AttackTek: How to Launch a Broadcast Resolution Poisoning and SMB Relay Attack
Welcome to our first AttackTek installment, where we’ll go deeper into the tech side of our penetration testing. We’re going to start with a couple of the easiest and most consistent ways we’ve found to get inside corporate networks and gain domain admin rights – sometimes before we finish our coffee on Day 1.
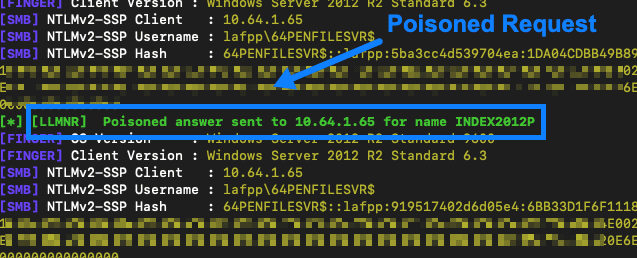
The first is broadcast name resolution poisoning, known more simply as the broadcast poisoning attack. The second, which we often use in tandem, is the SMB relay attack.
For those unfamiliar with these attacks, a broadcast poisoning attack targets users’ credentials as a means to further access corporate networks and data. An SMB relay attack is basically a man-in-the-middle attack in which the malicious actor tries to make the target machine believe that it is the authenticating server.
These two attack methods work really well together and can be put into motion in a matter of minutes.
In this video, I will walk you through an entire attack chain and break down both of these attacks as I’m conducting them.
Just a friendly heads-up: A lot of the ‘action’ in this video is code on a screen. If you’re a pen tester or a defender, you’ll probably find it very interesting. But if you’re a non-techie and you clicked here after watching your favorite surf video, well . . . enjoy!
At Raxis, we offer a variety of penetration tests to help you and your company identify vulnerabilities and close the gaps before a cybercriminal finds them. During these tests our team of experienced, professional hackers use every trick in the book – plus some they make up on the fly – to get past your security.
If you are ready to explore more penetration testing and assessment options with Raxis, be sure to visit our contact page.