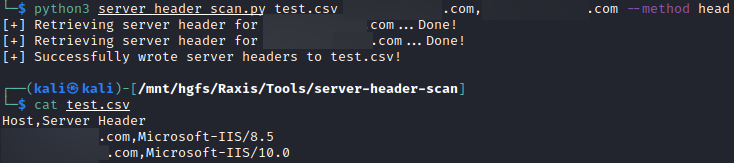
table-maker (https://github.com/k0pak4/table-maker)
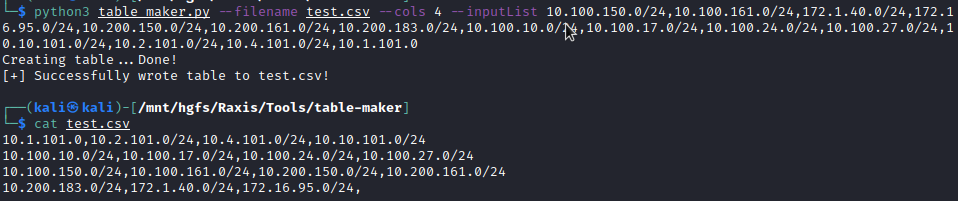
The table-maker is a bit more straightforward. It takes a list, either as a comma-separated list or as a file with one item per line, and turns it into a table with the desired number of columns. This can be useful for extremely large scopes or when discovering many hosts are vulnerable to a specific finding. This results in a csv ready to be opened and pasted as a table, as shown in the illustration below:
If you compile reports for large penetration tests, odds are that you’re going to be pressed for time at some point. My hope is that these tools will make it easier for you to provide more and better information to your customers in a way that helps them understand and act on your findings.