Year: 2024
1-10 of 212 results
-
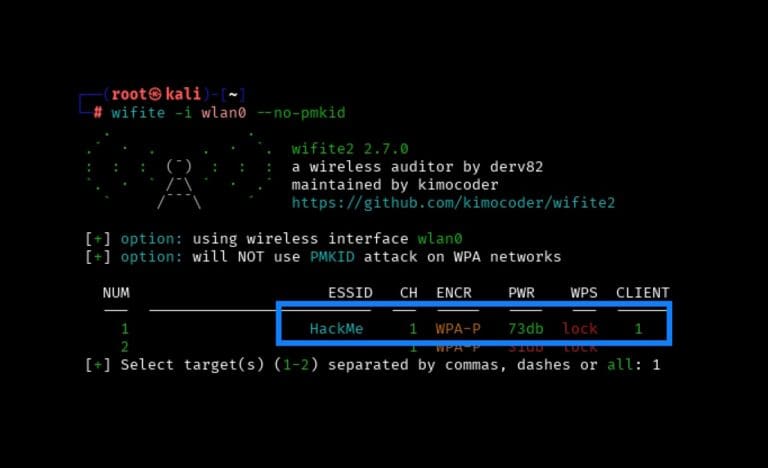
Wireless Series: Using Wifite to Capture and Crack a WPA2 Pre-Shared Key for Penetration Testing
By Scottie Cole • June 17, 2025 -
Jailbreak Journey: Transforming an iPad for Mobile App Penetration Testing
By Jason Taylor • June 3, 2025 -
-
Cisco Releases Patch for CVE-2025-20188 – 10.0 CVSS
By Scottie Cole • May 8, 2025 -
How AI Makes Phishing Easy & What to Watch For
By Andrew Trexler • May 6, 2025 -
Choosing a Penetration Testing Company: Part 1
By Cole Stafford • April 22, 2025 -
PSE & Red Team Series: Physical Entry Bypass
By Nathan Anderson • April 8, 2025 -
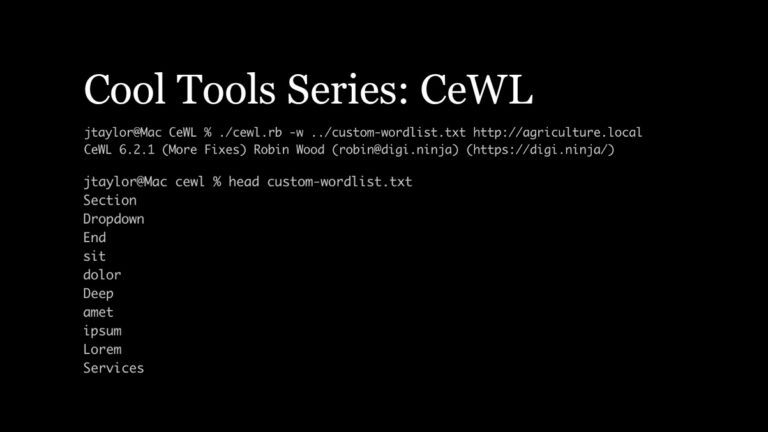
Cool Tools Series: CeWL for Penetration Testing
By Jason Taylor • March 25, 2025 -
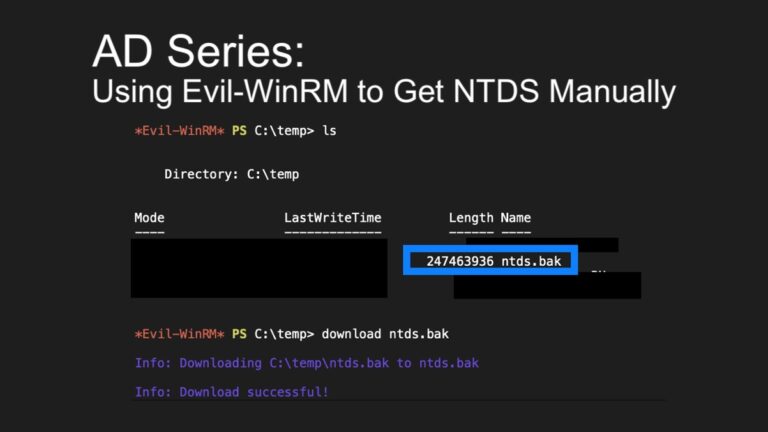
AD Series: Using Evil-WinRM to Get NTDS Manually in Penetration Tests
By Andrew Trexler • March 11, 2025 -
Understanding PTaaS: Penetration Testing as a Service
By Bonnie Smyre • March 5, 2025
- Careers
- Exploits
- How To
- In The News
- Injection Attacks
- Just For Fun
- Meet The Team
- Mobile Apps
- Networks
- Password Cracking
- Penetration Testing
- Phishing
- PTaaS
- Raxis In The Community
- Red Team
- Security Recommendations
- Social Engineering
- Tips For Everyone
- Unsupported Software Unpatched Systems
- Web Apps
- What People Are Saying
- Wireless