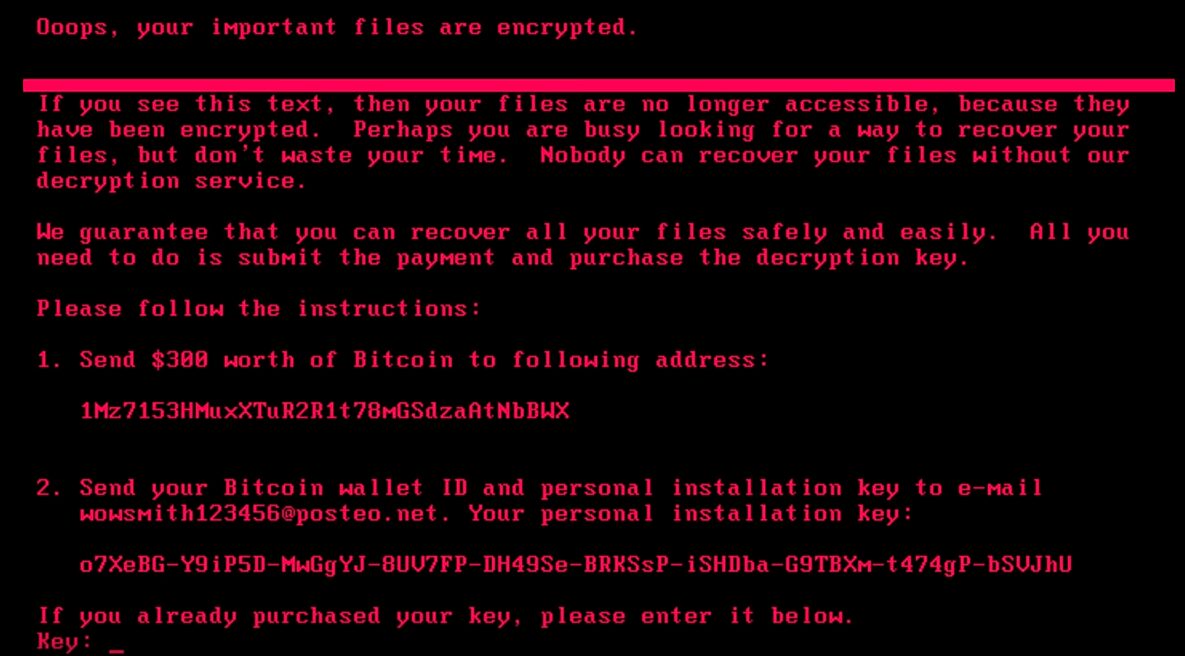
Petya, the next major security malware since Wannacry is specifically targeting companies across the globe. Originating from the Ukraine, the Petya ransomware uses the same Eternalblue/MS17-010 vulnerability that was used with Wannacry. The difference this time is there is no kill switch that we know of. It’s getting some significant traction, infecting systems everywhere. In the US, it’s hit a major pharmaceuticals company and a food services company. Petya has also hit Danish, French, and Russian companies.Similar to Wannacry, the malware virus is encrypting systems and demanding a ransom to get access to the data. Our research has not found a way to bypass this ransom at this time. Fortunately, it seems that working decryption keys are being provided once paid.
It’s not just ransomware
Unfortunately, there’s much more to this variant. Once the ransomware gains a foothold, it has worm capabilities and is breaching other systems using a variety of exploitation methods. It appears to be focused on critical infrastructure across the world, but is not limiting devices it infects by any means. Various news sources have reported that power plants in the US and other countries have been breached. If this turns out to be a successful attack, it is quite scary to think about the damage that could occur.For those who don’t remember, you can thank the NSA for this. The NSA had developed a tool that could breach Windows systems remotely using an exploit that was previously undisclosed. The Shadow Brokers hacker group obtained the source to the NSA tool and leaked it on April 14, 2017.
Stop PETYA with a penetration test
When it comes to ransomware, we haven’t found a good way to retroactively deal with the damage. Even once the ransom is paid, it is very likely that the attackers will return again in the future. Particularly if they know that they’ve received payment in the past. The only real way to defend against Petya is to eliminate the vulnerability from the beginning, and a penetration test from a trusted third party might be the only real way to know you’re protected. Petya (and Wannacry) uses the Eternalblue vulnerability in SMB, fixed by MS17-010. Systems are still falling victim, even when the organization has a patch management program. Mistakes with configuring the vulnerability scanning tool, or unknown systems to the patch management tool will cause a few systems to remain vulnerable and outside of the view of the security administrators. A penetration test can find these gaps in process before malware can exploit these systems. In addition, the penetration test will attempt to exploit any issues found as a proof of concept – providing you and your security organization proof that a potentially significant security event was avoided. Schedule a penetration test with Raxis before the next malware variant hits.