Why 8-Character Passwords Are No Longer Enough: Lessons from the Raxis Password Cracker
With the start of 2026, the Raxis team is already busy. A new upgrade to our password-cracking system shows how quickly 8-character passwords can be cracked.

With the start of 2026, the Raxis team is already busy. A new upgrade to our password-cracking system shows how quickly 8-character passwords can be cracked.

We reached into our vaults to bring you the final video in our cross-site scripting (XSS) series. Learn about cookie theft, website defacement, and CSRF attacks.

Raxis Lead Penetration Tester Jason Taylor’s in-depth tutorial explains setting up a server for DNS exfiltration. Check back next month to run the attack.

The FBI has released information to help organizations that are affected by recent attacks against Salesforce. Raxis’ Jason Taylor sums up next steps here.
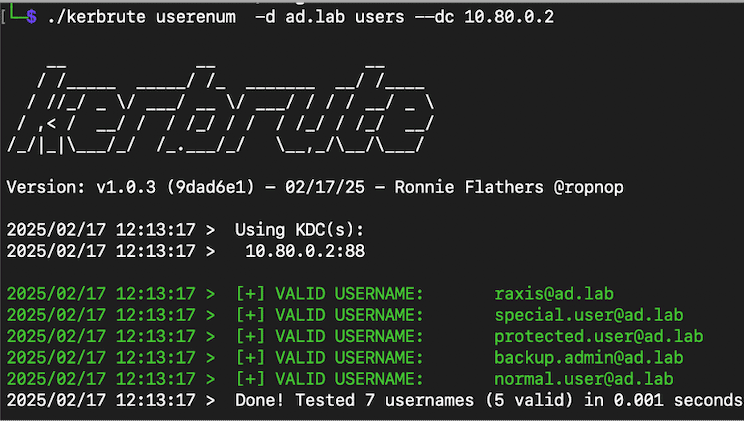
Raxis Principal Penetration Tester Andrew Trexler walks through the many uses of Kerbrute from user enumeration to brute-forcing and password spraying.